This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP JSEC CVE Details"
(→Github) |
|||
| (27 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
=Main= | =Main= | ||
| − | + | <!-- DO NOT ALTER OR REMOVE THE TEXT ON NEXT LINE --> | |
| − | <div style="width:100%;height: | + | <div style="width:100%;height:100px;border:0,margin:0;overflow: hidden;">[[Image:OWASP Inactive Banner.jpg|800px| link=https://www.owasp.org/index.php/OWASP_Project_Stages#tab=Inactive_Projects]] </div> |
{| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | {| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | ||
| Line 8: | Line 8: | ||
==OWASP JSEC CVE Details== | ==OWASP JSEC CVE Details== | ||
| − | |||
| − | + | OWASP JSEC CVE DETAILS is an opensource application developed in Java that uses the api provided by cvedetails.com to receive latest CVE updates. Apart from fetching the latest CVEs, it can also be used to search for expoits and vulnerabilities from exploitsearch.net. This tool is used to find and gather information related to CVEs. | |
| − | + | The Common Vulnerabilities and Exposures (CVE) system provides a reference-method for publicly known information-security vulnerabilities and exposures. MITRE Corporation maintains the system, with funding from the National Cyber Security Division of the United States Department of Homeland Security.CVE is used by the Security Content Automation Protocol, and CVE IDs are listed on MITRE's system[2] as well as the US National Vulnerability Database. | |
| − | |||
| + | This project has now been officially approved by OWASP. Here is the link to the project details on OWASP Website https://www.owasp.org/index.php/OWASP_JSEC_CVE_Details | ||
| − | |||
| − | |||
| + | www.cvedetails.com provides an easy to use web interface to CVE vulnerability data.You can browse for vendors, products and versions and view cve entries, vulnerabilities,related to them. You can view statistics about vendors, products and versions of products.CVE details are displayed in a single, easy to use page | ||
| − | + | www.exploitsearch.net, is an attempt at cross referencing/correlating exploits and vulnerability data from various sources and making the resulting database available to everyone. | |
| − | |||
| − | + | * [Features] | |
| + | * [+] Fetch Recent CVEs | ||
| + | * [New Features included in v2.0] | ||
| + | * [+] Search for vulnerabilities of different platform/application/categories | ||
| + | * [+] Search CVEs | ||
| + | * [+] Search POC & Exploits | ||
| − | |||
| − | |||
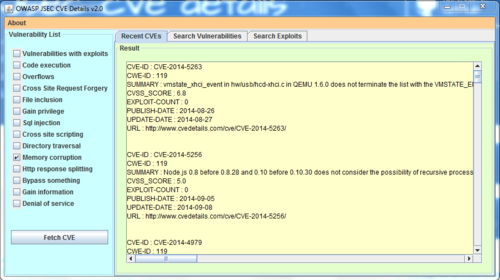
| − | + | ==Description== | |
| + | [[File:JsecV2.PNG|500px]] | ||
| − | == | + | ==Licensing== |
| + | OWASP JSEC CVE Details is free to use. It is licensed under the GNU GPL v3 license. | ||
| − | + | | valign="top" style="padding-left:25px;width:200px;border-right: 1px dotted gray;padding-right:25px;" | | |
| + | {| width="200" cellpadding="2" | ||
| + | |- | ||
| + | | align="center" valign="top" width="50%" rowspan="2"| [[File:New projects.png|100px|link=https://www.owasp.org/index.php/OWASP_Project_Stages#tab=Incubator_Projects]] | ||
| + | | align="center" valign="top" width="50%"| [[File:Owasp-builders-small.png|link=]] | ||
| + | |- | ||
| + | | align="center" valign="top" width="50%"| [[File:Owasp-defenders-small.png|link=]] | ||
| + | |- | ||
| + | | colspan="2" align="center" | [[File:Cc-button-y-sa-small.png|link=http://creativecommons.org/licenses/by-sa/3.0/]] | ||
| + | |- | ||
| + | | colspan="2" align="center" | [[File:Project_Type_Files_CODE.jpg|link=]] | ||
| + | |} | ||
| − | == | + | == News and Events == |
| + | * [13 June 2014] Released the project as opensource | ||
| + | * [17 August 2014] Requested for OWASP project approval | ||
| + | * [20 August 2014] Project Proposal Accepted | ||
| + | * [22 September 2014 ] v2.0 released | ||
| + | * [1st October 2016 ] v2.1 Released | ||
| + | * [10th October 2016 ] v3.0 Planned to be released | ||
| − | + | | valign="top" style="padding-left:25px;width:200px;" | | |
| + | == Project Leader == | ||
| − | + | [mailto:[email protected] Dibyendu Sikdar] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | == Related With == | ||
| − | + | [http://www.sillycon.org SillyCon - OWASP Kolkata Chapter] | |
| − | == | + | == Github == |
| − | [https://github.com/dibsy/JSEC_CVE_DETAILS | + | [https://github.com/dibsy/OWASP-JSEC_CVE_DETAILS] |
== Quick Download == | == Quick Download == | ||
| Line 66: | Line 82: | ||
[https://lists.owasp.org/mailman/listinfo/owasp-jsec-cve-details Sign up!] | [https://lists.owasp.org/mailman/listinfo/owasp-jsec-cve-details Sign up!] | ||
| − | |||
| − | |||
| − | |||
| − | + | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
|} | |} | ||
| Line 93: | Line 90: | ||
=FAQs= | =FAQs= | ||
| − | ; | + | ; How to contribute ? |
| − | : | + | : 1.Clone or Download the Project |
| + | : 2.Open Eclipse | ||
| + | : 3.Import the project as existing projects in workspace | ||
| + | : 4.Run the JSEC.java file | ||
| + | |||
| − | ; | + | ; How to get the executable Jar file |
| − | : | + | : Either you import the project and export it as a JAR or |
