This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP BeNeLux-Days 2018"
| (122 intermediate revisions by 7 users not shown) | |||
| Line 1: | Line 1: | ||
| − | <center>[[Image: | + | <center>[[Image:OBNL18 Banner v2.png]]</center> |
<br><!-- Header --> | <br><!-- Header --> | ||
| Line 6: | Line 6: | ||
<!-- First tab --> | <!-- First tab --> | ||
= Information = | = Information = | ||
| − | == | + | |
| − | {{#switchtablink: | + | <p style="text-align:center">'''Thanks to all speakers and trainers, sponsors and volunteers who could make this 2018 edition a success.<br>'''</p> |
| − | * | + | |
| + | Sad you missed the conference? No problem, just have a look at the {{#switchtablink:Conference_Day|video recordings}}! | ||
| + | |||
| + | |||
| + | == Save the date == | ||
| + | |||
| + | <p style="text-align:center"><font color="red">'''In 2019 we will skip one year (we organised Global AppSec Amsterdam), See you next year in the Netherlands: 26 and 27 November 2020'''</font></p> | ||
| + | |||
| + | == Confirmed Conference Speakers == | ||
| + | |||
| + | <!--{{#switchtablink:Conference_Day|<p>--> | ||
| + | |||
| + | * David Scrobonia | ||
| + | * Niels Tanis | ||
| + | * Jeroen Willemsen | ||
| + | * Björn Kimminich | ||
| + | * Ralph Moonen | ||
| + | * Jo Van Bulck | ||
| + | * Lennert Wouters | ||
| + | * Nick Drage | ||
| + | <!-- | ||
}} | }} | ||
| + | --> | ||
| + | |||
| + | == Confirmed Trainers == | ||
| − | + | <!-- | |
| − | {{#switchtablink: | + | {{#switchtablink:Training Day|<p> |
| − | * | + | --> |
| − | + | * Andrew Martin | |
| + | * David Scrobonia | ||
| + | * Jeroen Beckers - Stephanie Vanroelen | ||
| − | + | <!-- | |
| − | |||
| − | |||
}} | }} | ||
| + | --> | ||
== OWASP BeNeLux conference is free, but registration is required! == | == OWASP BeNeLux conference is free, but registration is required! == | ||
| − | + | The conference is closed.<br> | |
| + | |||
| + | '''To support the OWASP organisation, consider to become a member, it's only US$50! Check out the [[Membership]] page to find out more.''' | ||
| + | <br> | ||
== The OWASP BeNeLux Program Committee == | == The OWASP BeNeLux Program Committee == | ||
| − | * | + | |
| − | *Martin Knobloch / Joren Poll, OWASP Netherlands | + | * Sebastien Deleersnyder / Lieven Desmet / David Mathy / Thomas Herlea / Stella Dineva / Adolfo Solero / Bart De Win, [[Belgium|OWASP Belgium]] |
| − | * | + | * Martin Knobloch / Joren Poll / Edwin Gozeling, [[Netherlands|OWASP Netherlands]] |
| − | + | * [[Luxembourg|OWASP Luxembourg]] | |
== Tweet! == | == Tweet! == | ||
| + | |||
Event tag is [http://twitter.com/#search?q=%23owaspbnl17 #owaspbnl18] | Event tag is [http://twitter.com/#search?q=%23owaspbnl17 #owaspbnl18] | ||
| − | + | ||
== Donate to OWASP BeNeLux == | == Donate to OWASP BeNeLux == | ||
| + | |||
[https://co.clickandpledge.com/?wid=72689 Donate] | [https://co.clickandpledge.com/?wid=72689 Donate] | ||
<!-- Second tab --> | <!-- Second tab --> | ||
| + | = Registration = | ||
| − | = Registration = | + | == Registration is closed == |
| + | '''To support the OWASP organisation, consider to become a member, it's only US$50! Check out the [[Membership]] page to find out more.''' | ||
| − | + | <!-- Third tab --> | |
| − | <!-- | + | |
| − | + | = Venue = | |
| − | |||
| − | == | + | == Address == |
| − | |||
| − | |||
| − | < | + | <table width="100%"> |
| − | + | <tr valign="top"> | |
| − | + | <td width="50%"> | |
| − | < | + | === Training venue === |
