This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Category:OWASP Top Ten Project"
(more 2017 cleanup) |
(removed 2017 RC tab) |
||
| Line 79: | Line 79: | ||
|} | |} | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
= OWASP Top 10 for 2013 = | = OWASP Top 10 for 2013 = | ||
Revision as of 22:57, 19 November 2017
- Main
- OWASP Top 10 for 2013
- OWASP Top 10 for 2010
- Translation Efforts
- Project Details
- Some Commercial & OWASP Uses of the Top 10
OWASP Top 10 2017 ReleasedThe OWASP Top 10 - 2017 will be available for download on 20 November, 2017. We are asking for comments to be submitted on the project's GitHub issues. OWASP Top 10 Most Critical Web Application Security RisksThe OWASP Top 10 is a powerful awareness document for web application security. It represents a broad consensus about the most critical security risks to web applications. Project members include a variety of security experts from around the world who have shared their expertise to produce this list. We urge all companies to adopt this awareness document within their organization and start the process of ensuring that their web applications minimize these risks. Adopting the OWASP Top 10 is perhaps the most effective first step towards changing the software development culture within your organization into one that produces secure code. Translation EffortsThe OWASP Top 10 has been translated to many different languages by numerous volunteers. These translations are available as follows:
LicensingThe OWASP Top 10 is free to use. It is licensed under the http://creativecommons.org/licenses/by-sa/3.0/ Creative Commons Attribution-ShareAlike 3.0 license, so you can copy, distribute and transmit the work, and you can adapt it, and use it commercially, but all provided that you attribute the work and if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one. Related ProjectsProject SponsorsThe OWASP Top 10 - 2017 project is sponsored by Thanks to Aspect Security for sponsoring earlier versions. |
Quick Download
Get Involved
News and Events
Project LeadersClassifications
| |||||||
On June 12, 2013 the OWASP Top 10 for 2013 was officially released. This version was updated based on numerous comments received during the comment period after the release candidate was released in Feb. 2013.
- OWASP Top 10 2013 document (PDF).
- OWASP Top 10 2013 - Wiki.
- OWASP Top 10 2013 - Arabic (PDF).
- OWASP Top 10 2013 - Chinese (PDF).
- OWASP Top 10 2013 - Czech (PDF).
- OWASP Top 10 2013 - French (PDF).
- OWASP Top 10 2013 - German (PDF)
- OWASP Top 10 2013 - Hebrew (PDF)
- OWASP Top 10 2013 - Italian (PDF)
- OWASP Top 10 2013 - Japanese (PDF).
- OWASP Top 10 2013 - Korea (PDF).
- OWASP Top 10 2013 - Brazilian Portuguese (PDF).
- OWASP Top 10 2013 - Spanish (PDF)
- OWASP Top 10 2013 - Ukrainian (PDF)
- OWASP Top 10 2013 Presentation - Presenting Each Item in the Top 10 (PPTX).
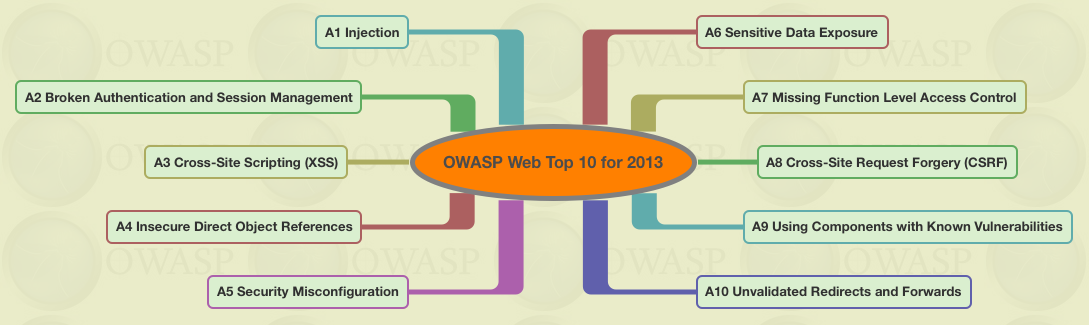
For 2013, the OWASP Top 10 Most Critical Web Application Security Risks are:
- A1 Injection
- A2 Broken Authentication and Session Management
- A3 Cross-Site Scripting (XSS)
- A4 Insecure Direct Object References
- A5 Security Misconfiguration
- A6 Sensitive Data Exposure
- A7 Missing Function Level Access Control
- A8 Cross-Site Request Forgery (CSRF)
- A9 Using Components with Known Vulnerabilities
- A10 Unvalidated Redirects and Forwards
If you are interested, the methodology for how the Top 10 is produced is now documented here: OWASP Top 10 Development Methodology
Please help us make sure every developer in the ENTIRE WORLD knows about the OWASP Top 10 by helping to spread the word!!!
