This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Basic Operation
You can help OWASP by improving it or discussing it on its Talk page.
Please add a comment to your tag. See FixME
WebGoat User Guide Table of Contents
At each stage of an application security assessment, it is important to understand the operation of the target.
This typically involves:
- Examining client side content, such as HTML and script
- Analyzing communications between the client and server
- Reviewing cookies and other local data
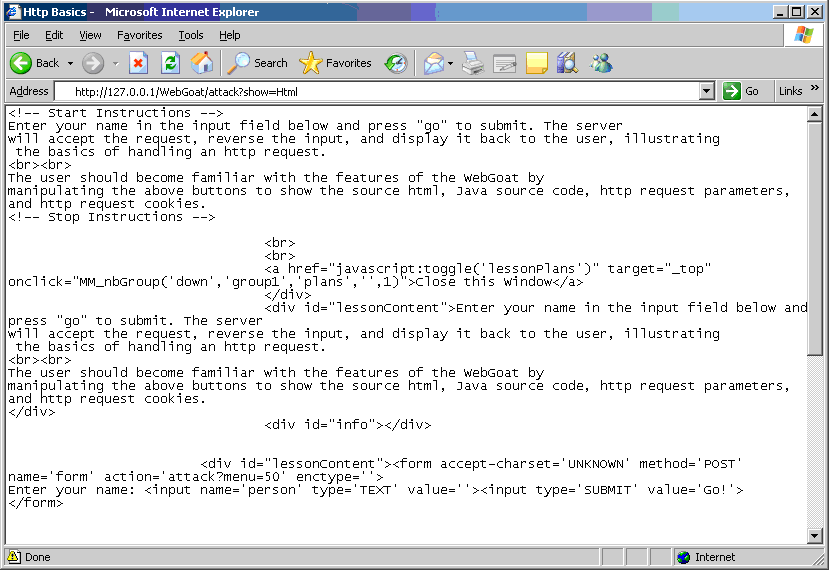
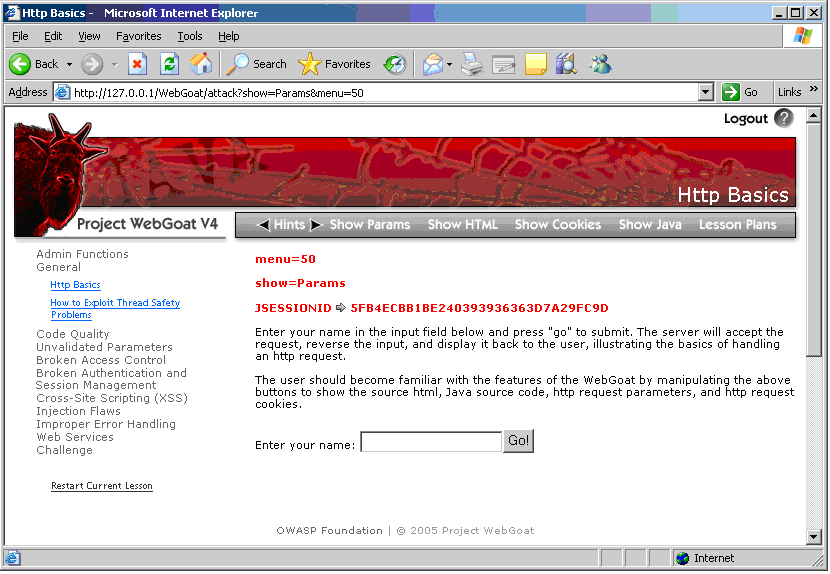
The browser typically makes it simple to view HTML source. WebGoat expands on that with operations to Show Params, Show HTML, Show Cookies and Show Java.
Under normal circumstances the browser provides a feature to view HTML source. For Microsoft Internet Explorer this is “Source” under the View menu. For Firefox this is “Page Source” under the view menu. The Show HTML feature of WebGoat shows only the HTML that is relevant for the current lesson. This view does not include HTML for side and top bars.
Parameters and cookies display in red.
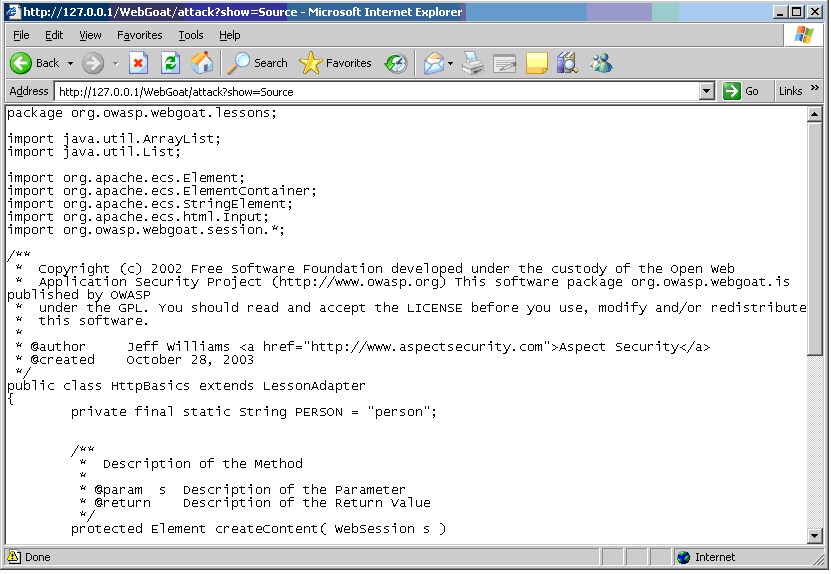
Show Java will open a new window containing source code.