This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Projects/OWASP XSSER"
(Created page with "{{Template:Project About | project_name =OWASP XSSER | project_home_page =OWASP_XSSER | project_description =Cross Site "Scripter" (XSSer) is an automatic -framework- to detec...") |
|||
| Line 1: | Line 1: | ||
| − | + | [[Category:OWASP Project]] | |
| − | + | {{Social Media Links}}<br> | |
| − | |||
| − | |||
| − | It contains several options to try to bypass certain filters, and various special techniques of code injection. | + | ---- |
| − | | | + | {| style="width:100%" border="0" align="center" |
| − | | | + | ! colspan="8" align="center" style="background:#4058A0; color:white"|<font color="white">'''OWASP XSSer Project'''<br>Web application vulnerability scanner / Security auditor |
| − | | | + | |- |
| − | | | + | | style="width:15%; background:#7B8ABD" align="center"|'''Project Name''' |
| − | | | + | | colspan="7" style="width:85%; background:#cccccc" align="left"|<font color="black">'''XSSer: The Cross Site Scripting Framework''' |
| − | + | |- | |
| + | | style="width:15%; background:#7B8ABD" align="center"| '''Short Project Description''' | ||
| + | | colspan="7" style="width:85%; background:#cccccc" align="left"| | ||
| + | Cross Site "Scripter" is an automatic -framework- to detect, exploit and report XSS vulnerabilities in web-based applications. It contains several options to try to bypass certain filters, and various special techniques of code injection. | ||
| + | |- | ||
| + | | style="width:15%; background:#7B8ABD" align="center"|'''Key Project Information''' | ||
| + | | style="width:14%; background:#cccccc" align="center"|Project Leader<br>[[User:Epsylon|'''psy''']] | ||
| + | | style="width:14%; background:#cccccc" align="center"|Roadmap <br>[http://xsser.sourceforge.net/xsser/xsser-roadmap.pdf '''Next Version'''] | ||
| + | | style="width:14%; background:#cccccc" align="center"|Mailing List<br>[https://lists.owasp.org/mailman/listinfo/owasp_xsser '''Subscribe'''] - [mailto:owasp_xsser@lists.owasp.org '''Use'''] | ||
| + | | style="width:14%; background:#cccccc" align="center"|License<br>[http://gplv3.fsf.org/ '''GNU GPLv3'''] | ||
| + | | style="width:14%; background:#cccccc" align="center"|Project Type<br>[[:Category:OWASP_Project#Alpha_Status_Projects|'''Pentesting tool''']] | ||
| + | | style="width:15%; background:#cccccc" align="center"|Support<br>[http://www.nlnet.nl/news/2010/20100623-awards.html '''NLNet Awards''']<br>[http://en.wikipedia.org/wiki/OWASP '''OWASP tool'''] | ||
| + | |} | ||
| + | {| style="width:100%" border="0" align="center" | ||
| + | ! align="center" style="background:#7B8ABD; color:white"|<font color="black">'''Release Status''' | ||
| + | ! align="center" style="background:#7B8ABD; color:white"|<font color="black">'''Main Links''' | ||
| + | ! align="center" style="background:#7B8ABD; color:white"|<font color="black">'''Related Documentation''' | ||
| + | |- | ||
| + | | style="width:29%; background:#cccccc" align="center"|[http://sourceforge.net/projects/xsser/files/latest/download '''v1.6b - "Grey Swarm"'''] | ||
| + | | style="width:42%; background:#cccccc" align="center"|[http://xsser.sf.net '''SF Website'''] <br> [http://sourceforge.net/projects/xsser/files/ '''Code Releases'''] | ||
