This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP AppSec Asia 2008 - Taiwan"
(→'''NOW AVAILABLE: OWASP AppSec Asia 2008 Session Slides''') |
(→(2008/10/27) - Day 1) |
||
| (52 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | == | + | == NOW AVAILABLE: OWASP AppSec Asia 2008 Session Slides == |
| − | + | The session slides are now available; please go to SESSION column under [https://www.owasp.org/index.php/OWASP_AppSec_Asia_2008_-_Taiwan#OWASP_AppSec_Asia_2008.2C_Conference_Schedule_.28Oct_27th_-_Oct_28th.29 Conference Schedule] to access to the slides. | |
| − | |||
| + | == A Note of Thanks == | ||
| − | + | We would like to thank this year's 1200+ attendees who came to show support for OWASP App Sec Asia 2008!! As well as our Speakers, Chapter leaders and Sponsors who helped make this year's OWASP Asia Conference a great success! | |
| + | [[Image:OWASP_Asia_08.jpg|center|733px]] | ||
| − | |||
| − | == | + | == OWASP AppSec Asia 2008 - Taiwan== |
Welcome to OWASP AppSec Asia 2008! We'd like to thank China, Delhi, Hong Kong, Korea, Mumbai, Singapore, Taiwan, Thailand, and Vietnam Chapters for helping out with the conference and for attending the conference. We are working with other chapters across Asia to see if we can invite more chapters. If you represent an Asia chapter and are interested in participating, please [mailto:[email protected] email us]. | Welcome to OWASP AppSec Asia 2008! We'd like to thank China, Delhi, Hong Kong, Korea, Mumbai, Singapore, Taiwan, Thailand, and Vietnam Chapters for helping out with the conference and for attending the conference. We are working with other chapters across Asia to see if we can invite more chapters. If you represent an Asia chapter and are interested in participating, please [mailto:[email protected] email us]. | ||
| Line 44: | Line 44: | ||
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''<br><br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''<br><br>''' | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''10:00-10:50''' || style="width:30%; background:#A7BFDE" align="center" | ''' [[What's Next? Strategies for Web Application Security]]<br>''' | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''10:00-10:50''' || style="width:30%; background:#A7BFDE" align="center" | ''' [[What's Next? Strategies for Web Application Security]]<br>''' '''[https://www.owasp.org/images/4/41/OWASP_Asia_2008_YMChen.pdf Slides]''' |
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''<BR>[[YM Chen, Director, Foundstone, A Division of McAfee]]<br><BR>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''<BR>[[YM Chen, Director, Foundstone, A Division of McAfee]]<br><BR>''' | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''11:00-11:50''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Web-based Malware obfuscation: the kung-fu and the detection]]''' | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''11:00-11:50''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Web-based Malware obfuscation: the kung-fu and the detection]]''' '''[https://www.owasp.org/images/6/6b/OWASP_Asia_2008_Wayne.pdf Slides]''' |
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''<BR>[[Wayne Huang, OWASP Taiwan Chapter]]<br><BR>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''<BR>[[Wayne Huang, OWASP Taiwan Chapter]]<br><BR>''' | ||
|- | |- | ||
| Line 61: | Line 61: | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''12:40 - 13:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Good Business Penetration Testing]]<BR><br>''' | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''12:40 - 13:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Good Business Penetration Testing]]<BR><br>''' '''[https://www.owasp.org/images/1/14/OWASP_Asia_2008_KK.pdf Slides]''' |
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[KK Mookhey (OWASP Mumbai)]]<br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[KK Mookhey (OWASP Mumbai)]]<br>''' | ||
|- | |- | ||
| Line 89: | Line 89: | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''14:50 - 15:40''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Tiny coding errors, big losses: real stories of website 0wnage]]<BR><br>''' | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''14:50 - 15:40''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Tiny coding errors, big losses: real stories of website 0wnage]]<BR><br>''' '''[https://www.owasp.org/images/6/6a/OWASP_Asia_2008_Fyodor.pdf Slides]''' |
