This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP AppSec DC 2012"
Mark.bristow (talk | contribs) (→OWASP Member Door Prizes!) |
Mark.bristow (talk | contribs) (→OWASP Member Door Prizes!) |
||
| Line 229: | Line 229: | ||
== OWASP Member Door Prizes! == | == OWASP Member Door Prizes! == | ||
| − | Are you an [[Membership|OWASP Member]]? At AppSecDC we will be giving away some amazing door prizes, including an Apple iPad "3" 4G to some randomly selected OWASP members in attendance. You HAVE to be an OWASP member to be | + | Are you an [[Membership|OWASP Member]]? At AppSecDC we will be giving away some amazing door prizes, including an Apple iPad "3" 4G to some randomly selected OWASP members in attendance. You HAVE to be an OWASP member to be eligible, but if your not, you can easily add the $50 annual membership to your conference ticket and receive $50 off admission. That's right, '''FREE OWASP MEMBERSHIP''' when combined with AppSec DC Registration! So remember to [https://guest.cvent.com/EVENTS/Register/IdentityConfirmation.aspx?e=d52c6f5f-d568-4e16-b8e0-b5e2bf87ab3a Register] today with your OWASP membership! |
| + | |||
| + | == Sponsor Passport == | ||
| + | Please take a moment to visit our sponsors and thank them for their support of AppSec DC, OWASP and the Application Security Mission. To help this along all attendees will receive a sponsor passport. As you visit all of our Gold and Silver sponsor booths they will stamp your passport which you can turn in by noon on the 5th to be entered to win an Apple iPad "3" 4G! | ||
== CTF == | == CTF == | ||
Revision as of 14:01, 30 March 2012
Registration Now OPEN! | Hotel | Schedule | Convention Center | AppSecDC.org
- Welcome
- CFP
- Registration
- Volunteer
- Schedule
- Training
- Special Events
- Contests
- Venue
- Hotel
- Sponsors
- Travel
- Conference Committee
- FAQ
|
|
NOTICE
Many of you have written to us asking about the requirement for a paper in our CFP hosted on EasyChair. Due to an unforseen change in the way EasyChair works, you are no longer able to configure a submission to require only an abstract as we thought we had done, and done in the past. To be clear, we are ***NOT*** requiring papers with our CFP submissions. As we have already started the CFP and can not move the platform we ask that anyone who does not have a paper simply submit their abstract as a .txt file to satisfy the systems requirement to upload a paper.
We apologize for this inconvience and the confusion it has caused and as a result of the confusion, we are extending the AppSec DC CFP deadline to Feburary 17th 2012 at 11:59 EST to allow all to submit their topics.
Submissions
Submit papers to http://cfp.appsecdc.org. Submission deadline is Feburary 17th 2012. Inquires can be made to cfpATappsecdcDOTorg.
To submit a paper, you will have to sign up for an EasyChair account at https://www.easychair.org/account/signup.cgi.
Topics
In accordance with the broader OWASP mission stemming from the 2011 OWASP Global Summit, AppSec DC is working to reflect the move of OWASP towards embracing all facets of Application Security, and not restricting it's content to strictly to the realm of web applications. Therefore we invite all practitioners of application security and those who work with or interact with all facets of application security to submit papers and participate in the conference.
The AppSec DC 2012 Content Committee is seeking presentations in the following subject areas:
- OWASP Projects
- Research in Application Security Defense (Defense & Countermeasures)
- Research in Application Security Offense (Vulnerabilities & Exploits)
- Web Application Security
- Critical Infrastructure Security
- Mobile Security
- Government Initiatives & Government Case Studies
- Effective Case studies in Policy, Governance, Architecture or Life Cycle
- and other application security topics
Submit papers to http://cfp.appsecdc.org. Submission deadline is Feburary 17th 2012. Inquires can be made to cfpATappsecdcDOTorg.
To submit a paper, you will have to sign up for an EasyChair account at https://www.easychair.org/account/signup.cgi.
Additional information can be found in the Conference FAQ.
Register Here
Registration is now OPEN.
You can register via at http://reg.appsecdc.org
Registration Fees
| Ticket Type | Early (until 2/3) | Regular Price (until 3/15) | Late (after 3/15) |
|---|---|---|---|
| Non-Member | $445.00 | $495.00 | $545.00 |
| Non-Member plus 1 year OWASP Membership! | $445.00 | $495.00 | $545.00 |
| Active OWASP Member | $395.00 | $445.00 | $495.00 |
| Student | $75.00 | $75.00 | $100.00 |
| Course | Fee |
|---|---|
| 1 Day Training | $745 |
| 2 Day Training | $1495 |
ATTENTION FEDERAL EMPLOYEES: Enter code ASDC12FED for $100 off, limited time only! (must register with your .gov or .mil email address)
For student discount, attendees must present proof of enrollment when picking up your badge.
Group Discounts
- 10% off for groups of 10-19
- 20% off for groups of 20-29
