This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Front Range OWASP Conference 2013"
Mark Major (talk | contribs) (Lots of content updates as well as a format change to use the recommended (tab-based) layout.) |
Mark Major (talk | contribs) |
||
| Line 3: | Line 3: | ||
__NOTOC__ | __NOTOC__ | ||
| + | <font size=2pt> | ||
= Introduction = | = Introduction = | ||
| − | + | {{:Front_Range_OWASP_Conference_2013/Introduction}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
=CFP= | =CFP= | ||
| − | + | {{:Front_Range_OWASP_Conference_2013/CFP}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
=Registration= | =Registration= | ||
| − | + | {{:Front_Range_OWASP_Conference_2013/Registration}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
=Venue= | =Venue= | ||
| − | + | {{:Front_Range_OWASP_Conference_2013/Venue}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
=Conference Schedule= | =Conference Schedule= | ||
| − | + | {{:Front_Range_OWASP_Conference_2013/Schedule}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | { | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
=Event Sponsors= | =Event Sponsors= | ||
| − | + | {{:Front_Range_OWASP_Conference_2013/Sponsors}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
=Continuing Education Credit= | =Continuing Education Credit= | ||
| − | + | {{:Front_Range_OWASP_Conference_2013/Continuing_Education}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
=Hotel and Travel= | =Hotel and Travel= | ||
| + | {{:Front_Range_OWASP_Conference_2013/Travel}} | ||
| − | == | + | =Presentation Materials= |
| − | + | {{:Front_Range_OWASP_Conference_2013/Archive}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | </font> | ||
<headertabs /> | <headertabs /> | ||
[[Category:OWASP_AppSec_Conference]] | [[Category:OWASP_AppSec_Conference]] | ||
Revision as of 00:34, 13 January 2013
- Introduction
- CFP
- Registration
- Venue
- Conference Schedule
- Event Sponsors
- Continuing Education Credit
- Hotel and Travel
- Presentation Materials
Welcome to SnowFROC 2013 - the 5th Annual Front Range OWASP Security Conference
The Colorado OWASP chapters are proud to present the 5th annual SnowFROC. Join 300 other developers, business owners, and security professionals for a day-and-a-half of presentations, training, and Birds-of-a-Feather (BoaF) sessions. The SnowFROC 2013 keynote speaker is Neal Ziring, Technical Director of InfoProtection at NSA.
The conference will occur on Thursday, March 28th at the Denver Marriott City Center and will feature four primary tracks:
- High-Level Technical
- Deep-Dive / Hands-on Technical
- Management
- Legal
Running in parallel to the conference proceedings will be a capture the flag (CTF) hacking competition developed exclusively for SnowFROC by Boulder OWASP chapter members. The day will conclude with a moderated panel discussion featuring top industry leaders.
On Friday, March 29, Aaron Weaver will teach a course in secure coding. This training is free to SnowFROC attendees!
Friday will also offer BoaF sessions. Join like-minded industry leaders and discuss pressing issues facing the industry and you. BoaF sessions are self-lead and may address and issue you would like. Pitch your idea and get the ball rolling!
Finally, Friday will feature a postmortem of the CTF tournament. In addition to discussing solutions, techniques, and tools, we will encourage participants to attack the previously out-of-bounds CTF framework. Itching to break into the scoreboard and rack up the points? The gloves come off Friday morning.
Conference Committee
Mark Major: Director
Brad Carvalho: Sponsorship, Executive events
Craig Klosterman: Merchandise
Steve Kosten: Sponsorship, Executive events
Glen Matthes: Planning
Chris Rossi: CTF, Networking events
Greg Foss: CTF
Colorado Chapter Hosts
OWASP Boulder chapter: Mark Major
OWASP Denver chapter: Steve Kosten, Brad Carvalho (acting)
Call for Presentations
Please direct all interested practitioners and colleagues to this site.
Submission process
Potential speakers may submit abstracts of proposed presentations here.
Abstracts will be formatted automatically during the submission process. However, all uploaded materials must adhere to the following requirements:
- Only Microsoft Word documents, PDFs, rich-text format documents, and text files will be reviewed.
- Author names, affiliations, email addresses, and other personally-identifiable information must be stripped from the uploaded document.
- All presentations must be titled. Titles should appear at the top of the page.
- The overview of the proposed presentation should not exceed 300 words.
Presenters will be allotted 45-minute time slots. One abstract must be submitted for each presentation considered. All abstracts must be written in English.
Evaluation process
The following criteria will determine abstract rankings:
- Applicability to the requested topics (see below)
- Relevance to web application development and operations
- Relevance to the cyber security industry at large
- Relevance to the OWASP Foundation
- Strength of presentation (as determined by the review committee)
- Timeliness of submission
Submitted abstracts will be assessed by selected members of the Colorado OWASP chapters. All reviews will be blind and author information will not be visible to reviewers.