| + | | style="width:29%; background:#cccccc" align="center"| Paper: 'XSS for fun and profit':<br>[http://xsser.sourceforge.net/xsser/XSS_for_fun_and_profit_SCG09_(english).pdf '''English'''] - [http://xsser.sourceforge.net/xsser/XSS_for_fun_and_profit_SCG09_(spanish).pdf '''Spanish'''] | ||
| + | |} | ||
| + | ---- | ||
| + | =Current Version= | ||
| + | |||
| + | <table> | ||
| + | <tr> | ||
| + | <td>XSSer v1.6b ("The Mosquito: <u>Grey Swarm!</u>")<br><br> | ||
| + | [[Image:xsser-greyswarm_sm.png]]<br> | ||
| + | [[http://xsser.sf.net/xsser/xsser-greyswarm.png '''+ Click for Zoom''']]<br> | ||
| + | |||
| + | <ul> | ||
| + | <li>Download original source code: [http://sourceforge.net/projects/xsser/files/xsser_1.6-1.tar.gz/download '''XSSer v1.6 -beta-''']</li> | ||
| + | <li>Ubuntu/Debian package: [http://xsser.sf.net/xsser/xsser-1.6_all.deb.tar.gz '''XSSer-1.6_all.deb''']</li> | ||
| + | <li>ArchLinux package: [http://aur.archlinux.org/packages.php?ID=43447 '''AUR link (v1.6b)''']</li> | ||
| + | <li>Gentoo package: [http://perso.ikujam.org/xsser-1.6.1-ebuild.tar.gz '''XSSer Gentoo ebuild (v1.6b)''']</li> | ||
| + | <li>RPM package: [http://xsser.sf.net/xsser/xsser-1.6-1.noarch.rpm.tar.gz '''XSSer-1.6-1.noarch.rpm''']</li> | ||
| + | <li>Or update your copy directly from the XSSer -Subversion- repository:</li> | ||
| + | |||
| + | <u>$ svn co https://xsser.svn.sourceforge.net/svnroot/xsser xsser</u><br><br> | ||
| + | |||
| + | </ul> | ||
| + | This version include more features on the GTK+ interface: | ||
| + | </td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td> | ||
| + | <table> | ||
| + | <tr> | ||
| + | |||
| + | <td> | ||
| + | [[Image:xsser-greyswarm-donate_sm.png]]<br> | ||
| + | [[http://xsser.sf.net/xsser/xsser-greyswarm-donate.png '''+ Click for Zoom''']]<br> | ||
| + | </td> | ||
| + | |||
| + | <td> | ||
| + | [[Image:xsser-greyswarm-map_sm.png]]<br> | ||
| + | [[http://xsser.sf.net/xsser/xsser-greyswarm-map.png '''+ Click for Zoom''']]<br> | ||
| + | </td> | ||
| + | </tr> | ||
| + | |||
| + | <tr> | ||
| + | <td> | ||
| + | [[Image:xsser-greyswarm-check_sm.png]]<br> | ||
| + | [[http://xsser.sf.net/xsser/xsser-greyswarm-check.png '''+ Click for Zoom''']]<br> | ||
| + | </td> | ||
| + | |||
| + | <td> | ||
| + | [[Image:xsser-greyswarm-conn_sm.png]]<br> | ||
| + | [[http://xsser.sf.net/xsser/xsser-greyswarm-conn.png '''+ Click for Zoom''']]<br> | ||
| + | </td> | ||
| + | |||
| + | </tr> | ||
| + | </table> | ||
| + | </td> | ||
| + | </tr> | ||
| + | </table> | ||
| + | TIP: type: 'xsser --gtk' to start from shell. Or run directly XSSer from menu [[Image:xssericon_32x32.png]] | ||
| + | |||
| + | =Installation= | ||
| + | |||
| + | <p> | ||
| + | XSSer runs on many platforms. It requires Python and the following libraries:<br><br> | ||
| + | |||
| + | - python-pycurl - Python bindings to libcurl<br> | ||
| + | |||
| + | - python-beautifulsoup - error-tolerant HTML parser for Python<br> | ||
| + | - python-libxml2 - Python bindings for the GNOME XML library<br> | ||
| + | - python-geoip - Python bindings for the GeoIP IP-to-country resolver library<br><br> | ||
| + | |||
| + | On Debian-based systems (ex: Ubuntu), run: <br><br> | ||
| + | |||
| + | sudo apt-get install python-pycurl python-beautifulsoup python-libxml2 python-geoip | ||
| + | </p> | ||
| + | |||
| + | =How to Use= | ||
| + | |||
| + | xsser [OPTIONS] [-u |-i |-d ] [-g |-p |-c ] [Request(s)] [Vector(s)] [Bypasser(s)] [Technique(s)] [Final Injection(s)] | ||