- 30% off for groups of 30 or more
Who Should Attend AppSec DC 2012
- Application Developers
- Application Testers and Quality Assurance
- Application Project Management and Staff
- Chief Information Officers, Chief Information Security Officers, Chief Technology Officers, Deputies, Associates and Staff
- Chief Financial Officers, Auditors, and Staff Responsible for IT Security Oversight and Compliance
- Security Managers and Staff
- Executives, Managers, and Staff Responsible for IT Security Governance
- IT Professionals Interesting in Improving IT Security
- Anyone interested in learning about or promoting Web Application Security
Volunteers Needed!
Get involved!
We will take all the help we can get to pull off the best Web Application Security Conference of the year!
More opportunities and areas will be added as time goes on. Our Volunteer Guide can be downloaded which outlines some of the responsibilities and available positions.
To volunteer please email [email protected]
| Plenary Day 1 - 4/4/2012 | ||||
| Offense & Tools Room 201 |
Case Studies Room 202A |
IoMT Room 202B |
Interrogate! Room 206 | |
|---|---|---|---|---|
| 7:30 AM - 8:50 AM | Registration | |||
| 8:50 AM - 9:00 AM | Welcome and Opening Remarks Room 202A | |||
| 9:00 AM - 10:00 AM | Keynote: Dan Geer Room 202A | |||
| 10:00 AM - 10:45 AM | OWASP Board Room 202A | |||
| 10:45 AM - 11:00 AM | Coffee Break | |||
| 11:00 AM - 11:50 AM | DOMJacking - Attack, Exploit and Defense video | slides Shreeraj Shah |
The Unfortunate Reality of Insecure Libraries video | slides Jeff Williams and Arshan Dabirsiaghi |
Python Basics for Web App Pentesters - Part 2 video | slides Justin Searle |
Integrating Application Security into your Lifecycle and
Procurement video | slides Moderator: Jim Manico |
| 11:50 AM - 12:00 PM | Coffee Break | |||
| 12:00 PM - 12:50 PM | Attacking CAPTCHAs for Fun and Profit video | slides Gursev Singh Kalra |
GoatDroid video | slides Jack Manino |
Security is Dead. Long Live Rugged DevOps: IT at Ludicrous
Speed video | slides Joshua Corman | |
| 12:50 PM - 2:30 PM | No-Host Lunch | |||
| 2:30 PM - 3:20 PM | Hacking .NET(C#) Applications: The Black Arts video | slides Jon McCoy |
Security at scale: Web application security in a continuous
deployment environment video | slides Zane Lackey |
The "Easy" Button for Your Web Application Security Career video | slides Salvador Grec |
Risk Analysis and Measurement with CWRAF video | slides Joe Jarzombek, Bob Martin, Walter Houser and Tom Brennan |
| 3:20 PM - 3:30 PM | Coffee Break | |||
| 3:30 PM - 4:20 PM | OWASP Broken Web Applications (OWASP BWA) 1.0 Release video | slides Chuck Willis |
Security Is Like An Onion, That's Why It Makes You Cry video | slides Michele Chubirka |
Anatomy of a Logic Flaw video | slides Charles Henderson and David Byrne | |
| 4:20 PM - 4:30 PM | Coffee Break | |||
| 4:30 PM - 5:20 PM | New and Improved Hacking Oracle from Web video | slides Sumit Siddharth |
State of Web Security video | slides Robert Rowley |
Old Webshells, New Tricks -- How Persistent Threats have
revived an old idea, and how you can detect them. video | slides Ryan Kazanciyan |
Fed Panel video | slides Moderator: Rex Booth Ron Ross, Joe Jarzombek, Kris Britton & Darren Death |
| 5:20 PM - 5:30 PM | Coffee Break | |||
| 5:30 PM - 6:20 PM | Unraveling some of the Mysteries around DOM-based XSS video | slides Dave Wichers |
2012 Global Security Report video | slides Tom Brennan and Nick Percoco |
Survivable Software for Cyber-Physical Systems video | slides Karen Mercedes Goertzel | |
| 6:20 PM | Networking Opportunity in Room 207AB sponsored by: 
| |||
Training
OWASP strives to provide world class training for a variety of skill levels and interests at its conferences. From the novice to the expert, developers to managers, there is a training course at AppSec DC for you! Classes will begin at 9 AM each day and run until 5 PM (Daily schedule set by the trainer). Morning refreshments and lunch will be provided. Check each course for the required materials.
Price per attendee (conference Registration is a separate item):
- 2-Day Class $1495
- 1-Day Class $745
Special Free Training
Certified Secure Software Lifecycle Professional (CSSLP) Clinic | FREE | Course Detail | Rm 204C
Educate yourself in Secure Software Design and Development which are two of the seven domains from the Certified Secure Software Lifecycle Professional (CSSLP) certification. This session will provide an in-depth education of these two tough domains of the CSSLP. We will cover the skills and knowledge needed to design and develop secure code. In the Secure Software Design domain, you will learn the fundamentals of design principles when applied will save costly rework. In the Secure Software Development domain, we will discuss the OWASP Top 10 threats and how to mitigate them effectively.
