This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Security Research and Development Framework"
| (11 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | {{taggedDocument | |
| + | | type=pls_review | ||
| + | | comment=This project seems outdated | ||
| + | }} | ||
| + | =Main= | ||
| − | + | <!-- DO NOT ALTER OR REMOVE THE TEXT ON NEXT LINE --> | |
| + | <div style="width:100%;height:100px;border:0,margin:0;overflow: hidden;">[[Image:OWASP Inactive Banner.jpg|800px| link=https://www.owasp.org/index.php/OWASP_Project_Stages#tab=Inactive_Projects]] </div> | ||
| − | + | {| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | |
| + | | valign="top" style="border-right: 1px dotted gray;padding-right:25px;" | | ||
| − | + | == Abstract: == | |
| − | |||
| − | |||
| − | |||
| − | = Abstract: = | ||
This is a free open source Development Framework created to support writing security tools and malware analysis tools. And to convert the security researches and ideas from the theoretical approach to the practical implementation. | This is a free open source Development Framework created to support writing security tools and malware analysis tools. And to convert the security researches and ideas from the theoretical approach to the practical implementation. | ||
| Line 16: | Line 18: | ||
| − | = Introduction: = | + | == Introduction: == |
| − | |||
In the last several years, the malware black market grows widely. The statistics shows that the number of new viruses increased from 300,000 viruses to millions and millions nowadays. | In the last several years, the malware black market grows widely. The statistics shows that the number of new viruses increased from 300,000 viruses to millions and millions nowadays. | ||
| Line 31: | Line 32: | ||
The SRDF is divided into 2 parts: User-Mode and Kernel-Mode. And we will describe each one in the next section. | The SRDF is divided into 2 parts: User-Mode and Kernel-Mode. And we will describe each one in the next section. | ||
| + | '''SRDF is seeking contributors to help with the next releases . Contact [mailto:[email protected] Amr Thabet] for more info. | ||
| + | |||
| + | '''We can help you create your own project based on SRDF .. just contact us from the email above | ||
| − | = | + | ==Licensing== |
| + | SRDF is a free open source framework. It is licensed under the GPL v2 | ||
| + | | valign="top" style="padding-left:25px;width:200px;border-right: 1px dotted gray;padding-right:25px;" | | ||
| − | + | ==The Features:== | |
| − | |||
| − | + | Before talking about SRDF Design and structure, I want to give you what you will gain from SRDF and what it could add to your project. | |
| + | ===in Malware:=== | ||
• Assembler and Disassembler | • Assembler and Disassembler | ||
| Line 46: | Line 52: | ||
• x86 Emulator | • x86 Emulator | ||
| − | • Debugger | + | • x86 Debugger |
| − | • PE Analyzer | + | • PE Analyzer, ELF Analyzer, PDF Analyzer (still in progress), Android APK Analyzer |
• Process Analyzer (Loaded DLLs, Memory Maps … etc) | • Process Analyzer (Loaded DLLs, Memory Maps … etc) | ||
| Line 54: | Line 60: | ||
• MD5, SSDeep and Wildlist Scanner (YARA) | • MD5, SSDeep and Wildlist Scanner (YARA) | ||
| − | • API Hooker and Process Injection | + | • API Hooker, IAT Hooking and Process Injection |
• Backend Database, XML Serializer | • Backend Database, XML Serializer | ||
| Line 60: | Line 66: | ||
• And many more | • And many more | ||
| − | + | ===in Network:=== | |
| + | |||
| + | • Packet capturing using winpcap | ||
| + | |||
| + | • Pcap file analysis and packet analyzer | ||
| + | |||
| + | • detecting malformed packets and packet generator | ||
| + | |||
| + | • Session analysis and session separation | ||
| + | |||
| + | • Protocol Analysis like tcp, udp, icmp .. etc | ||
| + | |||
| + | • Application layer protocol analysis like http and dns | ||
| + | |||
| + | • And many more | ||
| + | |||
| + | |||
| + | and the project is totally object oriented, very expandable and well organized | ||
| + | |||
| + | ''' the project development still active and still expanding | ||
| + | |||
| + | == Python SRDF (pySRDF)== | ||
| + | |||
| + | it's an implementation for SRDF on python and very easy to use like this: | ||