| + | |||
| + | [http://xsser.sourceforge.net/#usage '''Usage'''] <br> | ||
| + | [http://xsser.sourceforge.net/#examples '''Examples'''] <br> | ||
| + | [http://xsser.sourceforge.net/#docs '''Documentation'''] <br> | ||
| + | [http://xsser.sourceforge.net/#screenshots '''Screenshots'''] <br> | ||
| + | [http://xsser.sourceforge.net/#videotutorials '''Videos'''] <br> | ||
| + | |||
| + | =Changelog= | ||
| + | |||
| + | '''November, 28, 2011:'''<br> | ||
| + | |||
| + | Core: Added Drop Cookie option + Added Random IP X-Forwarded-For option + Random X-Client-IP option + Added GSS and NTLM authentication methods + Added Ignore proxy option + Added TCP-NODELAY option + Added Follow redirects option + Added Follow redirects limiter parameter + Added Auto-HEAD precheck system + Added No-HEAD option + Added Isalive option + Added Check at url option (Blind XSS) + Added Reverse Check parameter + Added PHPIDS (v.0.6.5) exploit + Added More vectors to auto-payloading + Added HTML5 studied vectors + Fixed Different bugs on core + Fixed Curl handlerer options + Fixed Dorkerers system + Fixed Bugs on results propagation + Fixed POST requests.<br> | ||
| + | |||
| + | GTK: Added New features to GTK controller + Added Detailed views to GTK interface.<br><br> | ||
| + | |||
| + | '''February, 25, 2011:'''<br> | ||
| + | |||
| + | Added package for Archlinux.<br><br> | ||
| + | |||
| + | '''February, 24, 2011:'''<br> | ||
| + | |||
| + | Core: Added GTK option + Heuristic test + HTTP Response Splitting (ak.a Induced attack!) + DoS (Server) injection + Final code (added DCP & DOM injections) + Update option + Code clean + Bugfixing + New options menu + More advanced statistics system + Updated dorkerers list.<br> | ||
| + | |||
| + | GTK: Intuitive navigation + Wizard helper ("build your pentesting answering some questions") + Expert visor (with target(s) geolocation included + Documentation.<br><br> | ||
| + | |||
| + | '''November, 13, 2010:'''<br> | ||
| + | |||
| + | XSSer package for Archlinux can be found in the AUR.<br><br> | ||
| + | |||
| + | '''November, 11, 2010:'''<br> | ||
| + | |||
| + | Created XSSer package (v1.0) for Ubuntu/Debian based systems.<br><br> | ||
| + | |||
| + | '''November, 9, 2010:'''<br> | ||
| + | |||
| + | Added more advanced statistics results + Bugfixig.<br><br> | ||
| + | |||
| + | '''November, 7, 2010:'''<br> | ||
| + | |||
| + | Added "final remote injections" option + Cross Flash Attack! + Cross Frame Scripting + Data Control Protocol Injections + Base64 (rfc2397) PoC + OnMouseMove PoC + Browser launcher + Code clean + Bugfixing + New options menu + Pre-check system + Crawler spidering clones + More advanced statistics system + "Mana" output results.<br><br> | ||
| + | |||
| + | '''October, 8, 2010:'''<br> | ||
| + | |||
| + | POC: Detecting, exploiting and reporting "fcgi-bin/echo" Oracle vulnerability with XSSer<br> | ||
| + | |||
| + | ./XSSer -d "'inurl:fcgi-bin/echo'" --De "google" --proxy "http://127.0.0.1:8118" -s --tweet<br> | ||
| + | |||
| + | Results of the -botnet- attack in real time:<br> | ||
| + | |||
| + | - http://identi.ca/xsserbot01<br> | ||
| + | - http://twitter.com/xsserbot01<br><br> | ||
| + | |||
| + | Reported: apróx. 3.000 websites vulnerables (XSSer storm!!).<br><br> | ||
| + | |||
| + | '''September 22, 2010:'''<br> | ||
| + | |||