As you help us spread the word, please emphasize:
- OWASP is reaching out to developers, not just the application security community
- The Top 10 is about managing risk, not just avoiding vulnerabilities
- To manage these risks, organizations need an application risk management program, not just awareness training, app testing, and remediation
We need to encourage organizations to get off the penetrate and patch mentality. As Jeff Williams said in his 2009 OWASP AppSec DC Keynote: “we’ll never hack our way secure – it’s going to take a culture change” for organizations to properly address application security.
Introduction
The OWASP Top 10 is a powerful awareness document for web application security. It represents a broad consensus about the most critical security risks to web applications. Project members include a variety of security experts from around the world who have shared their expertise to produce this list. Versions of the 2007 and 2010 version were translated into English, French, Spanish, Japanese, Korean and Turkish and other languages. The 2013 version was translated into even more languages.
We urge all companies to adopt this awareness document within their organization and start the process of ensuring that their web applications minimize these risks. Adopting the OWASP Top 10 is perhaps the most effective first step towards changing the software development culture within your organization into one that produces secure code.
Changes between 2010 and 2013 Editions
The OWASP Top 10 - 2013 includes the following changes as compared to the 2010 edition:
- A1 Injection
- A2 Broken Authentication and Session Management (was formerly 2010-A3)
- A3 Cross-Site Scripting (XSS) (was formerly 2010-A2)
- A4 Insecure Direct Object References
- A5 Security Misconfiguration (was formerly 2010-A6)
- A6 Sensitive Data Exposure (2010-A7 Insecure Cryptographic Storage and 2010-A9 Insufficient Transport Layer Protection were merged to form 2013-A6)
- A7 Missing Function Level Access Control (renamed/broadened from 2010-A8 Failure to Restrict URL Access)
- A8 Cross-Site Request Forgery (CSRF) (was formerly 2010-A5)
- A9 Using Components with Known Vulnerabilities (new but was part of 2010-A6 – Security Misconfiguration)
- A10 Unvalidated Redirects and Forwards
Other 2013 Top 10 Docs
- OWASP Top 10 - 2013 - Release Candidate
- OWASP Top 10 - 2013 - Final Release - Change Log (docx)
- Focusing on What Changed Since 2010 (PPTX)
Feedback
Please let us know how your organization is using the OWASP Top 10. Include your name, organization's name, and brief description of how you use the list. Thanks for supporting OWASP!
We hope you find the information in the OWASP Top 10 useful. Please contribute back to the project by sending your comments, questions, and suggestions to [email protected]. Thanks!
To join the OWASP Top 10 mailing list or view the archives, please visit the subscription page.
Project Sponsors
The OWASP Top 10 project is sponsored by 
On April 19, 2010 the final version of the OWASP Top 10 for 2010 was released, and here is the associated press release. This version was updated based on numerous comments received during the comment period after the release candidate was released in Nov. 2009.
