This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Category:OWASP WebGoat Project
|
OWASP WebGoat ProjectIntroductionWebGoat is a deliberately insecure web application maintained by OWASP designed to teach web application security lessons. You can install and practice with WebGoat. There are other 'goats' such as WebGoat for .Net. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat applications. For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. The application aims to provide a realistic teaching environment, providing users with hints and code to further explain the lesson. Why the name "WebGoat"? Developers should not feel bad about not knowing security. Even the best programmers make security errors. What they need is a scapegoat, right? Just blame it on the 'Goat! To get started download the the latest release here: https://github.com/WebGoat/WebGoat/releases WebGoat 8The WebGoat team is proud to present the first milestone release of version 8. It has been a long time since the last WebGoat 7 release, LessonsThe most important change is we moved towards a lesson model instead of 'just hacking' we now focus on explaining from the beginning what for example a SQL injection is. Each lesson within WebGoat now contains three elements:
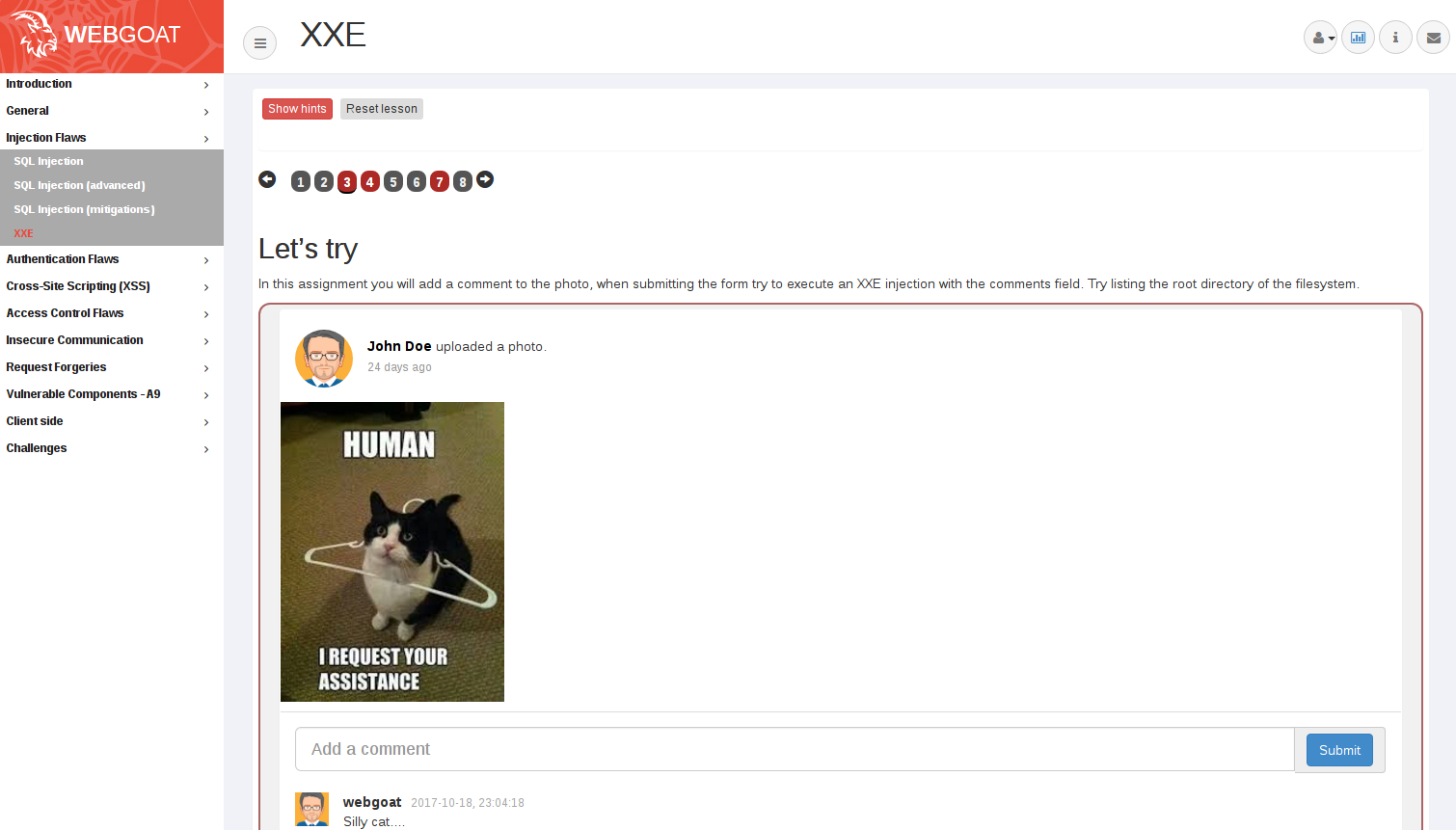
The screenshot shows the start of the lesson. At the top of the page there is a navigation bar which shows the number of steps within the lesson. A number with a red background means there is an assignment to solve. When you successfully complete the assignment the background will become green.
