This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP BeNeLux-Days 2018"
(→Talks) |
m (Fix spelling) |
||
| Line 19: | Line 19: | ||
* Niels Tanis | * Niels Tanis | ||
* Jeroen Willemsen | * Jeroen Willemsen | ||
| − | * | + | * Björn Kimminich |
* Ralph Moonen | * Ralph Moonen | ||
}} | }} | ||
Revision as of 17:26, 10 October 2018

Confirmed Conference Speakers
- David Scrobonia
- Niels Tanis
- Jeroen Willemsen
- Björn Kimminich
- Ralph Moonen
Confirmed Trainers
- Andrew Martin
- David Scrobonia
OWASP BeNeLux conference is free, but registration is required!
The OWASP BeNeLux Program Committee
- Bart De Win / Sebastien Deleersnyder/ Lieven Desmet/ David Mathy, OWASP Belgium
- Martin Knobloch / Joren Poll, OWASP Netherlands
- Jocelyn Aubert, OWASP Luxembourg
Tweet!
Event tag is #owaspbnl18
Donate to OWASP BeNeLux
OWASP BeNeLux conference is free, but registration is required!
OWASP BeNeLux training is reserved for OWASP members, and registration is required!
To support the OWASP organisation, we ask training attendees to consider becoming an OWASP member, it's only US$50! Check out the Membership page to find out more.
To support the OWASP organisation, consider to become a member, it's only US$50! Check out the Membership page to find out more.
Address
Venue:
Congres- en Erfgoedcentrum Lamot Van Beethovenstraat 8-10 2800 Mechelen Belgium
Parking:
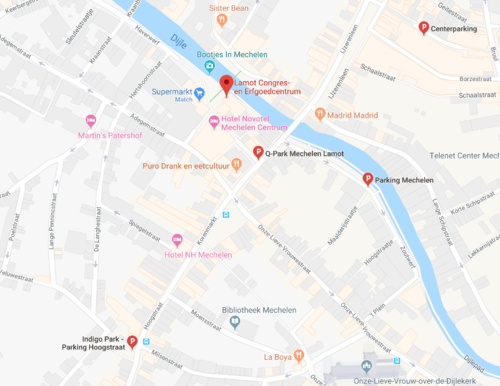
Find your parking on Google Maps
How to reach the venue?
Public transport
You can reach the Mechelen's train station from Antwerpen or Brussels. The Lamot conference center is 10 min away by bus (line 1).
Or you can choose to walk for 15 min (1.2 km).
By car
From Brussels:
Follow the E19 Brussels / Antwerpen and take the exit 10.
Follow the N1 until the R12 (take a left) and turn to the right at the "Brusselpoort" into the Hoogstraat to reach one of the parkings.
From Antwerpen:
Follow the E19 Brussels / Antwerpen and take the exit 9.
Follow the N16 until the R12 (take a right) and turn to the left at the "Brusselpoort" into the Hoogstraat to reach one of the parkings.
Hotels Nearby
Training Day is November 29th
Trainings
Kubernetes security by Andrew Martin
Abstract
Course Description
The course guides attendees through Linux container security in general, and progresses to advanced Kubernetes cluster security. It emphasises pragmatic threat modelling and risk assessment based on an understanding of the tools and primitives available, rather than dogmatic dos and don’ts.
Course Outline
- How to attack containerised workloads
- Enhanced container security
- How to attack Kubernetes
- Interactive production cluster hacking
- Hardening Kubernetes
- Locking down applications
- Security tooling and vendor landscape
Who Should Attend
This course is suitable for intermediate to advanced Kubernetes users who want to strengthen their security understanding. It is particularly beneficial for those operating Kubernetes in a high-compliance domain, or for established security professionals looking to update their skills for the cloud native world.
Bio
Andrew has a strong test-first engineering ethos gained architecting and deploying high-traffic web applications. Proficient in systems development, testing, and maintenance, he is comfortable profiling and securing every tier of a bare metal or cloud native application, and has battle-hardened experience delivering containerised solutions to enterprise clients. He is a co-founder at https://control-plane.io
Conference Day is November 30th
Talks
OWASP Zap by David Scrobonia
Abstract
Intoducing security testing tools to a QA or developers workflow can be difficult when the tools aren't easy or intuitive to use. Even for security professionals, the friction of cumbersome security tooling can prevent them from getting the most from a tool or being effective with their time.
The OWASP ZAP team is working to help enable developers, QA, and hackers alike with the ZAP Heads Up Display, a more user friendly way to engage with the security testing tool. The Heads Up Displays integrates ZAP directly in the browser providing all of the funcitonality of the tool via a heads up display. The goal is to make ZAP more accessible and enabling users, especially developers, to integrate security in their daily workflows.
This talk will discuss the importance of usable tools, design tradeoffs made to improve usability, the various browser technologies powering the HUD, and how you can start hacking with a heads up display.
Bio
David Scrobonia is a part of the Security Engineering team at Segment working to secure modern web apps and AWS infrastructure. He contributes to open source in his spare time and is a core team member of the OWASP ZAP project.
When Serverless Met Security… Serverless Security & Functions-as-a-Service (FaaS) by Niels Tanis
Abstract
Serverless is a design pattern for writing scalable applications in which Functions as a Service (FaaS) is one of the key building blocks. Every mayor Cloud Provider has got his own FaaS available. On Microsoft Azure there is Azure Functions, AWS has got Lambda and Cloud Functions can be used on the Google Cloud. All of these have a lot of similarities in the way they allow developers to create small event driven services.