- OWASP Top 10 - 2010 Document
- OWASP Top 10 - 2010 - wiki
- OWASP Top 10 - 2010 Presentation
- OWASP Top 10 Video of the Presentation above - this focused alot on the Top 10 for 2010 approach, rather than the details. (From OWASP AppSec EU 2010)
- OWASP Top 10 Video of this Presentation when the Top 10 for 2010 was 1st released for comment - this goes through each item in the Top 10. (From OWASP AppSec DC 2009)
For 2010, the OWASP Top 10 Most Critical Web Application Security Risks are:
- A1: Injection
- A2: Cross-Site Scripting (XSS)
- A3: Broken Authentication and Session Management
- A4: Insecure Direct Object References
- A5: Cross-Site Request Forgery (CSRF)
- A6: Security Misconfiguration
- A7: Insecure Cryptographic Storage
- A8: Failure to Restrict URL Access
- A9: Insufficient Transport Layer Protection
- A10: Unvalidated Redirects and Forwards
Introduction
The OWASP Top 10 is a powerful awareness document for web application security. It represents a broad consensus about the most critical security risks to web applications. Project members include a variety of security experts from around the world who have shared their expertise to produce this list. Versions of the 2007 were translated into English, French, Spanish, Japanese, Korean and Turkish and other languages and the 2010 version was translated into even more languages. See below for all the translated versions.
2010 Versions
2010 Edition:
2010 Translations:
- OWASP Top 10 2010 - Chinese PDF / 这里下载PDF格式文档
- OWASP Top 10 2010 - French PDF
- OWASP Top 10 2010 - German PDF
- OWASP Top 10 2010 - Hebrew PDF
- OWASP Top 10 2010 - Indonesian PDF
- OWASP Top 10 2010 - Italian PDF
- OWASP Top 10 2010 - Japanese PDF
- OWASP Top 10 2010 - Korean PDF
- OWASP Top 10 2010 - Spanish PDF
- OWASP Top 10 2010 - Spanish PPT
- OWASP Top 10 2010 - Vietnamese PDF
2010 Release Candidate:
- OWASP Top 10 2010 Release Candidate
- OWASP Top 10 2010 Release Candidate Comments, except for one set of scanned comments which are here.
Previous versions:
The 2017 RC1 has been rejected. There will be an RC2 coming out shortly. As RC2 may have significant changes from RC1, we suggest that you wait for RC2 before continuing your translation efforts.
If you are interested in helping, please contact the members of the team for the language you are interested in contributing to, or if you don't see your language listed, please email [email protected] to let us know that you want to help and we'll form a volunteer group for your language.
Here is the original source document for the OWASP Top 10 - 2017 Release Candidate which is in PowerPoint.
2017 Release Candidate Translation Teams:
- French: Ludovic Petit: [email protected], Sébastien Gioria: [email protected].
- Chinese: 王颉、包悦忠、Rip、顾凌志、王厚奎、王文君、吴楠、夏天泽、夏玉明、杨天识、袁明坤、张镇(排名不分先后,按姓氏拼音排列) OWASP Top10 2017 RC1 - Chinese PDF
- Azerbaijanian: Rashad Aliyev ([email protected])
- Others to be listed.
2013 Completed Translations:
- Arabic: OWASP Top 10 2013 - Arabic PDF Translated by: Mohannad Shahat: [email protected], Fahad: @SecurityArk, Abdulellah Alsaheel: [email protected], Khalifa Alshamsi: [email protected] and Sabri(KING SABRI): [email protected], Mohammed Aldossary: [email protected]
- Chinese 2013:中文版2013 OWASP Top 10 2013 - Chinese (PDF). 项目组长: Rip 王颉, 参与人员: 陈亮、 顾庆林、 胡晓斌、 李建蒙、 王文君、 杨天识、 张在峰
- Czech 2013: OWASP Top 10 2013 - Czech (PDF) OWASP Top 10 2013 - Czech (PPTX) CSIRT.CZ - CZ.NIC, z.s.p.o. (.cz domain registry): Petr Zavodsky: [email protected], Vaclav Klimes, Zuzana Duracinska, Michal Prokop, Edvard Rejthar, Pavel Basta
- French 2013: OWASP Top 10 2013 - French PDF Ludovic Petit: [email protected], Sébastien Gioria: [email protected], Erwan Abgrall: [email protected], Benjamin Avet: [email protected], Jocelyn Aubert: [email protected], Damien Azambour: [email protected], Aline Barthelemy: [email protected], Moulay Abdsamad Belghiti: [email protected], Gregory Blanc: [email protected], Clément Capel: [email protected], Etienne Capgras: [email protected], Julien Cayssol: [email protected], Antonio Fontes: [email protected], Ely de Travieso: [email protected], Nicolas Grégoire: [email protected], Valérie Lasserre: [email protected], Antoine Laureau: [email protected], Guillaume Lopes: [email protected], Gilles Morain: [email protected], Christophe Pekar: [email protected], Olivier Perret: [email protected], Michel Prunet: [email protected], Olivier Revollat: [email protected], Aymeric Tabourin: [email protected]
- German 2013: OWASP Top 10 2013 - German PDF [email protected] which is Frank Dölitzscher, Torsten Gigler, Tobias Glemser, Dr. Ingo Hanke, Thomas Herzog, Kai Jendrian, Ralf Reinhardt, Michael Schäfer
- Hebrew 2013: OWASP Top 10 2013 - Hebrew PDF Translated by: Or Katz, Eyal Estrin, Oran Yitzhak, Dan Peled, Shay Sivan.