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Fyodor Yarochkin (Guard-Info)]]<br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Fyodor Yarochkin (Guard-Info)]]<br>''' | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''15:50 - 16:40''' || style="width:30%; background:#A7BFDE" align="center" | '''Web Application Proactive and Passive Defense Best Practices | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''15:50 - 16:40''' || style="width:30%; background:#A7BFDE" align="center" | '''Web Application Proactive and Passive Defense Best Practices <BR><br>''' '''[https://www.owasp.org/images/d/d2/OWASP_Asia_2008_FrankFan.pdf Slides]''' |
| − | <BR><br>''' | ||
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Frank Yuan Fan, OWASP China Chapter]]<br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Frank Yuan Fan, OWASP China Chapter]]<br>''' | ||
|- | |- | ||
| align="center" style="width:20%; background:#4F81BD; color:white" | '''16:50 - 17:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Why Webmail systems are hard to secure--using real case studies]]<BR><br>''' | | align="center" style="width:20%; background:#4F81BD; color:white" | '''16:50 - 17:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Why Webmail systems are hard to secure--using real case studies]]<BR><br>''' | ||
| + | '''[https://www.owasp.org/images/d/d3/OWASP_Asia_Taiwan_Charmi.pdf Slides]''' | ||
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Charmi Lin (Taiwan Information & Communication Security Technology Center)]]<br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Charmi Lin (Taiwan Information & Communication Security Technology Center)]]<br>''' | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''17:40 - 18:10''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Penetration Test with BackTrack: Art of Exploitation]]<BR><br>''' | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''17:40 - 18:10''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Penetration Test with BackTrack: Art of Exploitation]]<BR><br>''' '''[https://www.owasp.org/images/f/f7/OWASP_Asia_2008_Anthony.pdf Slides]''' |
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Anthony Lai (Dark Floyd), OWASP HK Chapter]]<br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Anthony Lai (Dark Floyd), OWASP HK Chapter]]<br>''' | ||
|- | |- | ||
| Line 115: | Line 115: | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''09:00- 10:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[New 0-Day Browser Exploits: Clickjacking - yea, this is bad...]]<BR><br>''' | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''09:00- 10:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[New 0-Day Browser Exploits: Clickjacking - yea, this is bad...]]<BR><br>''' '''[https://www.owasp.org/images/9/9f/OWASP_Asia_2008_RSnake.pdf Slides]''' |
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Robert "RSnake" Hansen (SecTheory)]]<br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Robert "RSnake" Hansen (SecTheory)]]<br>''' | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''10:40- 11:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Web 2.0, Consumerization, and Application Security]]<BR><br>''' | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''10:40- 11:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Web 2.0, Consumerization, and Application Security]]<BR><br>''' '''[https://www.owasp.org/images/1/15/OWASP_Asia_2008_Chenxi.pdf Slides]''' |
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Chenxi Wang, Ph.D. (Forrester Research)]]<br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Chenxi Wang, Ph.D. (Forrester Research)]]<br>''' | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''11:40- 12:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Crossing the Chasm: Anatomy of Client-Side and Browser-Based Attacks]]<BR><br>''' | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''11:40- 12:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Crossing the Chasm: Anatomy of Client-Side and Browser-Based Attacks]]<BR><br>''' '''[https://www.owasp.org/images/7/74/OWASP_Asia_2008_Pukhraj.pdf Slides]''' |
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Dhruv Soi (OWASP Delhi Chapter Leader)]], [[Pukhraj Singh (OWASP Delhi Chapter)]]<br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Dhruv Soi (OWASP Delhi Chapter Leader)]], [[Pukhraj Singh (OWASP Delhi Chapter)]]<br>''' | ||
|- | |- | ||
| Line 135: | Line 135: | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''13:30 - 14:20''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Proxy Caches and Web Application Security--using the recent Google Docs 0-day as an example]]<BR><br>''' | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''13:30 - 14:20''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Proxy Caches and Web Application Security--using the recent Google Docs 0-day as an example]]<BR><br>''' '''[https://www.owasp.org/images/e/e5/OWASP_Asia_2008_TimBass.pdf Slides]''' |