| + | Added a-xml exporter + ImageXSS + New dorker engines (total 10) + Core clean + Bugfixing + Social Networking XSS auto-publisher + Started -federated- XSS (full disclosure) pentesting botnet.<br> | ||
| + | |||
| + | http://identi.ca/xsserbot01<br> | ||
| + | http://twitter.com/xsserbot01<br><br> | ||
| + | |||
| + | '''August 20, 2010:'''<br> | ||
| + | |||
| + | Added attack payloads to auto-payloader (26 new injections) + POST + Statistics + URL Shorteners + IP Octal + Post-processing payloading + DOM Shadows! + Cookie injector + Browser DoS (Denegation of Service).<br><br> | ||
| + | |||
| + | '''July 1, 2010:'''<br> | ||
| + | |||
| + | Dorking + Crawling + IP DWORD + Core clean.<br><br> | ||
| + | |||
| + | '''April 19, 2010:'''<br> | ||
| + | |||
| + | HTTPS implemented + patched bugs.<br><br> | ||
| + | |||
| + | '''March 22, 2010:'''<br> | ||
| + | |||
| + | Added "inject your own payload" option. Can be used with all character encoding -bypassers- of XSSer.<br><br> | ||
| + | |||
| + | '''March 18, 2010:'''<br> | ||
| + | |||
| + | Added attack payloads to auto-payloader (62 different XSS injections).<br><br> | ||
| + | |||
| + | '''March 16, 2010:'''<br> | ||
| + | |||
| + | Added new payload encoders to bypass filters. <br><br> | ||
| + | |||
| + | =Roadmap= | ||
| + | |||
| + | Download roadmap planning: [https://xsser.sourceforge.net/xsser/xsser-roadmap.pdf '''Next Version'''] | ||
| + | |||
| + | =Contact= | ||
| + | |||
| + | '''Irc:''' | ||
| + | |||
| + | * irc.freenode.net - channel: ''#xsser'' | ||
| + | |||
| + | '''Mailing lists:''' | ||
| + | |||
| + | * Owasp: [https://lists.owasp.org/mailman/listinfo/owasp_xsser '''Subscribe'''] [mailto:owasp_xsser@lists.owasp.org '''Write'''] | ||
| + | |||
| + | * Sourceforge: [https://lists.sourceforge.net/lists/listinfo/xsser-users '''Subscribe'''] [mailto:xsser-users@lists.sourceforge.net '''Write'''] | ||
| + | |||
| + | '''Project Leader:''' | ||
| + | |||
| + | GPG ID: ''0xB8AC3776'' | ||
| + | |||
| + | * Website: | ||
| + | o [http://lordepsylon.net '''http://lordepsylon.net'''] | ||
| + | |||
| + | * Email: | ||
| + | o [mailto:root@lordepsylon.net '''psy'''] | ||
| + | o [mailto:epsylon@riseup,net '''epsylon'''] | ||
| + | |||
| + | * Microblogging: | ||
| + | o [https://identi.ca/psy '''identi.ca'''] | ||
| + | o [https://twitter.com/lord_epsylon '''twitter.com'''] | ||
Revision as of 17:15, 10 September 2012
| OWASP XSSer Project Web application vulnerability scanner / Security auditor | |||||||
|---|---|---|---|---|---|---|---|
| Project Name | XSSer: The Cross Site Scripting Framework | ||||||
| Short Project Description |
Cross Site "Scripter" is an automatic -framework- to detect, exploit and report XSS vulnerabilities in web-based applications. It contains several options to try to bypass certain filters, and various special techniques of code injection. | ||||||
| Key Project Information | Project Leader psy |
Roadmap Next Version |
Mailing List Subscribe - Use |
License GNU GPLv3 |
Project Type Pentesting tool |
Support NLNet Awards OWASP tool | |
| Release Status | Main Links | Related Documentation |
|---|---|---|
| v1.6b - "Grey Swarm" | SF Website Code Releases |
Paper: 'XSS for fun and profit': English - Spanish |
Current Version
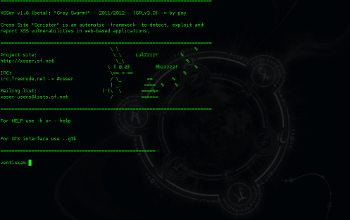
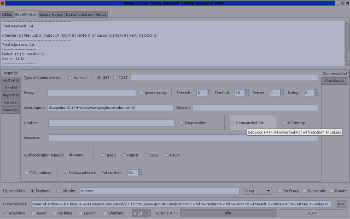
XSSer v1.6b ("The Mosquito: Grey Swarm!")
