This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Click Me Project"
Arun Kumar V (talk | contribs) (→Snapshot) |
Arun Kumar V (talk | contribs) (→Snapshot) |
||
| Line 75: | Line 75: | ||
Note : jar file ,so you will need JRE in your system to run the file. | Note : jar file ,so you will need JRE in your system to run the file. | ||
Double click the jar file or give "java -jar clickme.jar" in the command prompt. | Double click the jar file or give "java -jar clickme.jar" in the command prompt. | ||
| − | + | ---- | |
*Python | *Python | ||
[[File:Python.jpg]] | [[File:Python.jpg]] | ||
| Line 81: | Line 81: | ||
$python clickme.py https://www.example.com" | $python clickme.py https://www.example.com" | ||
| − | + | ---- | |
*Html | *Html | ||
[[File:Hmtl.jpg]] | [[File:Hmtl.jpg]] | ||
Note : Load the html in a browser and give the test url in the text area and hit click me button | Note : Load the html in a browser and give the test url in the text area and hit click me button | ||
| + | ---- | ||
= Get Involved = | = Get Involved = | ||
Revision as of 18:40, 28 February 2015
The OWASP Click Me Project: The primary contributors to date have been:
Acknowledgement
References
- OWASP definition on Click jacking or "UI redress attack"
- OWASP test guide for Click jacking attacks.
Just a click away to get your copy of OWASP Click Me.Here we go !
Click Me to Download
Click Me is made available in 3 formats ie as a java gui,python tool and as a stand alone html page.
Snapshot
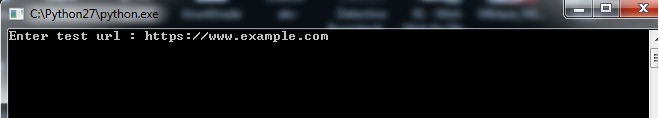
- Java
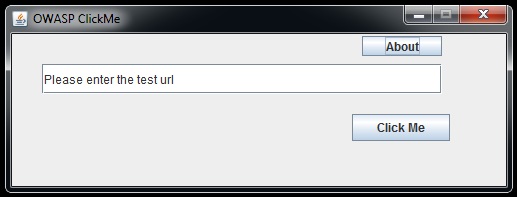 Note : jar file ,so you will need JRE in your system to run the file.
Double click the jar file or give "java -jar clickme.jar" in the command prompt.
Note : jar file ,so you will need JRE in your system to run the file.
Double click the jar file or give "java -jar clickme.jar" in the command prompt.
- Python
Note : Give the test url as shown in the figure, and you will need Python framework supppport to run python file.
$python clickme.py https://www.example.com"
- Html
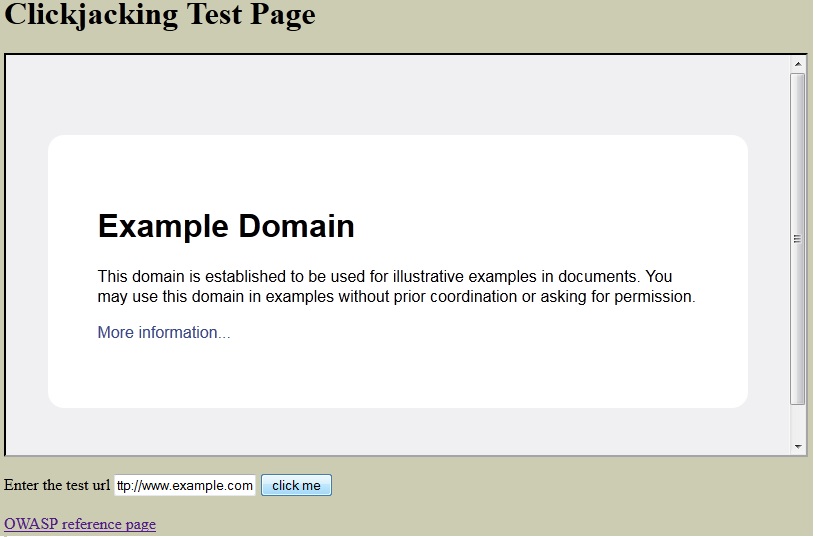 Note : Load the html in a browser and give the test url in the text area and hit click me button
Note : Load the html in a browser and give the test url in the text area and hit click me button
As of now, the priorities are:
- Creating the test html page.
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||