This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Front Range OWASP Conference 2013"
Mark Major (talk | contribs) |
Mark Major (talk | contribs) m |
||
| Line 21: | Line 21: | ||
=Event Sponsors= | =Event Sponsors= | ||
{{:Front_Range_OWASP_Conference_2013/Sponsors}} | {{:Front_Range_OWASP_Conference_2013/Sponsors}} | ||
| − | + | <!-- | |
=Continuing Education Credit= | =Continuing Education Credit= | ||
{{:Front_Range_OWASP_Conference_2013/Continuing_Education}} | {{:Front_Range_OWASP_Conference_2013/Continuing_Education}} | ||
| − | + | --> | |
=Hotel and Travel= | =Hotel and Travel= | ||
{{:Front_Range_OWASP_Conference_2013/Travel}} | {{:Front_Range_OWASP_Conference_2013/Travel}} | ||
Revision as of 21:57, 1 March 2013
- Introduction
- Registration
- Venue
- Conference Schedule
- Event Sponsors
- Hotel and Travel
- Presentation Materials
Welcome to SnowFROC 2013 - the 5th Annual Front Range OWASP Security Conference
The Colorado OWASP chapters are proud to present the 5th annual SnowFROC. Join 300 other developers, business owners, and security professionals for a day-and-a-half of presentations, training, and Birds-of-a-Feather (BoaF) sessions. The SnowFROC 2013 keynote speaker is Neal Ziring, Technical Director of InfoProtection at NSA.
The conference will occur on Thursday, March 28th at the Denver Marriott City Center and will feature four primary tracks:
- High-Level Technical
- Deep-Dive / Hands-on Technical
- Management
- Legal
Running in parallel to the conference proceedings will be a capture the flag (CTF) hacking competition developed exclusively for SnowFROC by Boulder OWASP chapter members. The day will conclude with a moderated panel discussion featuring top industry leaders.
On Friday, March 29, Aaron Weaver will teach a course in secure coding. This training is free to SnowFROC attendees!
Friday will also offer BoaF sessions. Join like-minded industry leaders and discuss pressing issues facing the industry and you. BoaF sessions are self-lead and may address and issue you would like. Pitch your idea and get the ball rolling!
Finally, Friday will feature a postmortem of the CTF tournament. In addition to discussing solutions, techniques, and tools, we will encourage participants to attack the previously out-of-bounds CTF framework. Itching to break into the scoreboard and rack up the points? The gloves come off Friday morning.
Conference Committee
Mark Major: Director
Brad Carvalho: Sponsorship, Executive events
Craig Klosterman: Merchandise
Steve Kosten: Sponsorship, Executive events
Glen Matthes: Planning
Chris Rossi: CTF, Networking events
Greg Foss: CTF
Colorado Chapter Hosts
OWASP Boulder chapter: Mark Major
OWASP Denver chapter: Steve Kosten, Brad Carvalho (acting)
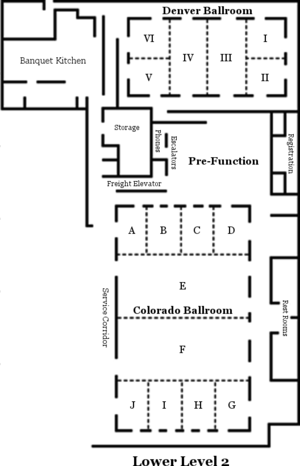
Conference Location
|
SnowFROC 2013 Schedule
Current Sponsors
Aerstone
| Aerstone provides strategic and technical cyber security consulting services including assessments, planning, architecture designed incident response, regulatory compliance, and computer forensics. We provide services and products for medium to large healthcare providers, financial services organizations and legal firms, and law enforcement. Clients range from local businesses to government agencies. |
Applied Trust
| AppliedTrust provides IT infrastructure, security, and opensource consulting services. Our clients are organizations where effective IT is critical to the reputation and growth of their business, and hail from a variety of industries including healthcare, financial services, hospitality, recreation, and government. Our specialty areas include:
|
Checkmarx
| Checkmarx - Source Code Analysis Made Easy
Checkmarx is the developer of next generation Static Code Analysis (SCA) solutions. The company pioneered the concept of a query language-based solution for identifying technical and logical code vulnerabilities. Checkmarx provides the best way for organizations to introduce security into their Software Development Lifecycle (SDLC) which systematically eliminates software risk. The product enables developers and auditors to easily scan un-compiled / un-built code in all major coding languages anywhere, anytime. CxSuite's application security testing is available in both "On Premise" and "On Demand" configurations. The security testing scans for the most prevalent security vulnerabilities as determined by OWASP Top 10, SANS, and other major standards. Checkmarx was recognized by Gartner as sole visionary in their latest SAST magic quadrant and as Cool vendor in application security. Customers include Fortune 500, government organizations and SMBs in over 30 countries. |
HP