As you can see we also thought about the visual appearance of our assignments. In short: WebGoat is now a teaching platform instead of just a hacking platform. WebWolfWe used WebGoat 8 during our workshops/training and we one of the feedback items was that sometimes an assignment was not realistic enough: it was difficult to grasp the perspective of the "hacker" vs the user. During one of the 'Project summits' at the OWASP AppSec conference we came up with the idea of creating WebWolf which would make the distinction more clear between actions you are performing as a hacker and actions are performed from the perspective of the user. WebWolf is a completely separate web application which you **can** use to solve assignments. In
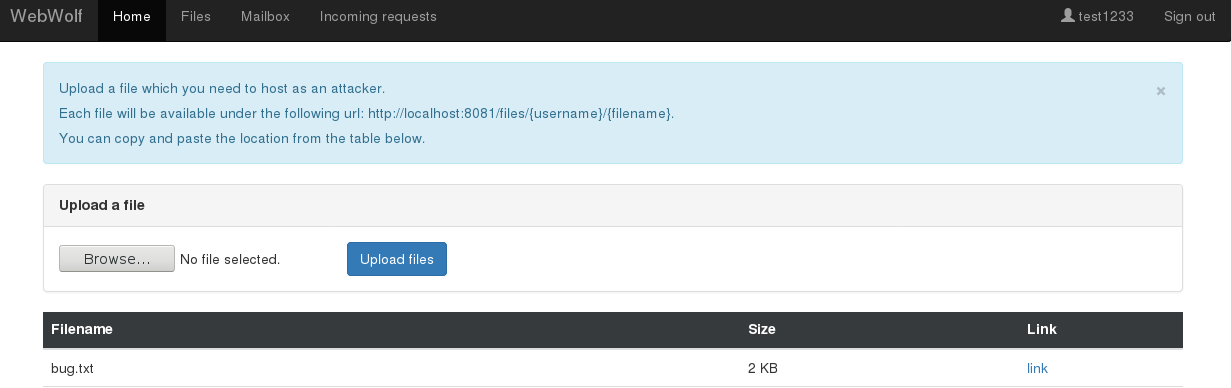
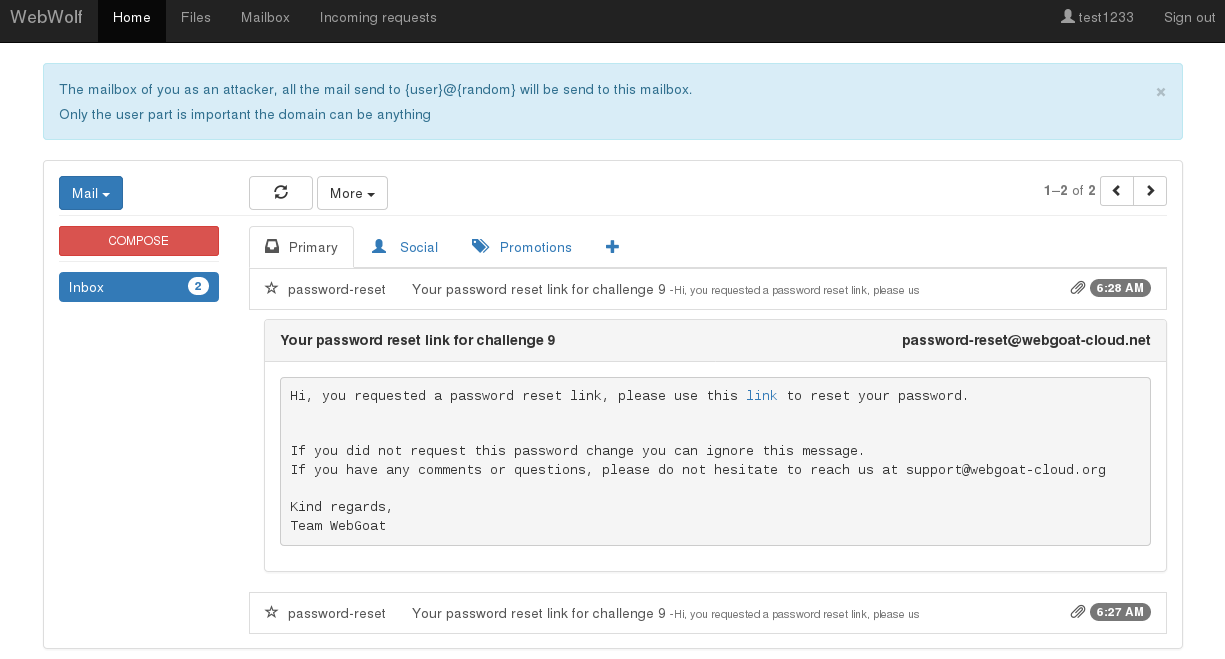
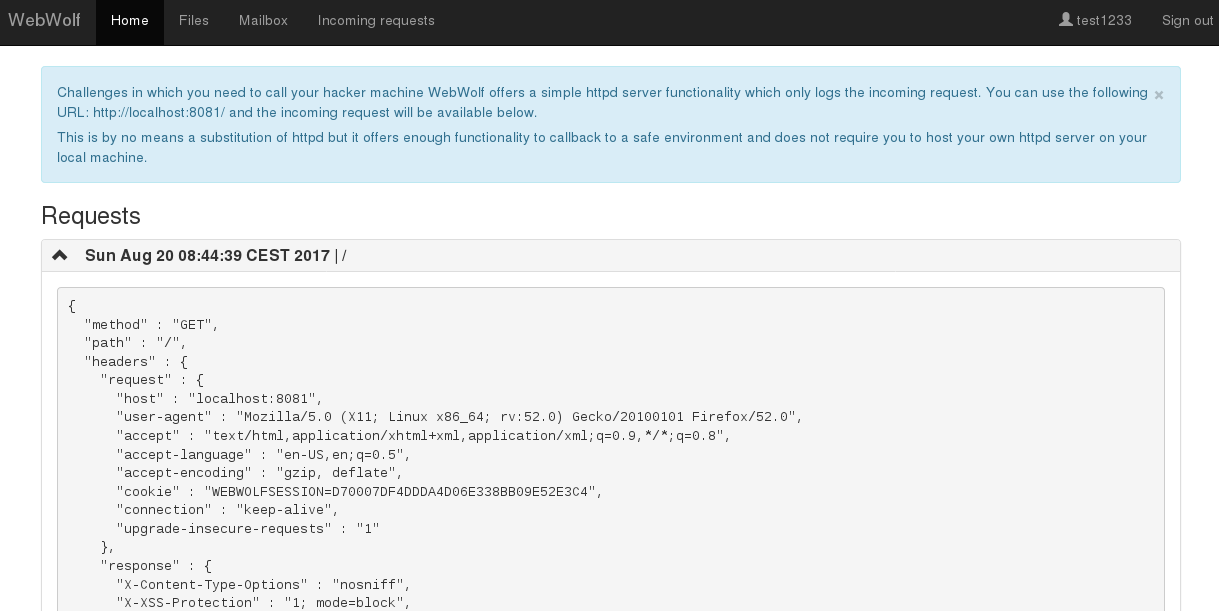
the current version a couple of assignment/challenges use WebWolf. At the moment WebWolf is able
to host files, receive e-mails and serve as a landing page. More details can be found in
our new WebWolf lesson inside WebWolf.
Some screenshots:
How to get started with WebWolf is described in a lesson within WebGoat, click [here](http://localhost:8080/WebGoat/start.mvc#lesson/WebWolfIntroduction.lesson)
Big thanks to OWASP for making it possible for us to go to the Project summits at AppSec conferences
Challenges/CTFDuring a couple of conferences we were asked to host a small Capture the Flag event with WebGoat. The first one was a success so we added a separate section in WebGoat with CTF challenges. Some of the challenges have a direct connection with the lessons but a couple of them are more for fun. Having the CTF challenges has two purposes:
IntroductionWebGoat is a deliberately insecure web application maintained by OWASP designed to teach web application security lessons. You can install and practice with WebGoat. There are other 'goats' such as WebGoat for .Net. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat applications. For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. The application aims to provide a realistic teaching environment, providing users with hints and code to further explain the lesson. Why the name "WebGoat"? Developers should not feel bad about not knowing security. Even the best programmers make security errors. What they need is a scapegoat, right? Just blame it on the 'Goat! To get started:
DescriptionWebGoat for J2EE is written in Java and therefore installs on any platform with a Java virtual machine. There are installation programs for Linux, OS X Tiger and Windows. Once deployed, the user can go through the lessons and track their progress with the scorecard. There are currently over 30 lessons, including those dealing with the following issues:
LicensingOWASP WebGoat Project is free to use. It is licensed under the GNU General Public License version 2.0 (GPLv2) Project SponsorsThe WebGoat project is sponsored by
|
Quick DownloadProject LeadersBruce Mayhew Related ProjectsSourcesSocial mediaEmail ListNews and Events
Classifications
| |||||||||
Q: Are you aware that lesson X does not work?