- Italian 2013: OWASP Top 10 2013 - Italian PDF Translated by: Michele Saporito: [email protected], Paolo Perego: [email protected], Matteo Meucci: [email protected], Sara Gallo: [email protected], Alessandro Guido: [email protected], Mirko Guido Spezie: [email protected], Giuseppe Di Cesare: [email protected], Paco Schiaffella: [email protected], Gianluca Grasso: [email protected], Alessio D'Ospina: [email protected], Loredana Mancini: [email protected], Alessio Petracca: [email protected], Giuseppe Trotta: [email protected], Simone Onofri: [email protected], Francesco Cossu: [email protected], Marco Lancini: [email protected], Stefano Zanero: [email protected], Giovanni Schmid: [email protected], Igor Falcomata': [email protected]
- Japanese 2013: OWASP Top 10 2013 - Japanese PDF Translated by: Chia-Lung Hsieh: ryusuke.tw(at)gmail.com, Reviewed by: Hiroshi Tokumaru, Takanori Nakanowatari
- Korean 2013: OWASP Top 10 2013 - Korean PDF (이름가나다순) 김병효:[email protected], 김지원:[email protected], 김효근:[email protected], 박정훈:[email protected], 성영모:[email protected], 성윤기:[email protected], 송보영:[email protected], 송창기:[email protected], 유정호:[email protected], 장상민:[email protected], 전영재:[email protected], 정가람:[email protected], 정홍순:[email protected], 조민재:[email protected],허성무:[email protected]
- Brazilian Portuguese 2013: OWASP Top 10 2013 - Brazilian Portuguese PDF Translated by: Carlos Serrão, Marcio Machry, Ícaro Evangelista de Torres, Carlo Marcelo Revoredo da Silva, Luiz Vieira, Suely Ramalho de Mello, Jorge Olímpia, Daniel Quintão, Mauro Risonho de Paula Assumpção, Marcelo Lopes, Caio Dias, Rodrigo Gularte
- Spanish 2013: OWASP Top 10 2013 - Spanish PDF Gerardo Canedo: [email protected], Jorge Correa: [email protected], Fabien Spychiger: [email protected], Alberto Hill: [email protected], Johnatan Stanley: [email protected], Maximiliano Alonzo: [email protected], Mateo Martinez: [email protected], David Montero: [email protected], Rodrigo Martinez: [email protected], Guillermo Skrilec: [email protected], Felipe Zipitria: [email protected], Fabien Spychiger: [email protected], Rafael Gil: [email protected], Christian Lopez: [email protected], jonathan fernandez [email protected], Paola Rodriguez: [email protected], Hector Aguirre: [email protected], Roger Carhuatocto: [email protected], Juan Carlos Calderon: [email protected], Marc Rivero López: [email protected], Carlos Allendes: [email protected], [email protected]: [email protected], Manuel Ramírez: [email protected], Marco Miranda: [email protected], Mauricio D. Papaleo Mayada: [email protected], Felipe Sanchez: [email protected], Juan Manuel Bahamonde: [email protected], Adrià Massanet: [email protected], Jorge Correa: [email protected], Ramiro Pulgar: [email protected], German Alonso Suárez Guerrero: [email protected], Jose A. Guasch: [email protected], Edgar Salazar: [email protected]