The Certified Secure Software Lifecycle Professional (CSSLP) is an (ISC)2 certification with 7 domains focusing on the topics needed to develop hacker resilient software. CSSLPs are professionals who have validated their competency in incorporating security into each phase of the software lifecycle.
2 Day Classes
Assessing and Exploiting Web Applications with Samurai-WTF | 2 Day | Course Detail | Rm 203A
Come take the official Samurai-WTF training course given by the two founders and lead developers of the project! You will learn the latest Samurai-WTF open source tools and as well as the latest techniques to perform web application penetration tests. After a quick overview of pen testing methodology, the instructors will lead you through the penetration and exploitation of various web applications, including client side attacks using flaws within the application. Different sets of open source tools will be used on each web application, allowing you to learn first hand the pros and cons of each tool. After you have gained experience with the Samurai-WTF tools, you will be challenged with a capture the flag event. This final challenge will give you time to practice your new skills at your own pace and experiment with your favorite new tools. This experience will help you gain the confidence and knowledge necessary to perform web application assessments and expose you to the wealth of freely available, open source tools.
Building Secure Android Apps | 2 Day | Course Detail | Rm 203B
The course focuses on building secure mobile applications for the Android platform. Students will learn about the Android security model and platform security features. They will be introduced to mobile application threat modeling, and learn how to apply the outcomes of threat modeling directly into their design and development processes. The OWASP Mobile Top 10 Risks and Controls will be covered at great length.
After students are taught foundational information, they will learn how to properly use the various Android components and APIs to reduce the amount of vulnerabilities within production code. Hands-on labs will use the vulnerable mobile Android applications provided by the OWASP GoatDroid project. Students will learn many techniques for performing source code reviews, penetration testing, and forensic analysis of Android applications. Hands-on exercises represent a large portion of the course. Each concept presented will include examples of insecure and secure code, along with strategies for remediation. By teaching students how to identify and exploit various security flaws, they will gain a greater understanding of how the security controls actually protect their applications.
At the end of this two-day course, attendees should understand how to build secure applications, perform source code reviews, and perform penetration testing for Android applications. They will also understand and be able to demonstrate expertise at applying security controls to applications for addressing many security defects. Each student will ultimately take back with them to their workplace a repeatable and reliable methodology for building and maintaining secure Android applications.
The Art of exploiting Injection Flaws | 2 Day | Course Detail | Rm 208A
OWASP rates injection flaws as the most critical vulnerability within the Top 10 most Critical Web Application Security Risks under the OWASP Top 10 project. http://www.owasp.org/index.php/Top_10_2010-A1. This hands-on session will only focus on the injection flaws and the attendees will get an "in-depth" understanding of the flaws arising from this vulnerability. The topics covered in the class are, SQL Injection, XPATH Injection, LDAP Injection, Hibernate Query Language Injection, Direct OS Code Injection, and XML Entity Injection. The workshop covers classical issues such as SQL Injection, which is an oldie yet very relevant in today's scenario as well as some lesser known injection flaws such as LDAP, XPATH and XML Injection. During the 2 days course, the attendees will have access to a number of challenges for each flaw and they will learn a variety of exploitation techniques used by the attackers in the wild. Identify, extract, escalate, execute; we have got it all covered.
Virtual Patching Workshop | 2 Day | Course Detail | Rm 208B
Identification of web application vulnerabilities is only half the battle with remediation efforts as the other. Let's face the facts, there are many real world business scenarios where it is not possible to update web application code in either a timely manner or at all. This is where the tactical use-case of implementing a web application firewall to address identified issues proves its worth.
