This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
File list
This special page shows all uploaded files.
First page |
Previous page |
Next page |
Last page |
| Date | Name | Thumbnail | Size | Description | Versions |
|---|---|---|---|---|---|
| 19:31, 15 July 2010 | LASCON 2010 Additional.jpg (file) |  |
107 KB | 1 | |
| 19:29, 15 July 2010 | LASCON Sponsorship Options.pdf (file) | 901 KB | 1 | ||
| 19:27, 15 July 2010 | LASCON 2010 Sponsors.jpg (file) | 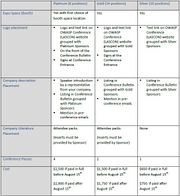 |
142 KB | 1 | |
| 16:00, 22 June 2010 | OWASP Lascon Logo.gif (file) |  |
5 KB | 1 | |
| 14:39, 16 June 2010 | Advanced Persistent Threats.pdf (file) | 5.22 MB | 1 | ||
| 15:43, 2 April 2010 | Reducing Your Data Security Risk Through Tokenization.pptx (file) | 2.74 MB | 1 | ||
| 20:47, 1 April 2010 | Enterprise Application Security Practices.ppt (file) | 932 KB | 1 | ||
| 20:09, 30 September 2009 | Austin Chapter OWASP ROI-mtesauro.pdf (file) | 482 KB | 1 | ||
| 19:52, 28 August 2009 | TM.pptx (file) | 1.05 MB | Michael Howard's presentation on Threat Modeling. | 1 | |
| 03:01, 29 April 2009 | OWASP - Architecting Secure Web Systems.pptx (file) | 381 KB | 1 | ||
| 13:14, 30 October 2008 | Using Proxies to secure applications and more.pptx (file) | 930 KB | Presented by Josh Sokol at the Austin OWASP meeting on 10/28/2008. The last Austin OWASP presentation of the year is a must see for anyone responsible for the security of a web application. It is a demonstration of the various types of proxy software and | 1 |
First page |
Previous page |
Next page |
Last page |