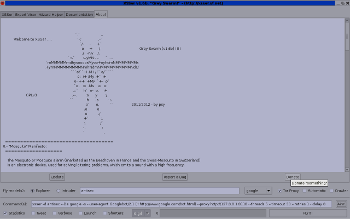
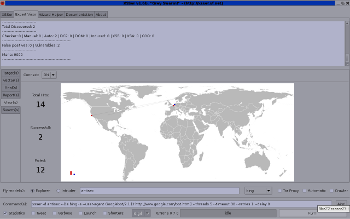
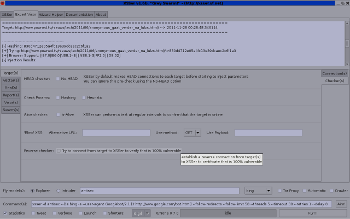
$ svn co https://xsser.svn.sourceforge.net/svnroot/xsser xsser This version include more features on the GTK+ interface: |
||||
|
|
TIP: type: 'xsser --gtk' to start from shell. Or run directly XSSer from menu ![]()
Installation
XSSer runs on many platforms. It requires Python and the following libraries:
- python-pycurl - Python bindings to libcurl
- python-beautifulsoup - error-tolerant HTML parser for Python
- python-libxml2 - Python bindings for the GNOME XML library
- python-geoip - Python bindings for the GeoIP IP-to-country resolver library
On Debian-based systems (ex: Ubuntu), run:
sudo apt-get install python-pycurl python-beautifulsoup python-libxml2 python-geoip
How to Use
xsser [OPTIONS] [-u |-i |-d ] [-g |-p |-c ] [Request(s)] [Vector(s)] [Bypasser(s)] [Technique(s)] [Final Injection(s)]
Usage
Examples
Documentation
Screenshots
Videos
Changelog
November, 28, 2011:
Core: Added Drop Cookie option + Added Random IP X-Forwarded-For option + Random X-Client-IP option + Added GSS and NTLM authentication methods + Added Ignore proxy option + Added TCP-NODELAY option + Added Follow redirects option + Added Follow redirects limiter parameter + Added Auto-HEAD precheck system + Added No-HEAD option + Added Isalive option + Added Check at url option (Blind XSS) + Added Reverse Check parameter + Added PHPIDS (v.0.6.5) exploit + Added More vectors to auto-payloading + Added HTML5 studied vectors + Fixed Different bugs on core + Fixed Curl handlerer options + Fixed Dorkerers system + Fixed Bugs on results propagation + Fixed POST requests.
GTK: Added New features to GTK controller + Added Detailed views to GTK interface.
February, 25, 2011:
Added package for Archlinux.
February, 24, 2011:
Core: Added GTK option + Heuristic test + HTTP Response Splitting (ak.a Induced attack!) + DoS (Server) injection + Final code (added DCP & DOM injections) + Update option + Code clean + Bugfixing + New options menu + More advanced statistics system + Updated dorkerers list.
GTK: Intuitive navigation + Wizard helper ("build your pentesting answering some questions") + Expert visor (with target(s) geolocation included + Documentation.
November, 13, 2010:
XSSer package for Archlinux can be found in the AUR.
November, 11, 2010:
Created XSSer package (v1.0) for Ubuntu/Debian based systems.
November, 9, 2010:
Added more advanced statistics results + Bugfixig.
November, 7, 2010:
Added "final remote injections" option + Cross Flash Attack! + Cross Frame Scripting + Data Control Protocol Injections + Base64 (rfc2397) PoC + OnMouseMove PoC + Browser launcher + Code clean + Bugfixing + New options menu + Pre-check system + Crawler spidering clones + More advanced statistics system + "Mana" output results.
October, 8, 2010:
POC: Detecting, exploiting and reporting "fcgi-bin/echo" Oracle vulnerability with XSSer
./XSSer -d "'inurl:fcgi-bin/echo'" --De "google" --proxy "http://127.0.0.1:8118" -s --tweet
Results of the -botnet- attack in real time:
- http://identi.ca/xsserbot01
- http://twitter.com/xsserbot01
Reported: apróx. 3.000 websites vulnerables (XSSer storm!!).
September 22, 2010:
Added a-xml exporter + ImageXSS + New dorker engines (total 10) + Core clean + Bugfixing + Social Networking XSS auto-publisher + Started -federated- XSS (full disclosure) pentesting botnet.
http://identi.ca/xsserbot01
http://twitter.com/xsserbot01
August 20, 2010:
Added attack payloads to auto-payloader (26 new injections) + POST + Statistics + URL Shorteners + IP Octal + Post-processing payloading + DOM Shadows! + Cookie injector + Browser DoS (Denegation of Service).
July 1, 2010:
Dorking + Crawling + IP DWORD + Core clean.
April 19, 2010:
HTTPS implemented + patched bugs.
March 22, 2010:
Added "inject your own payload" option. Can be used with all character encoding -bypassers- of XSSer.
March 18, 2010:
Added attack payloads to auto-payloader (62 different XSS injections).
March 16, 2010:
Added new payload encoders to bypass filters.
Roadmap
Download roadmap planning: Next Version
Contact
Irc:
* irc.freenode.net - channel: #xsser
Mailing lists:
* Owasp: Subscribe Write
* Sourceforge: Subscribe Write
Project Leader:
GPG ID: 0xB8AC3776
* Website:
o http://lordepsylon.net
* Email:
o psy
o epsylon
* Microblogging:
o identi.ca
o twitter.com