This workshop is intended to provide an overview of the recommended practices for utilizing a web application firewall for virtual patching. After discussing the framework to use, we will then present a very interesting OWASP Summer of Code Project where the challenge was to attempt to mitigate as many of the OWASP WebGoat vulnerabilities as possible using the open source ModSecurity web application firewall. During the workshop, we will discuss both WebGoat and ModSecurity and provide in-depth walk-throughs of the complex fixes. Examples will include addressing not only attacks but the underlying vulnerabilities, using data persistence for multiple-step processes, content injection and even examples of the new LUA programming language API. The goal of this workshop is to both highlight cutting edge mitigation options using a web application firewall and to show how it can effectively be used by security consultants who traditionally could only offer source code fixes.
1 Day Classes
Application Source Code Analysis - Discovering Vulnerabilities in Web 2.0, HTML5 and RIA | 1 Day (4/2/2012) | Course Detail | Rm 204A
Enterprise application source code, independent of languages and platforms, is a major source of vulnerabilities. The class is designed and developed to focus on enterprise architecture and application analytics to discover vulnerabilities across Web 2.0, RIA and HTML5. We will be covering analysis techniques, with tools, for assessment and review of enterprise application source code. It is imperative to know source code review methodologies and strategies for analysis. The emphasis of the class would be to develop a complete understanding of source code analysis, techniques and tools to address top set of vulnerabilities. Knowledge gained would help in analyzing and securing next generation enterprise applications at all different stages - architecture, design and/or development. The course is designed and delivered by the author of "Web Hacking: Attacks and Defenses", ?Hacking Web Services? and ?Web 2.0 Security ? Defending Ajax, RIA and SOA?, bringing his experience in application security and research to the curriculum.
Pratical Threat Modeling | 1 Day (4/2/2012) | Course Detail | Rm 204B
Threat modeling is gaining traction as a fundamental application security activity. In this class students learn about the attacks that their applications may face and then both formal and informal approaches to threat modeling. Using a fictional scenario, students perform all the activities of a threat model on a complex application ? including analyzing design documents and role-playing interviews. Students learn about the industry standard formal threat modeling process as well as Facilitated Application Threat Modeling: a 1-day approach to threat modeling pioneered by Security Compass. Students will also be taught about Security Compass?s unique source-code/design-pattern level threat modeling.
Mobile Hacking and Securing | 1 Day (4/3/2012)| Course Detail | Rm 204A
Students will discover mobile hacking techniques for Android and iPhone. They will understand the platform security models, device security models, app analysis, file system analysis and runtime analysis for these popular mobile operating systems. This course will provide students with the knowledge necessary to assess mobile app security including what hackers look for in mobile apps. Hacking apps themselves will equip them with the skills required to protect their own apps from attacks. Students will come out with an understanding of the pitfalls to mobile device security and the importance of developing mobile apps securely. They will learn the concepts necessary to securely develop mobile in your organization.
WebAppSec: Developing Secure Web Applications | 1 Day (4/3/2012)| Course Detail | Rm 204B
Web applications continue to be the frontier of wide-spread security breaches. This tutorial will guide through development practices to ensure the security and integrity of web applications, in turn protecting user data and the infrastructure the application runs on. Several attack types and risks will be reviewed (including OWASP?s Top 10), along with how the proper development practices can mitigate their damage. Although examples covered are PHP-based, much of the content is also applicable to other languages. This course was sold out at AppSec USA 2011.
OWASP Mobile Security Project: Working Session | 4/4/2012 rm 203A
The working session will be held to reflect on achievements, discuss current initiatives, and to identify emerging areas of concern. If you are involved with the project or would like to get involved, the working session is the perfect place for your voice to be heard.
Through the OWASP Mobile Security Project, our goal is to raise visibility and awareness around mobile application security issues. With collaboration between many different industries, we are bringing together experts from many different areas to solve hard problems.
Join us in our efforts to make the mobile world a more secure place
OWASP Member Door Prizes!
Are you an OWASP Member? At AppSecDC we will be giving away some amazing door prizes, including an Apple iPad "3" 4G to some randomly selected OWASP members in attendance. You HAVE to be an OWASP member to be eligible, but if your not, you can easily add the $50 annual membership to your conference ticket and receive $50 off admission. That's right, FREE OWASP MEMBERSHIP when combined with AppSec DC Registration! So remember to Register today with your OWASP membership!