A: We may be. Head over to https://github.com/WebGoat/WebGoat/issues and log an issue if there is a specific, you have encountered on a lesson. Give us as much information as you can.
Q: When will WebGoat 7 be 'released'?
A: As of February 2nd version 7 has been released, see https://github.com/WebGoat/WebGoat/releases for more information.
The rest are questions we hope people ask, but maybe haven't really yet ...
Q: Do you need help?
A: Of course we would always love help, especially with testing and feedback. Experienced Java, UI and Design folk are welcome as well. Security professionals willing to develop content are also welcome, of course.
Q: How do I get involved?
A: Fork the repo. (https://help.github.com/articles/fork-a-repo/) you want to work on and stay in sync with the mainstream development in master (https://help.github.com/articles/syncing-a-fork/)
Q: What's the difference between the repo at https://github.com/WebGoat/WebGoat and the repo at https://github.com/WebGoat/WebGoat-Lessons
A: As of WebGoat 7, the architecture is more modular and lessons can be loaded dynamically. The first repo is for the 'container' or main 'framework' for containing lessons. The WebGoat-Lessons repo. is for lesson development
Q: How do I author a lesson for WebGoat?
A: For WebGoat 7 you can take a look at any existing lesson (see https://github.com/WebGoat/WebGoat-Lessons), copy it to a new project and implement your own lesson. For WebGoat 8, we plan to make that much simpler (read, no more ECS!).
Volunteers
The WebGoat project is run by Bruce Mayhew. He can be contacted at webgoat AT owasp.org. WebGoat distributions are currently maintained on GitHub. The WebGoat framework makes it extremely easy to add additional lessons. We are actively seeking developers to add new lessons as new web technologies emerge. If you are interested in volunteering for the project, or have a comment, question, or suggestion, please join the WebGoat mailing list.
Road Map / Goals
The project's overall goal is to...
Be the defacto standard web application security training environment
In the near term, we are focused on the following tactical goals...
- Add educational support for secure coding practices
- User management: add the ability to define new users through the UI
- Enhance enterprise lesson tracking
- Attract more contributions of lessons
- Translate all lessons to other languages
- Increase ease-of-use and expand user base
- Update code base to Spring Boot and improve overall code quality (remove technical dept)
- Introduces category based way of displaying lessons
- Port old lessons to the new teaching frame
Here are the current tasks defined to help us achieve these goals
Architectural
- Create a service layer (done)
- Create plugin architecture and port all lessons to plugins (done)
- Remove dependencies on Tomcat (done)
- Rewrite user administration to allow better user management (non-hackable)
- Fix Logoff (done)
- Defuse all lessons to disallow inadvertent harm to user's OS
General
- General security cleanup. Remove exploits that are not lesson specific
- Remove non working lessons
New Lessons
- Server side forward allows access to WEB-INF resources (obsolete)
- XML attacks - Entity recursion (done)
Getting Involved
For more information contact one of the project leads. Involvement in the development and promotion of WebGoat is actively encouraged! You do not have to be a security expert in order to contribute.
If you'd like to contribute coding-wise ...
- Get on the WebGoat mailing list (http://lists.owasp.org/mailman/listinfo/owasp-webgoat)
- Fork one of the repo's on github:
- https://github.com/WebGoat/WebGoat << this is the WebGoat 'container'. Instructions on getting up and running are here as well.
- https://github.com/WebGoat/WebGoat-Lessons << this is the Lesson repository
- Keep you repo in sync (https://help.github.com/articles/syncing-a-fork/)
- Issue pull requests as you fix bugs, add features etc.
Testers are always welcome/needed. Again, log issues and features requests at https://github.com/WebGoat/WebGoat. If you are a college or university and would like to use WebGoat for classes, we'd especially love to hear your feedback and what content/lessons you would like to see added to the project.
Adding content/lesssons We are working to make adding your own content easier and to integrate with other OWASP projects/content. We'd love to hear from you to move this forward.
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||||
Pages in category "OWASP WebGoat Project"
The following 17 pages are in this category, out of 17 total.