- Ukrainian 2013: OWASP Top 10 2013 - Ukrainian PDF Kateryna Ovechenko, Yuriy Fedko, Gleb Paharenko, Yevgeniya Maskayeva, Sergiy Shabashkevich, Bohdan Serednytsky
2010 Completed Translations:
- Korean 2010: OWASP Top 10 2010 - Korean PDF Hyungkeun Park, ([email protected])
- Spanish 2010: OWASP Top 10 2010 - Spanish PDF *Daniel Cabezas Molina , Edgar Sanchez, Juan Carlos Calderon, Jose Antonio Guasch, Paulo Coronado, Rodrigo Marcos, Vicente Aguilera
- French 2010: OWASP Top 10 2010 - French PDF [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected]
- German: OWASP Top 10 2010 - German PDF [email protected] which is Frank Dölitzscher, Tobias Glemser, Dr. Ingo Hanke, Kai Jendrian, Ralf Reinhardt, Michael Schäfer
- Indonesian: OWASP Top 10 2010 - Indonesian PDF Tedi Heriyanto (coordinator), Lathifah Arief, Tri A Sundara, Zaki Akhmad
- Italian: OWASP Top 10 2010 - Italian PDF Simone Onofri, Paolo Perego, Massimo Biagiotti, Edoardo Viscosi, Salvatore Fiorillo, Roberto Battistoni, Loredana Mancini, Michele Nesta, Paco Schiaffella, Lucilla Mancini, Gerardo Di Giacomo, Valentino Squilloni
- Japanese: OWASP Top 10 2010 - Japanese PDF [email protected], Dr. Masayuki Hisada, Yoshimasa Kawamoto, Ryusuke Sakamoto, Keisuke Seki, Shin Umemoto, Takashi Arima
- Chinese: OWASP Top 10 2010 - Chinese PDF 感谢以下为中文版本做出贡献的翻译人员和审核人员: Rip Torn, 钟卫林, 高雯, 王颉, 于振东
- Vietnamese: OWASP Top 10 2010 - Vietnamese PDF Translation lead by Cecil Su - Translation Team: Dang Hoang Vu, Nguyen Ba Tien, Nguyen Tang Hung, Luong Dieu Phuong, Huynh Thien Tam
- Hebrew: OWASP Top 10 Hebrew Project -- OWASP Top 10 2010 - Hebrew PDF. Lead by Or Katz, see translation page for list of contributors.
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What does this OWASP project release offer you? | ||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| ||||||||||||||||||||||||||||||
Warning: these articles have not been rated for accuracy by OWASP. Product companies should be extremely careful about claiming to "cover" or "ensure compliance" with the OWASP Top 10. The current state-of-the-art for automated detection (scanners and static analysis) and prevention (WAF) is nowhere near sufficient to claim adequate coverage of the issues in the Top 10. Nevertheless, using the Top 10 as a simple way to communicate security to end users is effective.
- Microsoft
- as a way to measure the coverage of their SDL and improve security
- PCI Council
- as part of the Payment Card Industry Data Security Standard (PCI DSS)
- Microsoft
- to show how "T10 threats are handled by the security design and test procedures of Microsoft"
- OWASP
- OWASP Top 10 Mapped to the Web Hacking Incident Database
- OWASP
- OWASP Mobile Top 10 Risks
- OWASP
- OWASP Top 10 Cheat Sheet
Subcategories
This category has the following 2 subcategories, out of 2 total.
O
Pages in category "OWASP Top Ten Project"
The following 107 pages are in this category, out of 107 total.