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Tim Bass, OWASP Thailand]]<br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Tim Bass, OWASP Thailand]]<br>''' | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''14:30 - 15:20''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Best Practices Guide: Web Application Firewalls]]<BR><br>''' | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''14:30 - 15:20''' || style="width:30%; background:#A7BFDE" align="center" | '''[[Best Practices Guide: Web Application Firewalls]] |
| + | '''[https://www.owasp.org/images/5/5d/AppSecASIA08-BPWAF.pdf Slides]'''<BR><br>''' | ||
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Alexander Meisel (OWASP Germany)]]<br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Alexander Meisel (OWASP Germany)]]<br>''' | ||
|- | |- | ||
| Line 153: | Line 154: | ||
|- | |- | ||
| − | | align="center" style="width:20%; background:#4F81BD; color:white" | '''15:40 - 16:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[The HTTP Botnet Research: Focusing on HTTP based DDoS Botnets]]<BR><br>''' | + | | align="center" style="width:20%; background:#4F81BD; color:white" | '''15:40 - 16:30''' || style="width:30%; background:#A7BFDE" align="center" | '''[[The HTTP Botnet Research: Focusing on HTTP based DDoS Botnets]]<BR><br>''' '''[https://www.owasp.org/images/0/09/OWASP_Asia_2008_Steven.pdf Slides]''' |
| style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Steven Adair (ShadowServer Foundation)]]<br>''' | | style="width:40%; background:#EEF0F7; color:#4A4AFF" align="center" | '''[[Steven Adair (ShadowServer Foundation)]]<br>''' | ||
|- | |- | ||
| Line 220: | Line 221: | ||
== OWASP AppSec Asia 2008 Conference Sponsors == | == OWASP AppSec Asia 2008 Conference Sponsors == | ||
| + | ---- | ||
| + | |||
| + | === ''Guide Team:'' === | ||
| + | |||
| + | |||
| + | [http://www.moeaidb.gov.tw https://www.owasp.org/images/8/82/IDB.png] | ||
| + | [http://www.moea.gov.tw/ https://www.owasp.org/images/a/a4/MOEA.png] | ||
| + | |||
| + | ---- | ||
| + | |||
| + | === ''Organizers:'' === | ||
| + | |||
| + | |||
| + | [http://www.owasp.org/index.php/Taiwan https://www.owasp.org/images/2/2b/OWASP_TW.png] | ||
| + | [http://www.iii.org.tw/english/ https://www.owasp.org/images/7/75/III.png] | ||
| + | [http://web.cisanet.org.tw/# https://www.owasp.org/images/6/64/CISA.png] | ||
| + | |||
| + | ---- | ||
| + | |||
| + | === ''Platinum Sponsors:'' === | ||
| + | |||
| + | [http://www.armorize.com https://www.owasp.org/images/9/98/Armorize.png] - [http://www.fortify.com/ https://www.owasp.org/images/c/c7/Fortify.png] - [http://www.imperva.com/ https://www.owasp.org/images/d/da/IMPERVA.png] - | ||
| + | [http://www.mtechpro.com/ https://www.owasp.org/images/b/be/MTECH.png] - | ||
| + | [http://www.mudynamics.com/ https://www.owasp.org/images/1/17/Mu_Dynamics.png] - | ||
| + | [http://www.systex.com.tw/english/index.asp https://www.owasp.org/images/5/5e/SYSTEX.png] - | ||
| + | [http://www.twisc.ntust.edu.tw/ https://www.owasp.org/images/6/6d/TWISC.png] | ||
| + | |||
| + | ---- | ||
| + | |||
| + | === ''Gold Sponsors:'' === | ||
| + | |||
| + | [http://www.bluecoat.com/ https://www.owasp.org/images/9/9c/BLUECOAT.png] | ||
| + | [http://www.eraysecure.com.tw/ https://www.owasp.org/images/e/ea/ERay.png] | ||
| + | [http://tw.yahoo.com/ https://www.owasp.org/images/a/a9/YahooTw.png] | ||
| + | |||
| + | ---- | ||
| + | |||
| + | === ''Silver Sponsors:'' === | ||
| + | |||
| + | [http://www.network-box.com.tw/ https://www.owasp.org/images/0/08/NETWORK_BOX.png] | ||
| + | |||
| + | ---- | ||
| + | |||
| + | === ''Media Partners'': === | ||
| − | [ | + | [http://www.isecutech.com.tw/main/index.aspx https://www.owasp.org/images/9/97/INFOSECURITY.png] |
Latest revision as of 03:25, 17 November 2008
- 1 NOW AVAILABLE: OWASP AppSec Asia 2008 Session Slides
- 2 A Note of Thanks
- 3 OWASP AppSec Asia 2008 - Taiwan
- 4 OWASP AppSec Asia 2008, Conference Schedule (Oct 27th - Oct 28th)
- 5 Conference Fees & Registration
- 6 Conference T-Shirt
- 7 Conference Venue
- 8 Hotel Information
- 9 Taipei City Map - With OWASP Venue and Hotels Marked
- 10 Welcome to Taiwan
- 11 OWASP AppSec Asia 2008 Conference Sponsors
NOW AVAILABLE: OWASP AppSec Asia 2008 Session Slides
The session slides are now available; please go to SESSION column under Conference Schedule to access to the slides.
