This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "JBroFuzz"
| Line 1: | Line 1: | ||
| + | [[Image:OWASP Inactive Banner.jpg|1155px]] | ||
==== Main ==== | ==== Main ==== | ||
Revision as of 02:03, 23 January 2014
Main
This project is currently inactive. If you would like more information on the OWASP JBroFuzz Project, please contact Samantha Groves at [email protected].
JBroFuzz is a web application fuzzer for requests being made over HTTP or HTTPS. Its purpose is to provide a single, portable application that offers stable web protocol fuzzing capabilities.
Current version is 2.4. Get it from the SourceForge Download Section.
Release Notes (2.4):
- Commandline support - main class analyzing and executing the commandline options
- Added --no-execute option to command line support
- Added "Connection: close" preference option to be added to the headers automatically
- Massive UI revamp for Fuzzing Tab: Contains 3 Sub-Tabs: Input, Output, On the wire
- Introduction of Fuzzing Transforms for those double-URL, triple-Base64 encodings
- Added HTTP proxy support & authentication for checking updates
- EncoderHashWindow improvements in keeping history within different row selections
- Fixed ZBase32 Encoding/Decoding to work as Phil wants it to
- Prefix/Suffix in Fuzzer Transforms: http://www.owasp.org/index.php/OWASP_JBroFuzz_Tutorial#Added_Fuzzer_Transformations
- Added a plain-text encoder, similar to Zero-Fuzzer for theoretical completeness
- Fixed a bunch of supposed "security holes" reported by static analyzers
- Small Oracle payloads update
Vulnerability Identification
JBroFuzz generates requests, puts them on the wire and records the corresponding responses received back. It does not attempt to identify if a particular site is vulnerable or not; this requires further human analysis.
However, certain payloads included in fuzzers that can be used to generate requests (e.g. XSS) are crafted to attempt to successfully exploit flaws. Such flaws represent previously known vulnerabilities for web applications. JBroFuzz groups fuzzers with their corresponding payloads into a number of categories, depending on previously known vulnerabilities.
Thus, the human analyst would have to select the fuzzers to use in order to test against a particular set of vulnerabilities and review the results in order to recognize if exploitation succeeded or not.
JBroFuzz Documentation
Online Documentation
Frequently Asked Questions (FAQs)
Built-in Documentation
Frequently Asked Questions: Help -> FAQ
Help Topics: Help -> Topics
Application Overview
The components of JBroFuzz are presented into tabs, with more options (encodings, hash calculator, headers from popular browsers) available under the Tools option. The basic components are:
Fuzzing The fuzzing tab is the main tab of JBroFuzz, responsible for all fuzzing operations performed over the network. Depending on the fuzzer payloads selected, it creates the malformed data for each request, puts it on the wire and writes the response to a file.
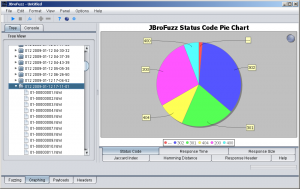
Graphing The graphing tab is responsible for graphing (in a variety of forms) the responses received while fuzzing. This tab can offer a clear indication of a response that is different then the rest received, an indication of further examination being required.
Payloads The payloads tab is a collection of fuzzers with their corresponding payloads that can be used while fuzzing. Payloads are added to the request in the fuzzing tab; a more clear view of what payloads are available, how they are grouped and what properties each fuzzer has can be seen in this tab.
Headers The headers window is a collection of browser headers that can be used while fuzzing. Headers are obtained from different browsers on different platforms and operating systems. This tab is provided, as many web applications respond differently to different browser impersonation attacks.
System The system tab represents the logging console of JBroFuzz at runtime. Here you can access java runtime information, see any errors that might occur and also track operation in terms of events being logged.
Roadmap
Building a web application fuzzer that sits at the rim of breaking known protocol specifications, can be a very time consuming exercise. Thus, JBroFuzz has a roadmap, based on how much time it would take to achieve each task.
You can find the project roadmap here.
Source Code
JBroFuzz is written in Java and requires a 1.6 JRE/JDK (or higher) installed, to run. It is constituted of more or less 70 classes, using, in total, 10 external libraries. It builds under Apache Ant.
SVN (Subversion) is a tool used by many software developers to manage changes within their source code tree. This project's SourceForge.net Subversion repository can be checked out through SVN with the following instruction set:
svn co https://jbrofuzz.svn.sourceforge.net/svnroot/jbrofuzz jbrofuzz
If the above sounds a bit greek, you can also browse through the complete source code at:
http://jbrofuzz.svn.sourceforge.net/viewvc/jbrofuzz/
Feedback and Participation
We hope you find the OWASP JBroFuzz Project useful. Please contribute to the project by volunteering for one of the tasks on the roadmap, sending your comments, questions, and suggestions to [email protected].
To join the OWASP JBroFuzz Project mailing list or view the archives, please visit the subscription page.
Project About
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||