| + | |||
| + | >>from pySRDF import * | ||
| + | >>dbg = Dbg("C:\\test.exe") | ||
| + | >>dbg.SetBp(0x401000) | ||
| + | >>dbg.Run() | ||
| − | + | OR Using the Emulator: | |
| + | >> emu = Emulator("C:\\test.exe") | ||
| + | >> emu.SetBp("eip == 0x401000") | ||
| + | >> emu.Run() | ||
| − | + | OR | |
| − | + | >> emu.SetBp("__isdirty(eip)") #which set bp on Execute on modified data | |
| + | >> emu.Run() | ||
| − | + | Find it at: | |
| − | + | [https://github.com/AmrThabet/pySRDF pySRDF Github] | |
| − | + | [https://github.com/AmrThabet/pySRDF/tree/master/Examples Examples] | |
| − | + | | valign="top" style="padding-left:25px;width:200px;" | | |
| − | + | == Source Code: == | |
| − | + | [https://github.com/AmrThabet/winSRDF Github] | |
| + | [https://www.openhub.net/p/winSRDF Openhub] | ||
| − | + | [http://www.security-framework.com Our Website] | |
| − | |||
| + | == Project Leader == | ||
| + | [mailto:[email protected] Amr Thabet] | ||
| + | |} | ||
| − | = | + | =Design= |
| − | |||
== The Design: == | == The Design: == | ||
| − | + | ||
| + | the main design is: | ||
| + | |||
| + | [[File:SRDF-Design.png]] | ||
| + | |||
=== Infrastructure: === | === Infrastructure: === | ||
| Line 125: | Line 169: | ||
1. String: it contains the string class, encoded string, hash and list | 1. String: it contains the string class, encoded string, hash and list | ||
| + | |||
2. Code: it contains the NativeCode class and StoredProcedure … and they represents the shellcode and the code that stored in database. Like a virus detection routines inside an Antivirus | 2. Code: it contains the NativeCode class and StoredProcedure … and they represents the shellcode and the code that stored in database. Like a virus detection routines inside an Antivirus | ||
| + | |||
3. XML: and it contains the XML Encoder and the Serializer. | 3. XML: and it contains the XML Encoder and the Serializer. | ||
| Line 133: | Line 179: | ||
1. Internet: and it contains the internet communication protocols like sockets, HTTP Sockets and so on. | 1. Internet: and it contains the internet communication protocols like sockets, HTTP Sockets and so on. | ||
| + | |||
2. IPC: and it contains the Inter-Process Communication protocol | 2. IPC: and it contains the Inter-Process Communication protocol | ||
| + | |||
3. User-Mode to Kernel-Mode Communication: and it contains the communication protocol to communicate to the kernel-mode part of the SRDF | 3. User-Mode to Kernel-Mode Communication: and it contains the communication protocol to communicate to the kernel-mode part of the SRDF | ||
| Line 141: | Line 189: | ||
1. Databases: and it contains the Database class and SQLiteDB and so on. | 1. Databases: and it contains the Database class and SQLiteDB and so on. | ||
| + | |||
2. Files: and contains the File writing and logging classes | 2. Files: and contains the File writing and logging classes | ||
| + | |||
3. Registry: and it contains the registry read and write | 3. Registry: and it contains the registry read and write | ||
| Line 179: | Line 229: | ||
And the core includes the cApp class that contains the back-end database and logging and the User-Interface such as cConsoleApp | And the core includes the cApp class that contains the back-end database and logging and the User-Interface such as cConsoleApp | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
=Project About= | =Project About= | ||
{{:Projects/OWASP_Security_Research_and_Development_Framework}} | {{:Projects/OWASP_Security_Research_and_Development_Framework}} | ||
| − | + | __NOTOC__ <headertabs /> | |
[[Category:OWASP Project]] | [[Category:OWASP Project]] | ||
Latest revision as of 15:29, 12 February 2016
Comment: This project seems outdated
Abstract:This is a free open source Development Framework created to support writing security tools and malware analysis tools. And to convert the security researches and ideas from the theoretical approach to the practical implementation. This development framework created mainly to support the malware field to create malware analysis tools and anti-virus tools easily without reinventing the wheel and inspire the innovative minds to write their researches on this field and implement them using SRDF.
