This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
OAT-002 Token Cracking
This is an automated threat. To view all automated threats, please see the Automated Threat Category page. The OWASP Automated Threat Handbook - Wed Applications (pdf, print), an output of the OWASP Automated Threats to Web Applications Project, provides a fuller guide to each threat, detection methods and countermeasures. The threat identification chart helps to correctly identify the automated threat.
Definition
OWASP Automated Threat (OAT) Identity Number
OAT-002
Threat Event Name
Token Cracking
Summary Defining Characteristics
Mass enumeration of coupon numbers, voucher codes, discount tokens, etc.
Indicative Diagram
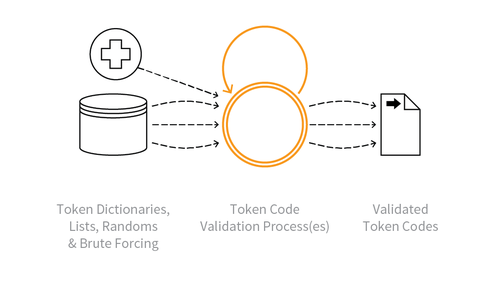
Description
Identification of valid token codes providing some form of user benefit within the application. The benefit may be a cash alternative, a non-cash credit, a discount, or an opportunity such as access to a limited offer.
For cracking of usernames, see OAT-007 Credential Cracking instead.
Other Names and Examples
Coupon guessing; Voucher, gift card and discount enumeration
See Also
Cross-References
CAPEC Category / Attack Pattern IDs
- 112 Brute Force
- 210 Abuse of Functionality
CWE Base / Class / Variant IDs
- 799 Improper Control of Interaction Frequency
- 837 Improper Enforcement of a Single, Unique Action
WASC Threat IDs
- 11 Brute Force
- 21 Insfficient Anti-Automation
- 42 Abuse of Functionality