This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
File list
This special page shows all uploaded files.
| Date | Name | Thumbnail | Size | Description | Versions |
|---|---|---|---|---|---|
| 16:11, 11 July 2013 | Secrets-as-a-Service.pdf (file) | 3.39 MB | Matt Tesauro (and Jarret Raim)'s presentation on cloud-based key management in OpenStack. Presented at OWASP San Antonio on Wednesday July 10th, 2013. | 1 | |
| 08:14, 1 August 2008 | Asmm levels small.png (file) |  |
15 KB | Application Security Maturity Model (ASMM) levels diagram. This is the small version. | 1 |
| 08:04, 1 August 2008 | Asmm levels.png (file) | 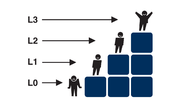 |
30 KB | Application Security Maturity Model (ASMM) basic levels graphic. | 1 |
| 12:26, 13 September 2007 | Fortify-bjenkins-AppSecStrategy-20070906.pdf (file) | 1.55 MB | Category:OWASP Presentations Over the past decade, the Department of Defense in general, and the US Air Force in particular, has transformed itself to better deal with 21st century warfare. The Air Force in fact has modified its stated mission to incl | 1 | |
| 10:26, 7 November 2006 | ExampleAtlasPage.PNG (file) |  |
97 KB | 2 | |
| 10:15, 7 November 2006 | ExampleAtlasRequest.jpg (file) |  |
30 KB | 1 | |
| 05:18, 20 October 2006 | OWASPSanAntonio 2006 09 AgileAndSecure.pdf (file) | 588 KB | Category:OWASP Presentations Software development organizations find themselves being pulled in two directions. Agile software development methodologies such as eXtreme Programming and Scrum have allowed organizations to be more responsive to busines | 1 | |
| 05:06, 20 October 2006 | OWASPSanAntonio 20040922.pdf (file) | 28 KB | Category:OWASP Presentations Basic overview of OWASP and the various projects. Used as the inaugural OWASP meeting for the San Antonio chapter. | 1 | |
| 13:32, 30 August 2006 | DenimGroup AJAXSecurityHereWeGoAgain Content 20060829.pdf (file) | 188 KB | Category:OWASP Presentations Abstract: AJAX (or Asynchronous JavaScript And XML) is the hot new web programming technique being used to create rich Internet applications. By interacting with the server behind the scenes and updating web page DOMs, AJ | 1 | |
| 13:41, 24 August 2006 | OWASPSanAntonio 2006 08 SingleSignOn.ppt (file) | 413 KB | Category:OWASP Presentations Presentation given to OWASP San Antonio on August 23, 2006 by Vijay Kumar. Abstract: Scattered software applications with differing security policies are a bane of today’s IT departments, consuming a large chunk of supp | 1 | |
| 13:25, 10 July 2006 | OWASPSanAntonio 2006 05 ForcefulBrowsing Content.pdf (file) | 59 KB | Category:OWASP Presentations By Forceful Browsing, clients may be able to access pages which should be forbidden. A technique for preventing forceful browsing is introduced. With this technique, you may be assured that clients may only visit pages f | 1 | |
| 13:11, 10 July 2006 | OWASPSanAntonio 2006 06 Crypto Content.pdf (file) | 429 KB | Cryptography Transitions are defined as "Managing the passage from one cryptographic architecture to another in a methodical approach that is consistent with prudent business practices and security guidelines." This talk will first discuss the technology | 1 |