This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Xenotix XSS Exploit Framework"
Ajin Abraham (talk | contribs) m (Version 5 Download link correction) |
m (Add abandonment note) |
||
| (23 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
=Main= | =Main= | ||
| − | <div style="width:100%;height: | + | <div style="width:100%;height:90px;border:0,margin:0;overflow: hidden;">[[File: lab_big.jpg|link=OWASP_Project_Stages#tab.3DLab_Projects]]</div> |
{| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | {| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | ||
| valign="top" style="border-right: 1px dotted gray;padding-right:20px;" | | | valign="top" style="border-right: 1px dotted gray;padding-right:20px;" | | ||
| − | ==OWASP Xenotix XSS Exploit Framework | + | ==OWASP Xenotix XSS Exploit Framework== |
| + | <span style="color:#ff0000"> | ||
| + | '''NOTE: PROJECT DEVELOPMENT AND SUPPORT IS DISCONTINUED''' | ||
| + | <br> | ||
| + | * https://github.com/ajinabraham/OWASP-Xenotix-XSS-Exploit-Framework#owasp-xenotix-xss-exploit-framework | ||
| + | <br></span> | ||
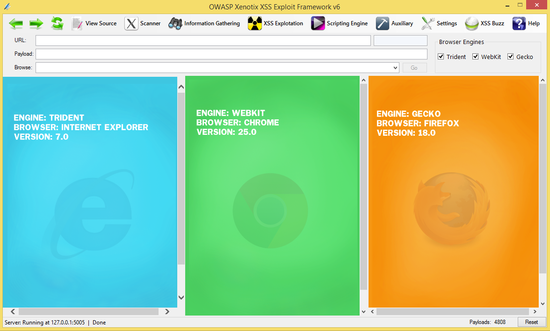
[[Image:Xen6.png|left|550px]] | [[Image:Xen6.png|left|550px]] | ||
| − | '''OWASP Xenotix XSS Exploit Framework''' is an advanced Cross Site Scripting (XSS) vulnerability detection and exploitation framework. Xenotix provides | + | '''OWASP Xenotix XSS Exploit Framework''' is an advanced Cross Site Scripting (XSS) vulnerability detection and exploitation framework. Xenotix provides Low False Positive XSS Detection by performing the Scan within the browser engines where in real world, payloads get reflected. Xenotix Scanner Module is incorporated with 3 intelligent fuzzers to reduce the scan time and produce better results. If you really don't like the tool logic, then leverage the power of Xenotix API to make the tool work like you wanted it to be. |
| − | It is claimed to have the world’s 2nd largest XSS Payloads of about 4800+ distinctive XSS Payloads. It is incorporated with a feature rich Information Gathering module for target Reconnaissance. The Exploit Framework includes real world offensive XSS exploitation modules for Penetration Testing and Proof of Concept creation. | + | It is claimed to have the world’s 2nd largest XSS Payloads of about 4800+ distinctive XSS Payloads. It is incorporated with a feature rich Information Gathering module for target Reconnaissance. The Exploit Framework includes real world offensive XSS exploitation modules for Penetration Testing and Proof of Concept creation. Say no to alert pop-ups in PoC. Pen testers can now create appealing Proof of Concepts within few clicks. |
| Line 30: | Line 35: | ||
'''Nulcon Goa 2013''' | '''Nulcon Goa 2013''' | ||
| − | *Presentation: [http://www.slideshare.net/ajin25/owasp-xenotix-xss-exploit-framework-v3-nullcon-goa-2013 OWASP Xenotix XSS Exploit Framework v3 ] | + | *Presentation: [http://www.slideshare.net/ajin25/owasp-xenotix-xss-exploit-framework-v3-nullcon-goa-2013 OWASP Xenotix XSS Exploit Framework v3 ] |
| + | : [[Media: Xenotixxssexploitframeworkbyajinabraham-130820064955-phpapp02.pdf | Download PDF ]] | ||
| + | |||
'''ClubHack 2012''' | '''ClubHack 2012''' | ||
*Presentation: [http://www.slideshare.net/ajin25/xenotix-xss-exploit-framework-clubhack-2012 OWASP Xenotix XSS Exploit Framework v2] | *Presentation: [http://www.slideshare.net/ajin25/xenotix-xss-exploit-framework-clubhack-2012 OWASP Xenotix XSS Exploit Framework v2] | ||