Dates and deadlines
Abstract collection will begin January 14th and continue until all speaking slots are filled. Evaluations will occur on a rolling schedule with selected papers announced each Monday, beginning on February 11th. Although the rolling format extends the submission period significantly, potential speakers are advised to submit as early as possible in order to maximize chances for selection.
Final presentations of accepted abstracts must be submitted for review by March 17th. Templates and other presentation formatting constraints will be made available to selected speakers directly.
Phase 1: Jan 14 - Feb 11
Jan 14 - Feb 03: Submission period
Feb 04 - Feb 10: Evaluation period
Feb 11: Selected papers announcement
Phase 2: Feb 04 - Feb 18 (as needed)
Feb 04 - Feb 10: Submission period
Feb 11 - Feb 17: Evaluation period
Feb 18: Selected papers announcement
Phase 3: Feb 11 - Feb 25 (as needed)
Jan 11 - Feb 17: Submission period
Feb 18 - Feb 24: Evaluation period
Feb 25: Selected papers announcement
Phase 4: Feb 18 - Mar 04 (as needed)
Feb 18 - Feb 24: Submission period
Feb 25 - Mar 03: Evaluation period
Mar 04: Selected papers announcement
Presentation evaluation
Mar 17: Final draft presentations due
Mar 18 - Mar 25: Committee final review
Mar 28, 2013: SnowFROC proceedings
Legalities
All speakers must agree with and abide by the OWASP Speaker Agreement v2.0.
Anyone who cannot or will not abide by these terms will not be permitted to present at the conference.
In addition, presenters must agree to allow use of abstract titles, text, speaker names, and bios for conference promotion. With speaker consent, presentation materials will be distributed to conference attendees and will be recorded and archived for future reference.
Preferred topics
The following topics will be prioritized during the selection process.
High-level technical track
- Web application security testing, especially targeting large and complex enterprise applications
- Mobile device security
- Cloud security
- Impacts on the security model
- Implementation of security controls
- OWASP tools and projects
- New and proposed projects
- Development and status of existing projects
Deep-dive technical track
- Technology-specific presentations (HTML5, AJAX, etc.)
- Secure coding for web applications
- Static code analysis
- Hands-on countermeasures
- Encryption across an n-tiered web application stack
- Auditing web application mash-ups
Management track
- Web application security management (scope, boundaries, responsibilities, legal considerations, etc.)
- Emerging threats
- Planning and managing secure software development life cycles
- Metrics for managing application security
- Business risks associated with application security
Legal track
- Liability related to web application security
- Data ownership and privacy laws within the cloud
- Cyber security and privacy legislation and regulation
- Electronic discovery considerations, both traditional and in the cloud
- Cyber security considerations related to law enforcement
- Data disclosure liability
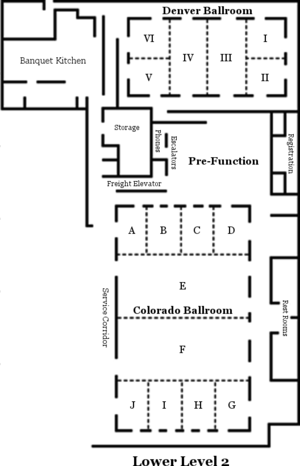
Conference Location
|
SnowFROC 2013 Schedule
Current Sponsors
Aerstone
| Aerstone provides strategic and technical cyber security consulting services including assessments, planning, architecture designed incident response, regulatory compliance, and computer forensics. We provide services and products for medium to large healthcare providers, financial services organizations and legal firms, and law enforcement. Clients range from local businesses to government agencies. |
Applied Trust
| AppliedTrust provides IT infrastructure, security, and opensource consulting services. Our clients are organizations where effective IT is critical to the reputation and growth of their business, and hail from a variety of industries including healthcare, financial services, hospitality, recreation, and government. Our specialty areas include:
|
Checkmarx
| Checkmarx - Source Code Analysis Made Easy
Checkmarx is the developer of next generation Static Code Analysis (SCA) solutions. The company pioneered the concept of a query language-based solution for identifying technical and logical code vulnerabilities. Checkmarx provides the best way for organizations to introduce security into their Software Development Lifecycle (SDLC) which systematically eliminates software risk. The product enables developers and auditors to easily scan un-compiled / un-built code in all major coding languages anywhere, anytime. CxSuite's application security testing is available in both "On Premise" and "On Demand" configurations. The security testing scans for the most prevalent security vulnerabilities as determined by OWASP Top 10, SANS, and other major standards. Checkmarx was recognized by Gartner as sole visionary in their latest SAST magic quadrant and as Cool vendor in application security. Customers include Fortune 500, government organizations and SMBs in over 30 countries. |
HP
| HP is a leading provider of security and compliance solutions for the modern enterprise that wants to mitigate risk in its hybrid environment and defend against advanced threats. Based on market leading products from HP ArcSight, HP Fortify, and HP TippingPoint, the HP Security Intelligence Platform uniquely delivers the advanced correlation, application protection, and network defenses to protect today’s hybrid IT infrastructure from sophisticated cyber threats. |
Security Pursuit