Sponsor Passport
Please take a moment to visit our sponsors and thank them for their support of AppSec DC, OWASP and the Application Security Mission. To help this along all attendees will receive a sponsor passport. As you visit all of our Gold and Silver sponsor booths they will stamp your passport which you can turn in by noon on the 5th to be entered to win an Apple iPad "3" 4G!
CTF
AppSec DC 2012 CTF will be a competition in which participants compete for prizes in a test of application and network hacking skills. The contestants will participate in real-world scenarios designed to simulate vulnerabilities discovered in production environments. The competition will focus on application security but participants should arrive ready with an arsenal of skill-sets to complete these challenges.
Rules:
The contest begins on April 4th at 1pm and ends the next day, April 5th at 1pm. Competitors are allowed to team up with a other contestants but prizes are only available for four (4) participants. All participants must physically attending the conference and external access ot the system is not available. Additionally, we are bound by the Convention Center’s hours of operation to conduct the CTF so this will not be an all night competition.
The scoring system and any other system NOT designated as “In-Scope” is considered OFF-LIMITS and any malicious activity towards or on those systems will result in an immediate disqualification for the team from which the participant(s) exists.
Contestants will use their own equipment to compete with but it is HIGHLY recommended that contestants do not bring equipment which hosts personal or sensitive data. Scoring will take place via a web-based scoreboard portal. Teams will have individual logins that will be required to submit points.
Resources:
Internet access will be offered at the conference as a means to obtain tools necessary for the competition, but we recommend that you bring the necessary tools to the event. We cannot guarantee access to all sites via the standard convention network, and visiting some sites you would normally obtain hacking tools from may be blocked from the normal convention Wi-Fi. OWASP AppSec DC will provide an isolated the environment and systems which will host the vulnerable applications.
Bring...
- Android SDK (Emulator)
- Any other Android related testing tools (Mallory, Eclipse & DDMS, etc.)
- Your toolkit, of course :-)
- Energy!
Registration:
Registration will be held up to the day of the competition 4/4/2012 at 12:30PM and can be done either by sending an email to [email protected] in the format listed below or in person in room 207A. We urge participants to register prior to the conference as space is limited.
Name: First, Last Alias: Ex: 1337h4xx0r Team Name: Ex: E4tU4br34kf4s7 Team Size: Max of 4 List Teammates: By Alias, if none, list N/A
Walter E. Washington Convention Center
AppSec DC 2012 will be taking place at the Walter E. Washington Convention Center in downtown Washington DC.
The convention center is located over the Mount Vernon Square/Convention Center Metro stop on the Green and Yellow lines of the DC Metro, and only a few blocks from our convention hotel, the Grand Hyatt Washington (reserve rooms here).
Rooms are available at the Grand Hyatt Washington at the GSA Rate for April of 2012.
Reserve Rooms here!
Room Rates are only guaranteed through the first week of March. Rooms at the discounted rates are available three days before and after the conference dates for attendees wishing to enjoy Washington DC during the National Cherry Blossom Festival.
Sponsors
We are currently soliciting sponsors for the AppSec DC Conference. Please refer to our sponsorship opportunities for details. Please contact us at [email protected] for sponsorship opportunities.
The OWASP AppSec DC Conference is the premier gathering for Information Security leaders. Executives from the US Government, Fortune 500 firms, technical thought leaders, security architects and lead developers, gather to share cutting-edge ideas, initiatives and technology advancements. AppSec DC will be one of the first OWASP conferences to highlight the new OWASP scope expanding from web to all application security issues.
Attendees will be pushed through the Expo floor for breakfast, lunch and coffee breaks giving them direct access to sponsors’ booths and technology. OWASP will also be hosting a “sponsor passport” game with a top prize to help encourage traffic to all of our Gold, Platinum and Diamond sponsors. The conference is expected to draw over 600 national and international attendees; all with budgets dedicated to web application security and software assurance initiatives. Government, Financial Services, Media, Pharmaceuticals, Healthcare, Technology, and many other verticals will be represented.
Gold Sponsors |
|
|
|