A Note of Thanks
We would like to thank this year's 1200+ attendees who came to show support for OWASP App Sec Asia 2008!! As well as our Speakers, Chapter leaders and Sponsors who helped make this year's OWASP Asia Conference a great success!
OWASP AppSec Asia 2008 - Taiwan
Welcome to OWASP AppSec Asia 2008! We'd like to thank China, Delhi, Hong Kong, Korea, Mumbai, Singapore, Taiwan, Thailand, and Vietnam Chapters for helping out with the conference and for attending the conference. We are working with other chapters across Asia to see if we can invite more chapters. If you represent an Asia chapter and are interested in participating, please email us.
Two professional translators will be at the conference to conduct simultaneous oral translation between English and Mandarin. Wireless earphones will be provided.
OWASP AppSec Asia 2008, Conference Schedule (Oct 27th - Oct 28th)
(2008/10/27) - Day 1 | |||
|---|---|---|---|
| 08:30 - 09:30 Door opens for registration | |||
|---|---|---|---|
| TIME | SESSION | SPEAKER | |
| 09:30- 09:40 | Opening welcome and an introduction to this year’s program |
Wayne Huang, Conference Chair | |
| 09:40-09:50 | Welcome by Institute for Information Industry |
| |
| 09:50-10:00 | Welcome by Information Security Consortium, Information Service Industry Association |
| |
| 10:00-10:50 | What's Next? Strategies for Web Application Security Slides |
YM Chen, Director, Foundstone, A Division of McAfee | |
| 11:00-11:50 | Web-based Malware obfuscation: the kung-fu and the detection Slides | Wayne Huang, OWASP Taiwan Chapter | |
| 11:50 - 12:40 Lunch | |||
|---|---|---|---|
| TIME | SESSION | SPEAKER | |
| 12:40 - 13:30 | Good Business Penetration Testing Slides |
KK Mookhey (OWASP Mumbai) | |
| 13:40 - 15:40 Asia Chapter Leader Meeting
Attendee: China, Delhi, HK, Korea, Mumbai, Singapore, Taiwan, Thailand, and Vietnam Chapters P.S: Meeting with go in parallel to the two of the talk sessions and coffee break. | |||
|---|---|---|---|
| 13:40 - 14:30 | How bad can Web vulnerabilities be—case study on a 50 million personal records breach |
PK (Taiwan Criminal Investigation Bureau) | |
| 14:30 - 14:50 Coffee Break | |||
|---|---|---|---|
| TIME | SESSION | SPEAKER | |
| 14:50 - 15:40 | Tiny coding errors, big losses: real stories of website 0wnage Slides |
Fyodor Yarochkin (Guard-Info) | |
| 15:50 - 16:40 | Web Application Proactive and Passive Defense Best Practices Slides |
Frank Yuan Fan, OWASP China Chapter | |