| − | |||
| − | |||
| − | |||
| − | |||
| + | '''Novotel Mechelen Centrum''' | ||
| + | Van Beethovenstraat 1 | ||
| + | 2800 Mechelen | ||
| + | Belgium | ||
| − | < | + | [https://goo.gl/maps/WxErtbWADqC2 Google maps] |
| + | </td> | ||
| + | <td width="50%"> | ||
| + | === Conference venue === | ||
| − | + | '''Congres- en Erfgoedcentrum Lamot''' | |
| + | Van Beethovenstraat 8-10 | ||
| + | 2800 Mechelen | ||
| + | Belgium | ||
| − | + | [https://goo.gl/maps/gZ9icR178w52 Google map] | |
| + | </td> | ||
| + | </tr> | ||
| + | </table> | ||
| + | <br /> | ||
| + | [[File:Mechelen-Lamot.jpg|350px|Lamot conference center]] | ||
| + | [[File:Mechelen-lamot-center-auditorium.jpg|350px|Auditorium]]<br /> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | Parking:<br /> | |
| + | [[File:Parking lots around Lamot Conference center Mechelen.png|500px|Parking facilities]]<br /> | ||
| + | [https://goo.gl/maps/Q5TD7hoTuUu Find your parking on Google Maps] | ||
=== How to reach the venue? === | === How to reach the venue? === | ||
| − | |||
| − | |||
| − | ' | + | ==== Public transport ==== |
| − | + | ||
| + | You can reach the Mechelen's train station from Antwerpen or Brussels. | ||
| + | The Lamot conference center is 10 min away by bus (line 1). | ||
| + | |||
| + | Or you can choose to walk for 15 min (1.2 km). | ||
| + | |||
| + | |||
| + | ==== By car ==== | ||
| + | |||
| + | ===== From Brussels: ===== | ||
| + | Follow the E19 Brussels / Antwerpen and take the exit 10. <br> Follow the N1 until the R12 (take a left) and turn to the right at the "Brusselpoort" into the Hoogstraat to reach one of the parkings. | ||
| + | |||
| + | ===== From Antwerpen: ===== | ||
| + | Follow the E19 Brussels / Antwerpen and take the exit 9. <br> Follow the N16 until the R12 (take a right) and turn to the left at the "Brusselpoort" into the Hoogstraat to reach one of the parkings. | ||
| + | |||
| + | |||
| + | === Hotels Nearby === | ||
| + | [https://www.google.com/maps/d/viewer?mid=1eYMYmwXKuAsTilKgpAtyYtfMA7A&ll=51.02648134397288%2C4.47819800000002&z=15 Hotels around the Lamot conference center] | ||
| − | |||
| − | |||
<!-- Fourth tab --> | <!-- Fourth tab --> | ||
| − | = | + | = Training Day = |
| − | + | ||
| + | '''Training Day is November 29th''' | ||
| − | == | + | == Training Venue == |
| + | |||
| + | The trainings will take place in the '''Novotel Mechelen Centrum''' hotel:<br> | ||
| + | Van Beethovenstraat 1<br> | ||
| + | 2800 Mechelen<br> | ||
| + | [https://goo.gl/maps/WxErtbWADqC2 Google maps] | ||
| + | |||
| + | == Agenda== | ||
| − | |||
{| class="wikitable" | {| class="wikitable" | ||
| − | ! Time !! Description !! | + | ! Time !! Description !! Training 1 !! Training 2 !! Training 3 |
| + | |- | ||
| + | ! !! !! (Hof van Busleyden 1) !! (Hof van Busleyden 2) !! (Hof van Kamerijk) | ||
|- | |- | ||
| 08h30 - 9h30 | | 08h30 - 9h30 | ||
| − | | | + | | style="text-align: center; background: grey; color: white;" colspan="5" | ''Registration'' |
|- | |- | ||
| 09h30 - 11h00 || Training | | 09h30 - 11h00 || Training | ||
| − | | | + | | style="width:100px;" rowspan="7" | [[#TRAINING_1 | Kubernetes security]] by Andrew Martin |
| − | | | + | | style="width:100px;" rowspan="7" | [[#TRAINING_2 | OWASP Zap Training]] by David Scrobonia |
| − | | | + | | style="width:100px;" rowspan="7" | [[#TRAINING_3 | Android security workshop]] by Jeroen Beckers & Stephanie Vanroelen |
|- | |- | ||
| 11h00 - 11h30 || ''Coffee Break'' | | 11h00 - 11h30 || ''Coffee Break'' | ||