| Security Pursuit provides computer security services to help organizations protect their critical information systems. Based in Denver, Colorado, Security Pursuit's services include: IT Security Risk Analysis, Data Breach Incident Response, Network Penetration Testing and Vulnerability Assessments, Website Penetration Testing and Vulnerability Assessments, Wireless Network Security, Social Engineering Prevention, Security Awareness Training, Employee Termination Assistance and Virtual CISO consulting. We have conducted hundreds of security assessments for financial institutions, healthcare providers, retailers, utilities, airports, and municipal governments; many in support of PCI, GLBA, NCUA, and HIPAA compliance requirements. Security Pursuit’s computer security services provide you with a higher level of awareness about the security posture of your organization. |
SouthSeas
| Escaping network insecurity means identifying and eliminating vulnerability at each and every level. At South Seas Corporation, we consider the big picture and the finest details of your information technology, from computers to routers to servers and the cabling between, from intranets to the internet, from mobile devices to web applications to remote networks across the globe. We also address administrative issues, including security policy and federal compliance. Of course, your budget is top of mind from the beginning. The end result is a tailored solution designed to secure every byte of information traveling through, to and around your organization at every point, installed by certified experts trained to work hand in hand with your IT department. Take a load off your mind with South Seas Corporation. |
Veracode
| Today most global enterprises live under the constant threat of being hacked, which begs this critical question – how do they innovate and rapidly release new and improved applications required to be an industry leader while still securing their organizations critical IP and data assets? Before Veracode, application security was widely thought to slow innovation, but not anymore. With the Veracode Platform, application security and innovation can go hand-in-hand. Whether applications are built, brought or outsourced, Veracode’s patented testing technology provides the intelligence needed to quickly secure them from the most common forms of attack. |
CPE and CLE credits
Much of the SnowFROC content is eligible for continuing professional education (CPE) or continuing legal education (CLE) credits. Please check with your institution regarding specific requirements.
CPE credits
The CISM CPE policy (www.isaca.org/cismcpepolicy) states:
One continuing professional education hour is earned for each fifty minutes of active participation (excluding lunches and breaks) in a professional educational activity. Continuing professional education hours are only earned in full-hour increments and rounding must be down. For example, a CISA who attends an eight-hour presentation (480 minutes) with 90 minutes of breaks will earn seven (7) continuing professional education hours.
Activities that qualify for CPE must be directly applicable to the management, design or assessment of an enterprise's information security as per the CISM job practice"
CLE credits
Conference organizers are actively pursuing certified seminar accreditation from the Colorado Board of Continuing Legal and Judicial Education. For additional information regarding CPEs and Rule 260 please visit the Colorado Supreme Court's CLE page.
Denver Marriott City Center
|
Denver Attractions
- Monty Python's Spamalot at the Buell Theatre (3/28-30)
- World-class exhibitions at the Denver Art Museum
- Guided walking tours of downtown's microbreweries
- The Denver Nuggets host the Brooklyn Nets (3/29 @ 7pm)
- Free tours of the US Mint
- Plus all the standard downtown stuff: shopping, more shopping, an aquarium, a zoo, comedy clubs, local music, and many clubs, restaurants, and art galleries.
Colorado Attractions
Out-of-town visitors may be interested in staying for the weekend to enjoy all Colorado has to offer, including:
- Red Rocks amphitheatre
- The Butterfly Pavilion
- Garden of the Gods (Colorado Springs)
- Royal Gorge (Canyon City)
- Coors, New Belgium, and many other Colorado breweries
Skiing
The SnowFROC staff is pursuing a chartered bus and negotiated discounts for premier ski resorts and lift tickets. Check back soon for details!
2013 presentations
Keynote Address: Data Protection for the 21st Century
Panel Discussion
Technical Track
DevFu: The inner ninja in every application developer
Adventures in Large Scale HTTP Header Abuse
Angry Cars: Hacking the "Car as Platform"
DevOps and Security: It's Happening. Right Now.
Real World Cloud Application Security
Deep-Dive Track
SIP Based Cloud Instances
How Malware Attacks Web Applications
Top Ten Web Application Defenses
A Demo of and Preventing XSS in .NET Applications
Data Mining a Mountain of Zero-Day Vulnerabilities
Management Track
Digital Bounty Hunters - Decoding Bug Bounty Programs
Linking Security to Business Value in the Customer Service Industry
Using SaaS and the Cloud to Secure the SDLC
Measuring Security Best Practices With Open SAMM
Defending Desktop (.NET/C#) Applications: Mitigating in the Dark (A Case Study Remix)
Legal Track
Electronic Discovery for System Administrators
Legal Issues of Forensics in the Cloud
CISPA: Why Privacy Advocates Hate This Legislation
Crafting a Plan for When Security Fails
Information Control: The Critical Need for a Defensible Position - Securing the Information Ecosystem
Previous conferences
2012 presentations are available here.