| HP is a leading provider of security and compliance solutions for the modern enterprise that wants to mitigate risk in its hybrid environment and defend against advanced threats. Based on market leading products from HP ArcSight, HP Fortify, and HP TippingPoint, the HP Security Intelligence Platform uniquely delivers the advanced correlation, application protection, and network defenses to protect today’s hybrid IT infrastructure from sophisticated cyber threats. |
Security Pursuit
| Security Pursuit provides computer security services to help organizations protect their critical information systems. Based in Denver, Colorado, Security Pursuit's services include: IT Security Risk Analysis, Data Breach Incident Response, Network Penetration Testing and Vulnerability Assessments, Website Penetration Testing and Vulnerability Assessments, Wireless Network Security, Social Engineering Prevention, Security Awareness Training, Employee Termination Assistance and Virtual CISO consulting. We have conducted hundreds of security assessments for financial institutions, healthcare providers, retailers, utilities, airports, and municipal governments; many in support of PCI, GLBA, NCUA, and HIPAA compliance requirements. Security Pursuit’s computer security services provide you with a higher level of awareness about the security posture of your organization. |
SouthSeas
| Escaping network insecurity means identifying and eliminating vulnerability at each and every level. At South Seas Corporation, we consider the big picture and the finest details of your information technology, from computers to routers to servers and the cabling between, from intranets to the internet, from mobile devices to web applications to remote networks across the globe. We also address administrative issues, including security policy and federal compliance. Of course, your budget is top of mind from the beginning. The end result is a tailored solution designed to secure every byte of information traveling through, to and around your organization at every point, installed by certified experts trained to work hand in hand with your IT department. Take a load off your mind with South Seas Corporation. |
Veracode
| Today most global enterprises live under the constant threat of being hacked, which begs this critical question – how do they innovate and rapidly release new and improved applications required to be an industry leader while still securing their organizations critical IP and data assets? Before Veracode, application security was widely thought to slow innovation, but not anymore. With the Veracode Platform, application security and innovation can go hand-in-hand. Whether applications are built, brought or outsourced, Veracode’s patented testing technology provides the intelligence needed to quickly secure them from the most common forms of attack. |
Denver Marriott City Center
|
Denver Attractions
- Monty Python's Spamalot at the Buell Theatre (3/28-30)
- World-class exhibitions at the Denver Art Museum
- Guided walking tours of downtown's microbreweries
- The Denver Nuggets host the Brooklyn Nets (3/29 @ 7pm)
- Free tours of the US Mint
- Plus all the standard downtown stuff: shopping, more shopping, an aquarium, a zoo, comedy clubs, local music, and many clubs, restaurants, and art galleries.
Colorado Attractions
Out-of-town visitors may be interested in staying for the weekend to enjoy all Colorado has to offer, including:
- Red Rocks amphitheatre
- The Butterfly Pavilion
- Garden of the Gods (Colorado Springs)
- Royal Gorge (Canyon City)
- Coors, New Belgium, and many other Colorado breweries
Skiing
The SnowFROC staff is pursuing a chartered bus and negotiated discounts for premier ski resorts and lift tickets. Check back soon for details!
2013 presentations
Keynote Address: Data Protection for the 21st Century
Panel Discussion
Technical Track
DevFu: The inner ninja in every application developer
Adventures in Large Scale HTTP Header Abuse
Angry Cars: Hacking the "Car as Platform"
DevOps and Security: It's Happening. Right Now.
Real World Cloud Application Security
Deep-Dive Track
SIP Based Cloud Instances
How Malware Attacks Web Applications
Top Ten Web Application Defenses
A Demo of and Preventing XSS in .NET Applications
Data Mining a Mountain of Zero-Day Vulnerabilities
Management Track
Digital Bounty Hunters - Decoding Bug Bounty Programs
Linking Security to Business Value in the Customer Service Industry
Using SaaS and the Cloud to Secure the SDLC
Measuring Security Best Practices With Open SAMM
Defending Desktop (.NET/C#) Applications: Mitigating in the Dark (A Case Study Remix)
Legal Track
Electronic Discovery for System Administrators
Legal Issues of Forensics in the Cloud
CISPA: Why Privacy Advocates Hate This Legislation
Crafting a Plan for When Security Fails
Information Control: The Critical Need for a Defensible Position - Securing the Information Ecosystem
Previous conferences
2012 presentations are available here.