This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
CISO Survey 2013: Investments and challenges
2. Investments and challenges
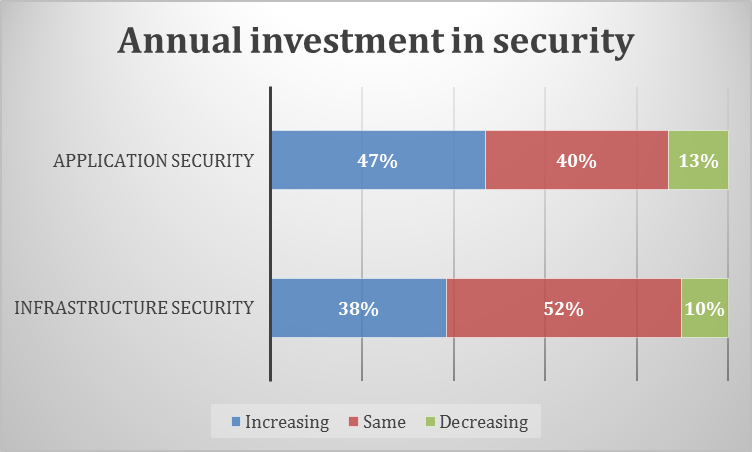
Increase of investments in Application Security
With regards to these risks and in general, application security investments are overall increasing for the next year, while the majority of budgets for infrastructure security will remain roughly the same.
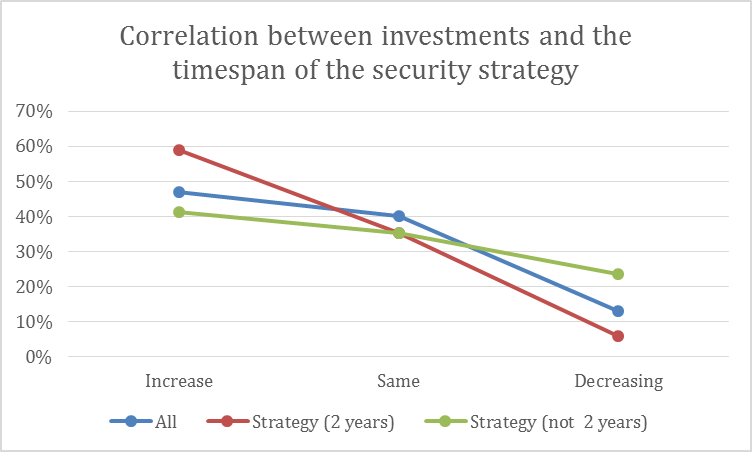
Advantages of a two year application security strategy for budget allocations
We also further analyzed the data for correlations of investments with a variety of factors, like whether an organization had a recent security breach, has an ASMS, company size, type of role of the submitting person (i.e. CISO), whether the organization has a security strategy, and the time horizon of the security strategy. So far we only found a significant correlation with the existence of 2-year security strategies. Other factors did not show a significant correlation, which can to some degree be due to the fact that the data set might not be large enough to prove other relationships.
Although of course correlation is not a proof for causality, it appears that there is a sweet spot of a 2-year security strategy that can help in budget decisions increasing investments in security. Other timespans did not show a significant improvement. Reasons behind this might be that a 2-year security strategy gives enough planning time to allocate security investments budgets into the following year, even if the budget for the current year is already exhausted. It may also give an advantage in the budget planning process to look beyond the annual budget plans. (More details about security strategies in the last section “Governance and Controls” and in part III of the OWASP CISO guide.)
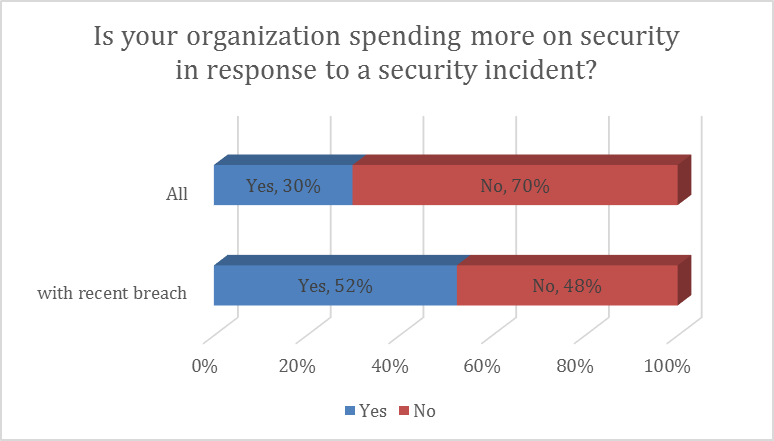
We also wanted to analyze the influence of a previous data breach on new security investments. So far there have been frequent anecdotal reports that a recent breach can increase the motivation and chances of an organization to invest more in security. So we asked the CISOs about whether their organization would be spending more on application security in response to a breach or security incident related to a web application?
Nearly seventy percent stated that a recent breach would not influence their future spending in security. Interestingly this picture changes when you look at only the sub-group of companies who recently had an incident. There, more than half stated that they would increase spending on application security after an incident. Maybe going through the experience recently made them more aware for the potential turmoil and damages resulting from such breaches with the consequence of increased spending to not “get burned again”. And vice versa, this could be an indication that companies who didn’t recently suffer from a breach or an incident (or are not aware of it) might in fact be underinvesting in application security as they are underestimating the potential damages from such a security incident. It might also be an indication for a lack of proactive risk management strategy of some organizations when budgeting for the security of applications. As when the focus is on tactical risk management, a security incident may still trigger an increase in spending in application security even if is not considered a factor in the budgeting for a one or two year strategy.
The Top five application security priorities for the coming 12 months
After looking at the trends of application security investment, we analyzed deeper which specific areas CISOs identified as their Top-5 priorities for 2014. And we received as a clear Top priority the improvement of security awareness and training for developers, which corresponds well to counter the most important security risk as seen by CISOs, the lack of awareness of application security issues within the organization. In line with these CISO priorities, OWASP will focus especially on this and has defined the improvement of security trainings as one of our key strategic goals for 2014.
|
Biggest challenges to effectively delivering your organization's application security initiatives
Interestingly the top challenge for CISOs is not acquiring adequate budget, but finding the right qualified resources and achieving awareness across the organization, be it among the developers who build new applications or the management team.
|