Introduction:In the last several years, the malware black market grows widely. The statistics shows that the number of new viruses increased from 300,000 viruses to millions and millions nowadays. The complexity of malware attacks also increased from small amateur viruses to stuxnet, duqu and flame. The malware field is searching for new technologies and researches, searching for united community can withstand against these attacks. And that’s why SRDF The SRDF is not and will not be developed by one person or a team. It will be developed by a big community tries to share their knowledge and tools inside this Framework SRDF still not finished … and it will not be finished as it’s a community based framework developed by the contributors. We just begin the idea. The SRDF is divided into 2 parts: User-Mode and Kernel-Mode. And we will describe each one in the next section. SRDF is seeking contributors to help with the next releases . Contact Amr Thabet for more info. We can help you create your own project based on SRDF .. just contact us from the email above LicensingSRDF is a free open source framework. It is licensed under the GPL v2 |
The Features:Before talking about SRDF Design and structure, I want to give you what you will gain from SRDF and what it could add to your project. in Malware:• Assembler and Disassembler • x86 Emulator • x86 Debugger • PE Analyzer, ELF Analyzer, PDF Analyzer (still in progress), Android APK Analyzer • Process Analyzer (Loaded DLLs, Memory Maps … etc) • MD5, SSDeep and Wildlist Scanner (YARA) • API Hooker, IAT Hooking and Process Injection • Backend Database, XML Serializer • And many more in Network:• Packet capturing using winpcap • Pcap file analysis and packet analyzer • detecting malformed packets and packet generator • Session analysis and session separation • Protocol Analysis like tcp, udp, icmp .. etc • Application layer protocol analysis like http and dns • And many more
the project development still active and still expanding Python SRDF (pySRDF)it's an implementation for SRDF on python and very easy to use like this: >>from pySRDF import *
>>dbg = Dbg("C:\\test.exe")
>>dbg.SetBp(0x401000)
>>dbg.Run()
OR Using the Emulator: >> emu = Emulator("C:\\test.exe")
>> emu.SetBp("eip == 0x401000")
>> emu.Run()
OR >> emu.SetBp("__isdirty(eip)") #which set bp on Execute on modified data
>> emu.Run()
Find it at: |
Source Code:
Project Leader |
The Design:
the main design is:
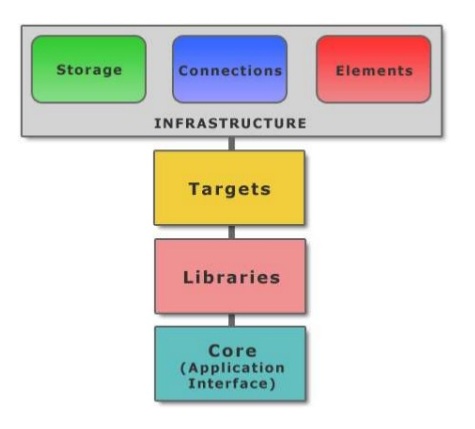
Infrastructure:
This includes the essential elements of any development framework and it’s not related to security like: string, hash, list, serializer, database, registry manipulation, sockets and so on.
We decided to create this part rather than depending on any development framework to make this framework independent from any other development frameworks and to be portable on any development framework
Targets:
This is the beginning of the SRDF. This part is simply the Target from your security tool. What do you want to secure or secure from. And it includes Files (PE Files and others), Processes and Packets.
Libraries:
That’s the security tools that the SRDF support. And it’s divided into two namespaces: malware and network
Malware includes the assemblers and disassemblers, emulator, debugger, API Hooker, Yara Scanner (wildcard scanner) file recursive scanner and other tools
Network includes User-Mode capturing and Firewall
Core (The Application Interface):
The Core includes the Logging system and the back-end Database.
And also, it’s the Application Interface. Like cConsoleApp … and you can inherit from it to create your own User-Interface.
We wish this part to be expanded to include more user interfaces and management systems
The Infrastructure:
Elements:
It’s divided into three namespaces:
1. String: it contains the string class, encoded string, hash and list
2. Code: it contains the NativeCode class and StoredProcedure … and they represents the shellcode and the code that stored in database. Like a virus detection routines inside an Antivirus
3. XML: and it contains the XML Encoder and the Serializer.
Connections:
It’s divided into three namespaces:
1. Internet: and it contains the internet communication protocols like sockets, HTTP Sockets and so on.
2. IPC: and it contains the Inter-Process Communication protocol
3. User-Mode to Kernel-Mode Communication: and it contains the communication protocol to communicate to the kernel-mode part of the SRDF
Storage:
It’s divided into three namespaces:
1. Databases: and it contains the Database class and SQLiteDB and so on.
2. Files: and contains the File writing and logging classes
3. Registry: and it contains the registry read and write
The Targets:
Files:
This namespace describes the File Formats of The Files that could contain malicious code like: Executable Files (PE and ELF) and Document Files (PDF, Docx …) and so on.
Until now it contains The PE Files parser
Process:
And it includes one class only named cProcess. And, this class describes a running process and parses its PEB and gives you the important information about the process and its memory map. And support injecting code and create a remote thread.
Packets:
And it includes classes that describe an internet packets captured on the wire or generated for an attack.
Libraries:
It contains two namespaces:
Malware:
This namespace contains the scanning, Hooking and emulation libraries and contains Pokas Emulator wrapper class, Yara wrapper class (wildcard scanner), a debugger and contains a directory recursive scanner and other tools
And also, it contains the x86 assembler and disassembler (using Pokas Emulator Assembler) and allow to contain other assemblers and for other platforms.
Network:
This namespace should contain the User-Mode Packet capture and firewall. And should contain the Winpcap Packet capturing and firewall system. It also should include Application Layer parsers for FTP, HTTP, IRC and all known protocols and include Pcap Reader and writer.
The Core:
And the core includes the cApp class that contains the back-end database and logging and the User-Interface such as cConsoleApp
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||||