| Line 38: | Line 45: | ||
Ajin Abraham | [https://twitter.com/ajinabraham @ajinabraham] | Ajin Abraham | [https://twitter.com/ajinabraham @ajinabraham] | ||
| + | == PROJECT WEBSITE == | ||
| + | |||
| + | *http://xenotix.in | ||
== AWARDS == | == AWARDS == | ||
| − | [[Image: | + | [[Image:ToolsWatch2014.png |180px | thumb | left |link=http://www.toolswatch.org/2015/01/2014-top-security-tools-as-voted-by-toolswatch-org-readers/ | Top 5th Security Tool of 2014]] |
| + | [[Image:ToolsWatch2013.png |180px | thumb | left |link=http://www.toolswatch.org/2013/12/2013-top-security-tools-as-voted-by-toolswatch-org-readers/ | Top 5th Security Tool of 2013]] | ||
[[Image:CSPF.jpg |180px | thumb | left | Recommended by CSPF]] | [[Image:CSPF.jpg |180px | thumb | left | Recommended by CSPF]] | ||
| − | | valign="top" style="padding-left:25px;width:175px;" | | + | | valign="top" style="padding-left:25px;width:175px;" | |
== QUICK DOWNLOAD == | == QUICK DOWNLOAD == | ||
| − | [[Image:Dwd.png |200px| link= | + | [[Image:Dwd.png |200px| link=https://github.com/ajinabraham/OWASP-Xenotix-XSS-Exploit-Framework]] |
== NEWS AND EVENTS == | == NEWS AND EVENTS == | ||
| + | * [19 Mar 2014] Xenotix XSS Exploit Framework V6.2 is Released | ||
| + | * [14 Jan 2015] [http://www.toolswatch.org/2015/01/2014-top-security-tools-as-voted-by-toolswatch-org-readers/ Top 5th Security tool of 2014, voted by ToolsWatch Readers] | ||
* [14 Sept 2014] Xenotix XSS Exploit Framework V6 is Released | * [14 Sept 2014] Xenotix XSS Exploit Framework V6 is Released | ||
* [14 Feb 2014] Xenotix XSS Exploit Framework V5 is Released | * [14 Feb 2014] Xenotix XSS Exploit Framework V5 is Released | ||
| Line 65: | Line 78: | ||
* [[OWASP_XSSER]] | * [[OWASP_XSSER]] | ||
| − | |||
| − | |||
| − | |||
| − | |||
== CLASSIFICATIONS == | == CLASSIFICATIONS == | ||
| Line 92: | Line 101: | ||
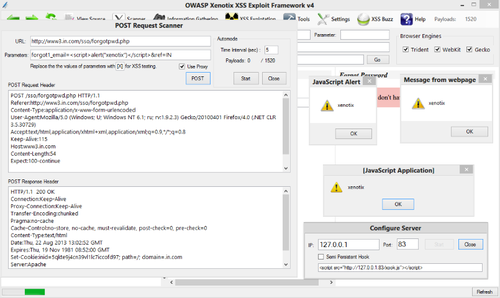
'''SCANNER MODULES''' | '''SCANNER MODULES''' | ||
| − | |||
| − | |||
| − | |||
*GET Request Fuzzer | *GET Request Fuzzer | ||
*POST Request Fuzzer | *POST Request Fuzzer | ||
| Line 100: | Line 106: | ||
*OAuth 1.0a Request Scanner | *OAuth 1.0a Request Scanner | ||
*DOM Scanner | *DOM Scanner | ||
| + | **DOM XSS Analyzer | ||
| + | **Local DOM XSS Analyzer | ||
*Hidden Parameter Detector | *Hidden Parameter Detector | ||
| Line 116: | Line 124: | ||
**Fingerprinting | **Fingerprinting | ||
**Features Detector | **Features Detector | ||
| + | ** HSTS+ CSP Visited Sites Grabber | ||
'''EXPLOITATION MODULES''' | '''EXPLOITATION MODULES''' | ||
| Line 199: | Line 208: | ||
=Downloads= | =Downloads= | ||
| + | == Downloads == | ||
<div style="font-size:120%;border:none;margin: 0;color:#000"> | <div style="font-size:120%;border:none;margin: 0;color:#000"> | ||
| − | + | Get Xenotix Binaries: https://github.com/ajinabraham/OWASP-Xenotix-XSS-Exploit-Framework | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
= Documentation = | = Documentation = | ||
<div style="font-size:120%;border:none;margin: 0;color:#000"> | <div style="font-size:120%;border:none;margin: 0;color:#000"> | ||
| − | + | Check: https://www.youtube.com/playlist?list=PLX3EwmWe0cS80ls3TsNiukQD0hfZjLHnP | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
</div> | </div> | ||
| Line 257: | Line 224: | ||
