This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
SAMM - Roadmap - Government Organization

|
For the latest project news and information, join the mailing list and visit the OpenSAMM website. |
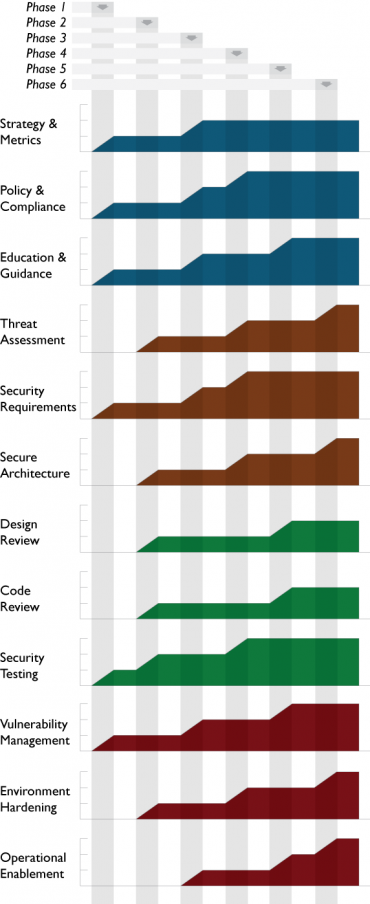
Government Organization
Rationale
A Government Organization involves the core business function of being a state-affiliated organization that builds software to support public sector projects.
Initially, Governance Practices are established, generally to get an idea of the overall compliance burden for the organization in context of the concrete roadmap for improvement.
Because of risks of public exposure and the quantity of legacy code generally in place, early emphasis is given to Security Testing within the Verification Practices and later the more involved Code Review or Design Review Practices are developed.
Similar emphasis is placed on the Construction and Deployment Practices. This helps establish the organization’s management of vulnerabilities and moves toward bolstering the security posture of the operating environment. At the same time, proactive security activities under Construction are built up to help prevent new issues in software under development.
Additional Considerations
Outsourced Development
For organizations using external development resources, restrictions on code access typically leads to prioritization of Security Requirements activities instead of Code Review activities. Additionally, advancing Threat Assessment in earlier phases would allow the organization to better clarify security needs to the outsourced developers. Since expertise on software configuration will generally be strongest within the outsourced group, contracts should be constructed to account for the activities related to Operational Enablement.
Web Services Platforms
For organizations building web services platforms, design errors can carry additional risks and be more costly to mitigate. Therefore, activities from Threat Assessment, Security Requirements, and Secure Architecture should be placed in earlier phases of the roadmap.
Regulatory Compliance
For organizations under heavy regulations that affect business processes, the build-out of the Policy & Compliance Practice should be adjusted to accommodate external drivers. Likewise, organizations under a lighter compliance load should take the opportunity to push back build-out of that Practice in favor of others.
Additional Resources