| Line 117: | Line 175: | ||
| 16h00 - 17h30 || Training | | 16h00 - 17h30 || Training | ||
|} | |} | ||
| + | |||
| + | <font color="red">Choose the most appropriate training as they will be hosted at the same time.</font> | ||
== Trainings == | == Trainings == | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | ====Abstract ==== | + | === <span id="TRAINING_1">Training 1 - Kubernetes security by Andrew Martin</span> === |
| − | + | ||
| − | The | + | ==== Abstract ==== |
| − | + | ||
| − | + | ===== Course Description ===== | |
| − | + | The course guides attendees through Linux container security in general, and progresses to advanced Kubernetes cluster security. It emphasises pragmatic threat modelling and risk assessment based on an understanding of the tools and primitives available, rather than dogmatic dos and don’ts. | |
| − | + | ||
| − | + | ===== Course Outline ===== | |
| + | * How to attack containerised workloads | ||
| + | * Enhanced container security | ||
| + | * How to attack Kubernetes | ||
| + | * Interactive production cluster hacking | ||
| + | * Hardening Kubernetes | ||
| + | * Locking down applications | ||
| + | * Security tooling and vendor landscape | ||
| + | |||
| + | ===== Who Should Attend ===== | ||
| + | This course is suitable for intermediate to advanced Kubernetes users who want to strengthen their security understanding. It is particularly beneficial for those operating Kubernetes in a high-compliance domain, or for established security professionals looking to update their skills for the cloud native world. | ||
| + | |||
| + | ===== Participant requirements ===== | ||
| + | Just a laptop with an SSH client please, ssh or PuTTY. | ||
| + | |||
| + | ==== Bio ==== | ||
| + | |||
| + | Andrew has a strong test-first engineering ethos gained architecting and deploying high-traffic web applications. Proficient in systems development, testing, and maintenance, he is comfortable profiling and securing every tier of a bare metal or cloud native application, and has battle-hardened experience delivering containerised solutions to enterprise clients. He is a co-founder at https://control-plane.io | ||
| + | |||
| + | === <span id="TRAINING_2">Training 2 - OWASP Zap Training by David Scrobonia</span> === | ||
| + | |||
| + | ==== Abstract ==== | ||
| + | |||
| + | This hands on course will start with the basics of using ZAP attack proxy and finish with leveraging it's API to integrate ZAP within you CI/CD processes. Along the way we will be practicing techniques by attacking the OWASP JuiceShop, an intentionally vulnerable web application. | ||
| − | + | ==== Audience ==== | |
| − | + | This couse is designed for both new and experienced users. No knowledge or experience with ZAP is required, but even those familiar with ZAP will learn something new. | |
| − | |||
| − | ==== | + | ==== Contents ==== |
| − | + | # Basic Techniques & Manual Testing | |
| + | # Advanced Techniques & Automated Testing | ||
| + | # Scripting with ZAP | ||
| + | # Using ZAP within your CI/CD Pipeline | ||
| + | |||
| + | ===== Participant requirements ===== | ||
| + | Please come prepared with the following tools installed: | ||
| + | * ZAP (https://github.com/zaproxy/zaproxy/wiki/Downloads#zap-270-standard) | ||
| + | * docker | ||
| − | + | If you have any trouble with the setup please feel free to reach out to davidscrobonia at gmail with questions. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | ==== | + | ==== Bio ==== |