<div style="font-size:120%;border:none;margin: 0;color:#000"> | <div style="font-size:120%;border:none;margin: 0;color:#000"> | ||
''' WHAT'S NEW! ''' | ''' WHAT'S NEW! ''' | ||
| − | + | ==V6.2 Changes== | |
| + | * Added more Payloads | ||
| + | * New Info Gathering Module HSTS+CSP Visited Sites Detection | ||
| + | * Bug Fix Hash Calculator | ||
| + | * Bug Fix - Get Fuzzer | ||
| + | * Bug Fix IP2Geolocation | ||
| + | ==V6.1 Changes== | ||
| + | * Bug Fixes | ||
| + | * Updated QuickPHP Server | ||
| + | * Local DOM XSS Analyzer | ||
| + | ==V6 Changes== | ||
{{#ev:youtube|RhGVuus_NJw}} | {{#ev:youtube|RhGVuus_NJw}} | ||
| − | |||
| − | |||
* Intelli Fuzzer | * Intelli Fuzzer | ||
* Context Based Fuzzer | * Context Based Fuzzer | ||
| Line 308: | Line 283: | ||
</div> | </div> | ||
| − | = XSS | + | = XSS Cheat Sheet = |
[[Image:Xss_protection.png|center]] | [[Image:Xss_protection.png|center]] | ||
| Line 315: | Line 290: | ||
This document follows a simple language and justifying explanations that helps a developer to implement the correct XSS defense and to build a secure web application that prevents XSS vulnerability and Post XSS attacks. It will also discuss about the existing methods or functions provided by various programming languages to mitigate XSS vulnerability. This document will be updated regularly in order to include updated and correct in information in the domain of XSS Protection. | This document follows a simple language and justifying explanations that helps a developer to implement the correct XSS defense and to build a secure web application that prevents XSS vulnerability and Post XSS attacks. It will also discuss about the existing methods or functions provided by various programming languages to mitigate XSS vulnerability. This document will be updated regularly in order to include updated and correct in information in the domain of XSS Protection. | ||
| − | VIEW: [https://docs.google.com/viewer?srcid=0B_Ci-1YbMqshWUtlaGRyLVBVd28&pid=explorer&efh=false&a=v&chrome=false&embedded=true THE ULTIMATE XSS PROTECTION CHEAT SHEET FOR DEVELOPERS] | + | VIEW: [https://docs.google.com/viewer?srcid=0B_Ci-1YbMqshWUtlaGRyLVBVd28&pid=explorer&efh=false&a=v&chrome=false&embedded=true THE ULTIMATE XSS PROTECTION CHEAT SHEET FOR DEVELOPERS on Google Docs] |
| + | |||
| + | [[Media:Xenotix_XSS_Protection_CheatSheet_For_Developers.pdf| Download PDF from owasp.org]] | ||
| + | |||
| + | = Goodies = | ||
| + | == Xenotix Hoodies == | ||
| + | [[Image:Xenotix_front.jpg]][[Image:Xenotix_back.jpg]] | ||
| + | == Purchase == | ||
| + | Buy Xenotix Hoodies from Paypal [http://opensecurity.in/xenotix-hoodies/ BUY NOW] | ||
= Get Involved = | = Get Involved = | ||
| Line 327: | Line 310: | ||
==Support Us== | ==Support Us== | ||
| + | *Twitter Page: [https://twitter.com/Xenotix Xenotix on Twitter] | ||
*Facebook Page: [https://www.facebook.com/xenotix Xenotix on Facebook] | *Facebook Page: [https://www.facebook.com/xenotix Xenotix on Facebook] | ||
*Official Page: [[http://www.opensecurity.in/owasp-xenotix-xss-exploit-framework-v4-2013 Xenotix @ OpenSecurity]] | *Official Page: [[http://www.opensecurity.in/owasp-xenotix-xss-exploit-framework-v4-2013 Xenotix @ OpenSecurity]] | ||
Latest revision as of 12:25, 1 April 2019
- Main
- Features
- Conference Talks
- Screenshots
- Downloads
- Documentation
- Roadmap
- XSS Cheat Sheet
- Goodies
- Get Involved
OWASP Xenotix XSS Exploit Framework
