This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Windows Binary Executable Files Security Checks Project"
From OWASP
Dan Vasile (talk | contribs) |
|||
| (6 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
| − | [[ | + | {| |
| + | |- | ||
| + | ! width="700" align="center" | <br> | ||
| + | ! width="500" align="center" | <br> | ||
| + | |- | ||
| + | | align="right" | [[Image:OWASP Inactive Banner.jpg|800px| link=https://www.owasp.org/index.php/OWASP_Project_Stages#tab=Inactive_Projects]] | ||
| + | | align="right" | | ||
| − | + | |} | |
This checklist represent a series of tests and the associated tools to perform the tasks related to thick client testing. | This checklist represent a series of tests and the associated tools to perform the tasks related to thick client testing. | ||
| Line 9: | Line 15: | ||
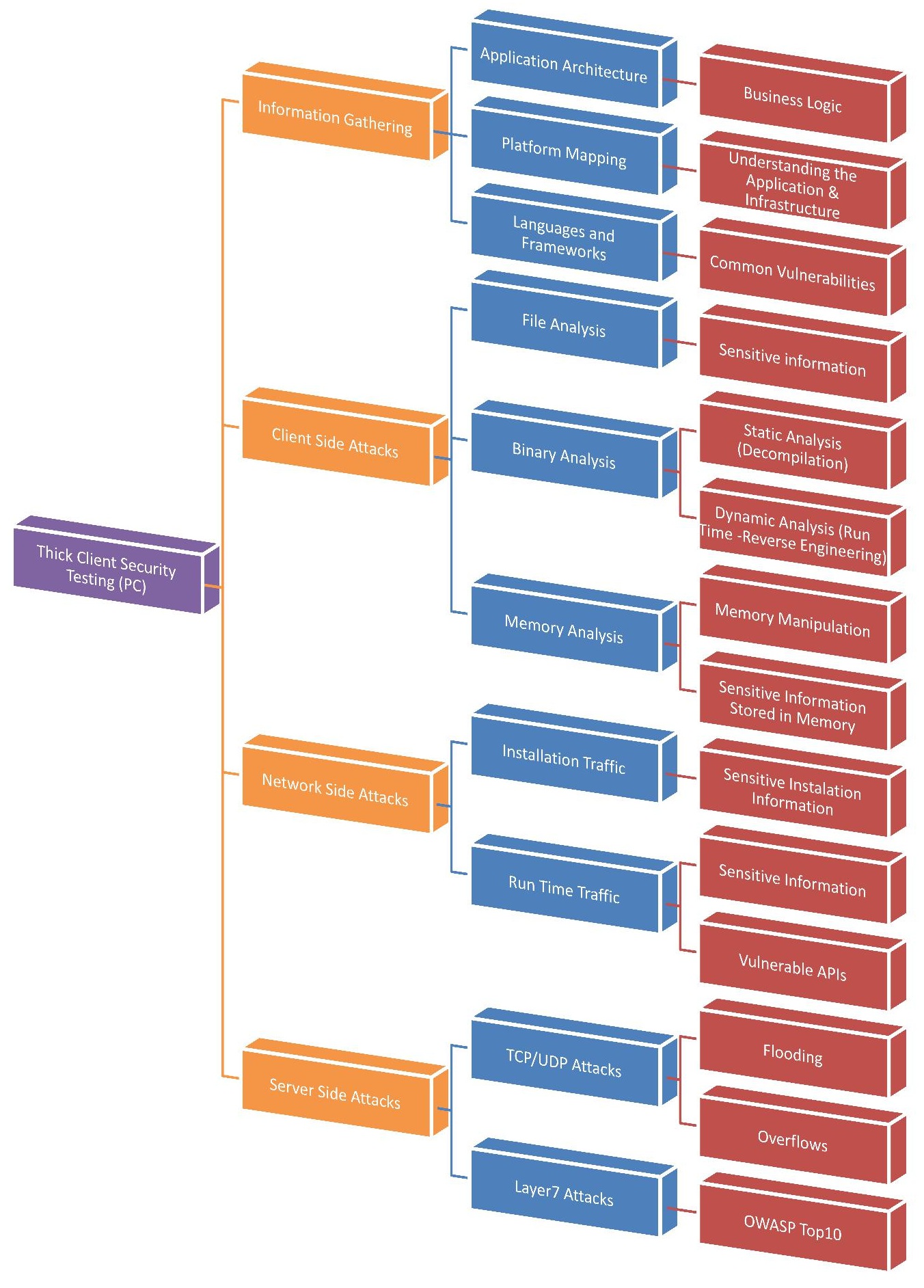
[[File:Thick client testing.jpg]] | [[File:Thick client testing.jpg]] | ||
| + | |||
| + | ==Thick Client Security Testing== | ||
| + | |||
| + | ===Information Gathering=== | ||
| + | |||
| + | ====Application Architecture==== | ||
| + | |||
| + | ====Platform Mapping==== | ||
| + | |||
| + | ====Languages and Frameworks==== | ||
| + | |||
| + | ===Client Side attacks=== | ||
| + | |||
| + | ====Files Analysis==== | ||
| + | |||
| + | ====Binary Analysis==== | ||
| + | |||
| + | ====Memory Analysis==== | ||
| + | |||
| + | ===Network Side Attacks=== | ||
| + | |||
| + | ====Installation Traffic==== | ||
| + | |||
| + | ====Run Time Traffic==== | ||
| + | |||
| + | ===Server Side Attacks=== | ||
| + | |||
| + | ====Network Layer Attacks==== | ||
| + | |||
| + | ====Layer 7 Attacks==== | ||
= Project About = | = Project About = | ||
Latest revision as of 21:33, 9 May 2014
| |
|
|---|---|

|
This checklist represent a series of tests and the associated tools to perform the tasks related to thick client testing.
We define the thick client as a computer (client) in client–server architecture or networks that typically provides rich functionality independent of the central server. The focus of this checklist will be around PC/Windows architecture, although general concepts apply to all thick clients.
The Map
Thick Client Security Testing
Information Gathering
Application Architecture
Platform Mapping
Languages and Frameworks
Client Side attacks
Files Analysis
Binary Analysis
Memory Analysis
Network Side Attacks
Installation Traffic
Run Time Traffic
Server Side Attacks
Network Layer Attacks
Layer 7 Attacks
Project About
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||