| 16:50 - 17:30 | Why Webmail systems are hard to secure--using real case studies |
Charmi Lin (Taiwan Information & Communication Security Technology Center) | |
| 17:40 - 18:10 | Penetration Test with BackTrack: Art of Exploitation Slides |
Anthony Lai (Dark Floyd), OWASP HK Chapter | |
(2008/10/28) - Day 2 | |||
|---|---|---|---|
| TIME | SESSION | SPEAKER | |
| 09:00- 10:30 | New 0-Day Browser Exploits: Clickjacking - yea, this is bad... Slides |
Robert "RSnake" Hansen (SecTheory) | |
| 10:40- 11:30 | Web 2.0, Consumerization, and Application Security Slides |
Chenxi Wang, Ph.D. (Forrester Research) | |
| 11:40- 12:30 | Crossing the Chasm: Anatomy of Client-Side and Browser-Based Attacks Slides |
Dhruv Soi (OWASP Delhi Chapter Leader), Pukhraj Singh (OWASP Delhi Chapter) | |
| 12:30 - 13:30 Lunch | |||
|---|---|---|---|
| TIME | SESSION | SPEAKER | |
| 13:30 - 14:20 | Proxy Caches and Web Application Security--using the recent Google Docs 0-day as an example Slides |
Tim Bass, OWASP Thailand | |
| 14:30 - 15:20 | Best Practices Guide: Web Application Firewalls | Alexander Meisel (OWASP Germany) | |
| 15:20 - 15:40 Coffee Break | |||
|---|---|---|---|
| TIME | SESSION | SPEAKER | |
| 15:40 - 16:30 | The HTTP Botnet Research: Focusing on HTTP based DDoS Botnets Slides |
Steven Adair (ShadowServer Foundation) | |
| 16:40 - 17:30 | Panel: Manual auditing or automated tools? Blackbox, whitebox, or WAF? |
Alex, Anthony, Chenxi, Dhruv, Frank Fan, Fyodor, KK, Robert, Tim Bass, Wayne, YM | |
Conference Fees & Registration
Conference Fees
The fee for the two days conference is USD 35, which includes:
- Two lunches
- Coffee breaks
- Conference T-Shirt
Registration
Registration is now open!! Please contact us for the registration.
Conference T-Shirt
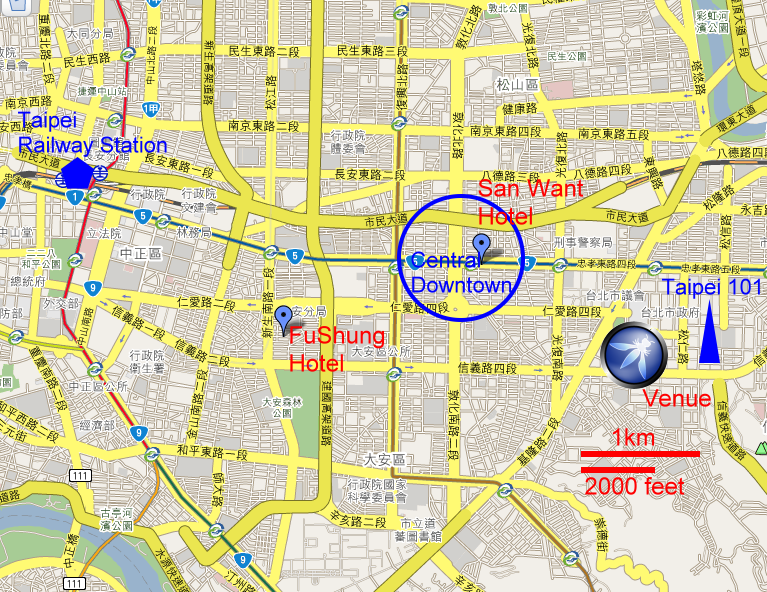
Conference Venue
Taipei International Convention Center
Address: 3rd floor Conference Hall, Xin Yi Road, Section 5, number 1, Taipei, Taiwan R.O.C.
Hotel Information
San Want Hotel
Address: No.172, Sec. 4, ZhongXiao East Road, Taipei, Taiwan
Tel:+886-2-2772-2121 | Fax : +886-2-2721-0302
Hope City FuShing Hotel
Address: No.275, Sec.1, Fushing S. Rd., Taipei, Taiwan
Tel : +886-2-2703-9990 | Fax : +886-2-2706-8547
Taipei City Map - With OWASP Venue and Hotels Marked
Welcome to Taiwan
And WELCOME TO TAIWAN! Please check out this video about interesting places in Taiwan. If you need suggestions on how to plan out your trip, please feel free to contact us!