From security perspective there are a lot of benefits when moving to a serverless architecture. There is no need to manage any of the machines and the underlying infrastructure. Dealing with updates, patches and infrastructure is the responsibility of the platform provider. FaaS are short lived processes which will be instantiated and destroyed in a matter of milliseconds making it more resilient to denial-of-services (DoS) and also makes it harder to attack and compromise.
But will all of this be sufficient to be ’secure’ or should we be worried about more? With serverless there is still a piece of software that will be developed, build, deployed and executed. It will also introduce a more complex architecture with corresponding attack surface which also makes it hard to monitor. What about the software supply chain and delivery pipeline? There still will be a need to patch your software for vulnerabilities in code and used 3rd party libraries. In this talk we will identify the security area’s we do need to focus on when developing serverless and define possible solutions for dealing with those problems.
Bio
Niels Tanis has got a background in .NET development, pentesting and security consultancy. He also holds the CSSLP certification and has been involved in breaking, defending and building secure applications. He joined Veracode in 2015 and right now he works as a security researcher on a variant of languages and technologies related to Veracode’s Binary Static Analysis service. He is married, father of 2 and lives in a small village just outside Amersfoort, The Netherlands.
Weaknesses in our voice communications network: from Blue Boxing to VoLTE by Ralph Moonen
Abstract
Voice over 4G, or VoLTE, brings back the phreaking 80's. Once again, after 3 decades, the signaling path of telephony is accessible to end users. No more R1, R2, C4 or C5 however: we now have SIP. As it turns out, the implementations of SIP and VoLTE in various European providers' 4G infrastructures, open up a host of possibilities. During our research over the past few years we have identified vulnerabilities in implementations such as txt message spoofing, subscriber enumeration, location determination (leakage of cell-ID and LAC), IMEI leakage and a potential SIM-card sharing attack.
During this talk we will begin with a little historic stroll of phone phreaking through notable events and discoveries over the years. Bridging the narrative over the last few decades, new technologies such as VoIP, Volte, and VoWiFi are introduced, explaining the 4G and VoLTE infrastructure components and protocols. Next, on a rooted Android phone, we will show what control the user has over the VoLTE stack using some standard tools and the IPv6 stack. This includes hidden activities in Android and extraction of IPsec keys from the VoLTE stack. We will show that it is possible to import keys to Wireshark and monitor the IPv6 SIP traffic and components. Finally, examples of the vulnerabilities in implementations such as txt message spoofing, subscriber enumeration, location determination (leakage of cell-ID and LAC), IMEI leakage and a potential SIM-card sharing attack will be explained.
Yes, a slightly technical nugget of knowledge, yet very accessible and a lot of fun!
Importance of presentation for involved audience
The phone systems of the world have always been of interest to everyone: from users who expect privacy, to intelligence agencies who want access. The privacy, integrity and confidentiality of voice communications over telecommunication networks is therefore of interest to anyone who uses mobile phones (i.e.: everyone). It is also typically a closed subject with very little research being done, relative to other security topics such as malware and application vulnerabilities. The combination of little research and high impact on everyone, makes that this topic deserves much more attention than it currently does. The VoLTE weaknesses we will describe are implementation dependent, and largely unpublished (i.e. new).
Bio
Ralph Moonen CISSP is Technical Director at Secura. Ralph is an old-school ethical hacker with 3 decades of experience as penetration tester, IT-auditor and security consultant. Now, as Technical Director, he is responsible for topics such as R&D and technical projects at Secura.
Juice Shop: OWASP's most broken Flagship by Björn Kimminich
Abstract
OWASP Juice Shop is an intentionally insecure webapp for security trainings written entirely in Javascript which encompasses the entire OWASP Top Ten and many more severe security flaws. In this talk, you'll learn about this open-source project and its capabilities first-hand from its creator. Join a “happy shopper round trip,” enjoy a hacking demo of some of the built-in challenges, witness how to re-theme the Juice Shop into a security awareness booster for your own company, and learn how to set it up for a capture-the-flag (CTF) event in less than 5 minutes!
Bio
Björn Kimminich is responsible for global IT architecture and application security at Kuehne + Nagel. On the side, he gives IT security lectures at the non-profit private university Nordakademie. Björn also is the project leader of the OWASP Juice Shop and a board member for the German OWASP chapter.
![]()
![]()
![]()
Fast forwarding Mobile Security with the MSTG by Jeroen Willemsen
Abstract
After the startup of the mobile security project in 2010, the mobile security project and its testing guides have seen quiet some evolution. All of this changed quiet intensively when, in 2016, the Mobile Application Security Verification Standard (MASVS) and the Mobile Application Security Testing Guide were created. Now, two years fast forward: where are we now? How can you use it as a pentester or a developer? We will start with introducing the current state of the MSTG and its side-projects and then show various demos on iOS and Android.
This talk is intended to teach people about the existence of mobile security and to give a call to action to everybody who is there.
Bio
Jeroen Willemsen is a Principal Security Architect at Xebia. With a love for mobile security, he recently became one of the projectleaders for the OMTG project (MASV & MSTG). Jeroen is more or less a jack of all trades with interest in infrastructure security, risk management and application security.
The Social Event is on Thursday, November 29th
If you want to join the social event, don't forget to register for it via the registration:
The social event details will be published very soon! Stay tuned.
Become a sponsor of OWASP BeNeLux!
There are 3 combined sponsorship packages (Gold, Silver or Bronze) that cover the BeNeLux chapter meetings 2019 and the BeNeLux OWASP Days 2018.
Download our sponsor brochure and contact us for questions or sponsorship confirmation!
Your sponsorship will be invested directly in the chapter meetings, supporting speaker and catering expenses.
The sponsorship will also be dedicated to cover the costs of the OWASP 2018 BeNeLux event.
Made possible by our Sponsors
Gold
Silver