| |
Silver Sponsors |

| ||||
Small Business |

|

| |||
Exhibitors |
|
|

|

| |
Item Sponsors |

| ||||
Event Supporters |

|
Traveling to the DC Metro Area
The Washington DC Area is serviced by three airports -- Reagan National (DCA), Dulles (IAD), and Thurgood Marshall Baltimore/Washington International (BWI). All currently have available transportation to downtown DC via public transportation, shuttles, or cab.
Washington DC is also serviced by Amtrak, VRE, and MARC train lines, which arrive in Union Station, a few metro stops or a short cab ride away from the convention center and the Grand Hyatt.
If you live in the DC Metropolitan area, we suggest taking Metro to the event. The convention center is located over the Mount Vernon Square/Convention Center Metro stop on the Green and Yellow lines of the DC Metro.
Organizers
Mail List: [email protected]
Arch-Minions
Mail List: [email protected]
- Facilities ([email protected])
- Content ([email protected])
- Press ([email protected])
- Registration/Info Desk ([email protected])
- Volunteer Coordinators ([email protected])
- Competitions/Contests/Events ([email protected])
- Marketing/Community Outreach ([email protected])
- Sponsorships ([email protected])
Q. What will it cost?
A. Ticketing prices are on the main page. Prices for 2012 have not been announced yet.
Call For Papers
Q. What is the Open Web & Application Security Project (OWASP)?
The Open Web & Application Security Project (OWASP) is a worldwide free and open community focused on improving the security of application software. Our mission is to make application security visible, so that people and organizations can make informed decisions about true application security risks. Everyone is free to participate in OWASP and all of our materials are available under a free and open software license. The OWASP Foundation is a 501c3 not-for-profit charitable organization that ensures the ongoing availability and support for our work with your support.
Q. How many speaking slots are there?
The schedule for AppSec DC will largely be based on the number of quality presentations we receive. While we have an outline for the conference schedule we cannot solidify it until the CFP has completed. In addition to the primary slots we will be selecting a small number of alternate presenters who will receive a free pass to the conference in return for being ready to present if there is a cancellation.
Q. What are the submission deadlines?
The dates for CFP are from October 11th to until January 15th. Some speaker selections may be made before the end of CFP.
Q: Who is allowed to submit presentations?
A: Original authors of presentations may submit presentations for consideration. Third party representatives such as PR firms or Speaker Representatives MAY NOT submit materials on behalf of a potential speaker.
Q: Why aren't Third Parties such as PR Firms allowed to submit presentations?
A: Due to potential copyright and intellectual property liability issues as well as the need for OWASP to have direct contact with potential and selected presenters to expedite selection and deliverable materials, we require that only original authors of presentations submit for the Call for Papers. Third party representatives such as PR firms or Speaker Representatives MAY NOT submit materials on behalf of a potential speaker.