NOTE: PROJECT DEVELOPMENT AND SUPPORT IS DISCONTINUED
OWASP Xenotix XSS Exploit Framework is an advanced Cross Site Scripting (XSS) vulnerability detection and exploitation framework. Xenotix provides Low False Positive XSS Detection by performing the Scan within the browser engines where in real world, payloads get reflected. Xenotix Scanner Module is incorporated with 3 intelligent fuzzers to reduce the scan time and produce better results. If you really don't like the tool logic, then leverage the power of Xenotix API to make the tool work like you wanted it to be. It is claimed to have the world’s 2nd largest XSS Payloads of about 4800+ distinctive XSS Payloads. It is incorporated with a feature rich Information Gathering module for target Reconnaissance. The Exploit Framework includes real world offensive XSS exploitation modules for Penetration Testing and Proof of Concept creation. Say no to alert pop-ups in PoC. Pen testers can now create appealing Proof of Concepts within few clicks.
LICENSINGOWASP Xenotix XSS Exploit Framework is free to use. It is licensed under the http://creativecommons.org/licenses/by-sa/3.0/ Creative Commons Attribution-ShareAlike 3.0 license], so you can copy, distribute and transmit the work, and you can adapt it, and use it commercially, but all provided that you attribute the work and if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one.
|
PRESENTATIONSDEFCON DCG Banglore 2013
BlackHat Europe Arsenal 2013
Nulcon Goa 2013
ClubHack 2012
PROJECT LEADERAjin Abraham | @ajinabraham PROJECT WEBSITEAWARDS
|
QUICK DOWNLOADNEWS AND EVENTS
RELATED PROJECTS
CLASSIFICATIONS
| |||||||
SCANNER MODULES
- GET Request Fuzzer
- POST Request Fuzzer
- Advanced Request Fuzzer
- OAuth 1.0a Request Scanner
- DOM Scanner
- DOM XSS Analyzer
- Local DOM XSS Analyzer
- Hidden Parameter Detector
INFORMATION GATHERING MODULES
- WAF Fingerprinting
- Victim Fingerprinting
- IP to Location
- IP to GeoLocation
- Network
- Network IP (WebRTC)
- Ping Scan
- Port Scan
- Internal Network Scan
- Browser
- Fingerprinting
- Features Detector
- HSTS+ CSP Visited Sites Grabber
EXPLOITATION MODULES
- Send Message
- Cookie Thief
- Keylogger
- HTML5 DDoSer
- Load File
- Grab Page Screenshot
- JavaScript Shell
- Reverse HTTP WebShell
- Metasploit Browser Exploit
- Social Engineering
- Phisher
- Tabnabbing
- Live WebCam Screenshot
- Download Spoofer
- Geolocation HTML5 API
- Java Applet Drive-By (Windows)
- Java Applet Drive-By Reverse Shell (Windows)
- HTA Network Configuration (Windows, IE)
- HTA Drive-By (Windows, IE)
- HTA Drive-By Reverse Shell (Windows, IE)
- Firefox Addons
- Reverse TCP Shell Addon (Windows, Persistent)
- Reverse TCP Shell Addon (Linux, Persistent)
- Session Stealer Addon (Persistent)
- Keylogger Addon (Persistent)
- DDoSer Addon (Persistent)
- Linux Credential File Stealer Addon (Persistent)
- Drop and Execute Addon (Persistent)
AUXILIARY MODULES
- WebKit Developer Tools
- Encoder/Decoder
- JavaScript Encoders
- JSFuck 6 Char Encoder
- jjencode Encoder
- aaencode Encoder
- JavaScript Beautifier
- Hash Calculator
- Hash Detector
- View Injected JavaScript
- View XSS Payloads
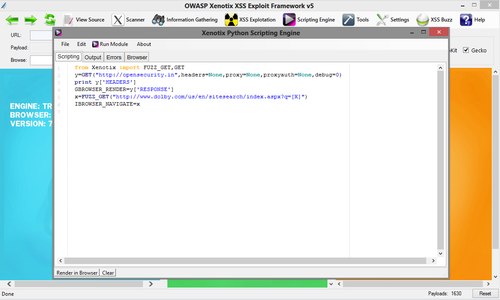
XENOTIX SCRIPTING ENGINE
- Xenotix API
- IronPython Scripting Support
- Trident and Gecko Web Engine Support
NULLCON GOA 2013
CLUBHACK 2012
Downloads
Get Xenotix Binaries: https://github.com/ajinabraham/OWASP-Xenotix-XSS-Exploit-Framework
WHAT'S NEW!