A
- A1 2004 Unvalidated Input
- A10 2004 Insecure Configuration Management
- A2 2004 Broken Access Control
- A3 2004 Broken Authentication and Session Management
- A4 2004 Cross Site Scripting
- A5 2004 Buffer Overflow
- A6 2004 Injection Flaws
- A7 2004 Improper Error Handling
- A8 2004 Insecure Storage
- A9 2004 Application Denial of Service
- Access Control In Your J2EE Application
C
G
T
- Top 10 2004
- Top 10 2007
- Top 10 2007-Broken Authentication and Session Management
- Top 10 2007-Cross Site Request Forgery
- Top 10 2007-Cross Site Scripting
- Top 10 2007-Failure to Restrict URL Access
- Top 10 2007-Information Leakage and Improper Error Handling
- Top 10 2007-Injection Flaws
- Top 10 2007-Insecure Communications
- Top 10 2007-Insecure Cryptographic Storage
- Top 10 2007-Insecure Direct Object Reference
- Top 10 2007-Malicious File Execution
- Top 10 2007-Methodology
- Top 10 2007-References
- Top 10 2007-Where to Go From Here
- Top 10 2010
- Top 10 2010-A1-Injection
- Top 10 2010-A10-Unvalidated Redirects and Forwards
- Top 10 2010-A2-Cross-Site Scripting (XSS)
- Top 10 2010-A3-Broken Authentication and Session Management
- Top 10 2010-A4-Insecure Direct Object References
- Top 10 2010-A5-Cross-Site Request Forgery (CSRF)
- Top 10 2010-A6-Security Misconfiguration
- Top 10 2010-A7-Insecure Cryptographic Storage
- Top 10 2010-A8-Failure to Restrict URL Access
- Top 10 2010-A9-Insufficient Transport Layer Protection
- Top 10 2010-Main
- Top 10 2010-Notes About Risk
- Top 10 2010-Release Notes
- Top 10 2010-What's Next For Developers
- Top 10 2010-What's Next For Organizations
- Top 10 2010-What's Next For Verifiers
- Top 10 2013
- Top 10 2013-A1-Injection
- Top 10 2013-A10-Unvalidated Redirects and Forwards
- Top 10 2013-A2-Broken Authentication and Session Management
- Top 10 2013-A3-Cross-Site Scripting (XSS)
- Top 10 2013-A4-Insecure Direct Object References
- Top 10 2013-A5-Security Misconfiguration
- Top 10 2013-A6-Sensitive Data Exposure
- Top 10 2013-A7-Missing Function Level Access Control
- Top 10 2013-A8-Cross-Site Request Forgery (CSRF)
- Top 10 2013-A9-Using Components with Known Vulnerabilities
- Top 10 2013-Details About Risk Factors
- Top 10 2013-Introduction
- Top 10 2013-Note About Risks
- Top 10 2013-Release Notes
- Top 10 2013-Risk
- Top 10 2013-Top 10
- Top 10 2013-What's Next for Developers
- Top 10 2013-What's Next for Organizations
- Top 10 2013-What's Next for Verifiers
- Template:Top 10 2013:BottomAdvancedTemplate
- Template:Top 10 2013:BottomTemplate
- Top 10-2017 A1-Injection
- Top 10-2017 A10-Insufficient Logging&Monitoring
- Top 10-2017 A2-Broken Authentication
- Top 10-2017 A3-Sensitive Data Exposure
- Top 10-2017 A4-XML External Entities (XXE)
- Top 10-2017 A5-Broken Access Control
- Top 10-2017 A6-Security Misconfiguration
- Top 10-2017 A7-Cross-Site Scripting (XSS)
- Top 10-2017 A8-Insecure Deserialization
- Top 10-2017 A9-Using Components with Known Vulnerabilities
- Top 10-2017 Acknowledgements
- Top 10-2017 Application Security Risks
- Top 10-2017 Details About Risk Factors
- Top 10-2017 Foreword
- Top 10-2017 Introduction
- Top 10-2017 Methodology and Data
- Top 10-2017 Note About Risks
- Top 10-2017 Release Notes
- Top 10-2017 Top 10
- Top 10-2017 What's Next for Application Managers
- Top 10-2017 What's Next for Developers
- Top 10-2017 What's Next for Organizations
- Top 10-2017 What's Next for Security Testers
Media in category "OWASP Top Ten Project"
The following 2 files are in this category, out of 2 total.