Q: How long will I have to wait before I am notified if I have been accepted or denied?
A: Due to the overwhelming response from the community the planning committee needs more time to sift through all of the proposals that we received. We feel that it is better to give each presentation a complete review rather then meet a somewhat arbitrary deadline. Originally we promised that we would respond to speakers within 15 business days of the CFP closing. We do reserve the right to select outstanding presentations prior to the date that CFP closes.
Q. Is there an honorarium for presenters?
No. OWASP is committed to making its conferences available to the widest possible audience. In order to do this OWASP keeps the entrance fees as low as possible to make the conference accessible. As a result we are unable to provide a monetary honorarium but we welcome our speakers as our guests to the conference where they can network with other security professionals.
Q: I have been accepted. What are the materials that I have to turn in and what are the deadlines?
A: The following is a list of materials that are required from each accepted presentation. Failure to proceed these materials by the deadlines set forth for the event the presentation was accepted for will result in of acceptance.
- A confirmed Speaker Agreement
- Presentation in PowerPoint or Keynote format using the OWASP Template
- Detailed Bibliography of resources, co-authors, etc.
- Optional White Paper for inclusion on CD
Q: Do I have to submit a White Paper?
A: No. We would certainly appreciate any White Papers that can be included on the conference CD but they are not required. If you have written an existing white paper to go along with your presentation, please submit it with your CFP submission. Submissions with attached White Papers will receive additional consideration.
Q: What if I have a co-author who is not presenting. How do I cite the person(s)?
A: All co-authors and works that have been used should be cited in a detailed bibliography that will be published on the Conference CD.
Q: I have been accepted and would like to add co-presenters. Can I still do this?
A: No. Co-presenters should have been added at the time that the Presentation was submitted. They may attend the conference and present if they pay the full conference fee.
Q: My PR company/friends/co-workers/family would like to come see me give my presentation. Will they be allowed in for free?
A: No. All guests of speakers must be registered and paid in full in order to receive admission to the conference.
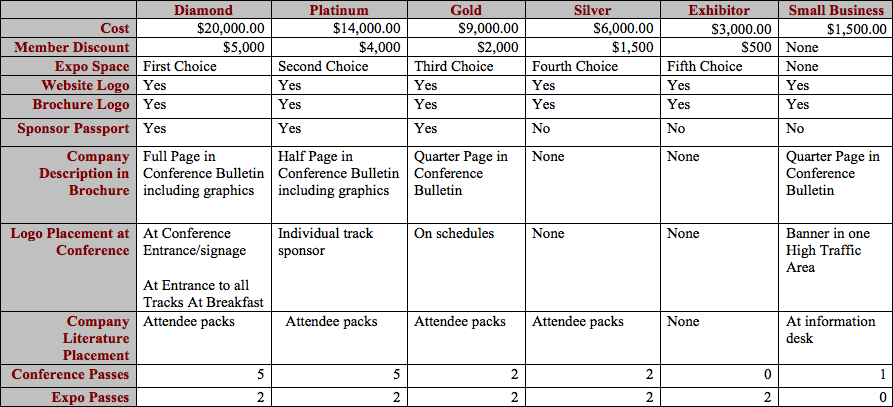
Q: My company wants to donate and support OWASP as a 501(3)c non-profit in exchange for resources at the Expo, what is the cost?
A: Sponsorship information can be found here.
Q. I have more questions
A: Email info(at)appsecdc.org concerning this event.
Gold Sponsors |
|
|
|

|
Silver Sponsors |

| |||
Small Business |

|

| ||
Exhibitors |
|
|

|

|
Gold Sponsors |
|
|
|

|
Silver Sponsors |

| |||
Small Business |

|

| ||
Exhibitors |
|
|

|

|