V6.2 Changes
- Added more Payloads
- New Info Gathering Module HSTS+CSP Visited Sites Detection
- Bug Fix Hash Calculator
- Bug Fix - Get Fuzzer
- Bug Fix IP2Geolocation
V6.1 Changes
- Bug Fixes
- Updated QuickPHP Server
- Local DOM XSS Analyzer
V6 Changes
- Intelli Fuzzer
- Context Based Fuzzer
- Blind Fuzzer
- HTA Network Configuration
- HTA Drive-By
- HTA Drive-By Reverse Shell
- JSFuck 6 Char Encoder
- jjencode Encoder
- aaencode Encoder
- IP to Location
- IP to GeoLocation
- IP Hinting
- Download Spoofer
- HTML5 Geolocation API
- Reverse TCP Shell Addon (Linux)
- OAuth 1.0a Request Scanner
- 4800+ Payloads
- SSL Error Fixed
V5 Changes
- Xenotix Scripting Engine
- Xenotix API
- V4.5 Bug Fixes
- GET Network IP (Information Gathering)
- QR Code Generator for Xenotix xook
- HTML5 WebCam Screenshot(Exploitation Module)
- HTML5 Get Page Screenshot (Exploitation Module)
- Find Feature in View Source.
- Improved Payload Count to 1630
- Name Changes
V4.5 Changes
- JavaScript Beautifier
- Pause and Resume support for Scan
- Jump to Payload
- Cookie Support for POST Request
- Cookie Support and Custom Headers for Header Scanner
- Added TRACE method Support
- Improved Interface
- Better Proxy Support
- WAF Fingerprinting
- Load Files <exploitation module>
- Hash Calculator
- Hash Detector
The Ultimate XSS Protection Cheat Sheet for Developers is a compilation of information available on XSS Protection from various organization, researchers, websites, and from our own experience. This document follows a simple language and justifying explanations that helps a developer to implement the correct XSS defense and to build a secure web application that prevents XSS vulnerability and Post XSS attacks. It will also discuss about the existing methods or functions provided by various programming languages to mitigate XSS vulnerability. This document will be updated regularly in order to include updated and correct in information in the domain of XSS Protection.
VIEW: THE ULTIMATE XSS PROTECTION CHEAT SHEET FOR DEVELOPERS on Google Docs
Involvement in the development of Xenotix is highly encouraged!
Here are some of the ways you can help:
Support Us
- Twitter Page: Xenotix on Twitter
- Facebook Page: Xenotix on Facebook
- Official Page: [Xenotix @ OpenSecurity]
Feedback & Queries
- Do you have any issues with it?
- Do you find any design flows or errors?
- Do you need help in using it?
- Do you have something to tell about it?
Then please use this form: https://docs.google.com/forms/d/1RpUhQvuHGvPTl7Gi-EXzecidGvJwKpsRaY9-MeXm1ro/viewform
Development
Are you a developer? Do you have some cool ideas to contribute? Get in touch via ajin [DOT] abraham [AT] owasp.org If you actively contribute to Xenotix then you will be invited to join the project.