| + | : Download from sourceforge https://sourceforge.net/projects/jseccvedetails/ | ||
= Acknowledgements = | = Acknowledgements = | ||
==Volunteers== | ==Volunteers== | ||
| − | + | The primary contributors to date have been: | |
| − | * | + | * Debarshi Das - Designing OWASP Logo |
| − | |||
==Others== | ==Others== | ||
| − | * | + | * Adam - Exploit Search (exploitsearch.net) |
| − | * | + | * Admin - cvedetails.com |
= Road Map and Getting Involved = | = Road Map and Getting Involved = | ||
| + | *Updates : October 2016 | ||
| + | *v2.1 source code has been released in Github | ||
| + | *v2.1 has POCs and Exploits searching capabilities | ||
| + | *v3.0 is planned to to be released on 2nd Week of October 2016 | ||
| + | *v3.0 has features of scanning is being added | ||
| + | *v4.0 will have cloud integration and REST apis | ||
| + | |||
| + | |||
As of August, 2014, the priorities are: | As of August, 2014, the priorities are: | ||
| Line 116: | Line 125: | ||
*Using this tool the user can receive latest CVE details and choosing the type of vulnerability i.e. CSRF / XSS / etc | *Using this tool the user can receive latest CVE details and choosing the type of vulnerability i.e. CSRF / XSS / etc | ||
*Other features to be added in future are like searching the Proof of Concepts for every CVE that is listed . | *Other features to be added in future are like searching the Proof of Concepts for every CVE that is listed . | ||
| − | + | ||
Involvement in the development and promotion of JSEC CVE Details is actively encouraged! | Involvement in the development and promotion of JSEC CVE Details is actively encouraged! | ||
You do not have to be a security expert in order to contribute. | You do not have to be a security expert in order to contribute. | ||
Some of the ways you can help: | Some of the ways you can help: | ||
| − | * | + | * Find bugs in the code |
| − | * | + | * Suggest ideas |
| − | |||
| − | |||
=Project About= | =Project About= | ||
Latest revision as of 21:09, 30 September 2016
OWASP JSEC CVE DetailsOWASP JSEC CVE DETAILS is an opensource application developed in Java that uses the api provided by cvedetails.com to receive latest CVE updates. Apart from fetching the latest CVEs, it can also be used to search for expoits and vulnerabilities from exploitsearch.net. This tool is used to find and gather information related to CVEs. The Common Vulnerabilities and Exposures (CVE) system provides a reference-method for publicly known information-security vulnerabilities and exposures. MITRE Corporation maintains the system, with funding from the National Cyber Security Division of the United States Department of Homeland Security.CVE is used by the Security Content Automation Protocol, and CVE IDs are listed on MITRE's system[2] as well as the US National Vulnerability Database. This project has now been officially approved by OWASP. Here is the link to the project details on OWASP Website https://www.owasp.org/index.php/OWASP_JSEC_CVE_Details
www.cvedetails.com provides an easy to use web interface to CVE vulnerability data.You can browse for vendors, products and versions and view cve entries, vulnerabilities,related to them. You can view statistics about vendors, products and versions of products.CVE details are displayed in a single, easy to use page www.exploitsearch.net, is an attempt at cross referencing/correlating exploits and vulnerability data from various sources and making the resulting database available to everyone.
DescriptionLicensingOWASP JSEC CVE Details is free to use. It is licensed under the GNU GPL v3 license. |
News and Events
|
Project LeaderRelated WithSillyCon - OWASP Kolkata Chapter GithubQuick DownloadEmail List
| |||||||
- How to contribute ?
- 1.Clone or Download the Project
- 2.Open Eclipse
- 3.Import the project as existing projects in workspace
- 4.Run the JSEC.java file
- How to get the executable Jar file
- Either you import the project and export it as a JAR or
- Download from sourceforge https://sourceforge.net/projects/jseccvedetails/
Volunteers
The primary contributors to date have been:
- Debarshi Das - Designing OWASP Logo
Others
- Adam - Exploit Search (exploitsearch.net)
- Admin - cvedetails.com
- Updates : October 2016
- v2.1 source code has been released in Github
- v2.1 has POCs and Exploits searching capabilities
- v3.0 is planned to to be released on 2nd Week of October 2016
- v3.0 has features of scanning is being added
- v4.0 will have cloud integration and REST apis
As of August, 2014, the priorities are:
- This tool uses the api provided by cvedetails.com.
- Using this tool the user can receive latest CVE details and choosing the type of vulnerability i.e. CSRF / XSS / etc
- Other features to be added in future are like searching the Proof of Concepts for every CVE that is listed .
Involvement in the development and promotion of JSEC CVE Details is actively encouraged!
You do not have to be a security expert in order to contribute.
Some of the ways you can help:
- Find bugs in the code
- Suggest ideas
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||||