| − | |||
| − | + | David Scrobonia is a part of the Security Engineering team at Segment working to secure modern web apps and AWS infrastructure. He contributes to open source in his spare time and is a core team member of the OWASP ZAP project. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | === <span id="TRAINING_3">Training 3 - Android security workshop by Jeroen Beckers & Stephanie Vanroelen</span> === | ||
| − | ==== | + | ==== Abstract ==== |
| − | |||
| − | + | In this workshop, participants will come in contact with the basics of | |
| − | + | Android application security. Through hands-on exercises, Jeroen and | |
| − | + | Stephanie will show which mistakes can be made, both at the design and | |
| − | + | implementation level, that can compromise the security of both the | |
| − | + | application and the backend server. Although no real prior experience | |
| − | + | with Android is needed, some basic knowledge on programming is advised. | |
| − | |||
| − | ==== | + | ==== Participation requirements ==== |
| − | + | * Basic linux / terminal knowledge | |
| + | * Be able to understand the OWASP Top 10 (Not Mobile) | ||
| + | * Laptop with VirtualBox / VMWare (At least 8GB of RAM) | ||
| − | ==== | + | ==== Bio ==== |
| − | |||
| − | + | Jeroen Beckers is a security researcher at NVISO. He focusses mainly on | |
| − | + | mobile applications for Android/iOS and sometimes even Windows Phone | |
| − | + | (yes, some people actually use it!). Apart from breaking mobile | |
| + | applications, he also gives security trainings and presentations at | ||
| + | conferences.<br> | ||
| + | <br> | ||
| + | Stephanie Vanroelen is an IT security consultant currently focussing on Web and | ||
| + | Mobile Application Security. Her experiences in organizing IT Security | ||
| + | conferences such as BruCON and CyberSKool help her with project | ||
| + | management and communication skills. In her free time she pretends to be | ||
| + | Godzilla :). | ||
| − | |||
| − | |||
<!-- Fifth tab --> | <!-- Fifth tab --> | ||
| + | = Conference Day = | ||
| − | + | '''Conference Day is November 30th''' | |
| − | |||
| + | == Agenda == | ||
| − | |||
{| class="wikitable" | {| class="wikitable" | ||
! width="120pt" | Time | ! width="120pt" | Time | ||
! width="190pt" | Speaker | ! width="190pt" | Speaker | ||
! width="400pt" | Topic | ! width="400pt" | Topic | ||
| − | ! width="100pt" | + | ! width="100pt" | Media |
|- | |- | ||
| − | | 08h30 - | + | | 08h30 - 09h15 |
| − | | | + | | style="text-align: center; background: grey; color: white" colspan="3" | ''Registration / [[#CyberWayFinder | Women in cybersecurity (CyberWayFinder)]]'' |
|- | |- | ||
| − | | | + | | 09h15 - 09h30 |
| − | | | + | | style="text-align: center; background: grey; color: white" colspan="3" | ''Opening'' |
|- | |- | ||
| − | | | + | | 09h30 - 10h15 |
| − | + | | [[#TALK_0930 | Lennert Wouters]] | |
| − | | | + | | [[#TALK_0930 | Fast, Furious and Insecure: Passive Keyless Entry and Start in Modern Supercars]] |
| + | | | ||
|- | |- | ||
| − | | | + | | 10h15 - 11h00 |
| − | | | + | | [[#TALK_1015 | Ralph Moonen]] |
| − | + | | [[#TALK_1015 | Weaknesses in our voice communications network: from Blue Boxing to VoLTE]] | |
| − | + | | [[Media:OWASP BeNeLux 2018 Ralph Moonen - Weaknesses in our voice communications network - from Blue Boxing to VoLTE compressed.pdf | Slides]]<br> | |
| + | [https://youtu.be/Rl7VabjEd_A Video] | ||
|- | |- | ||
| − | | | + | | 11h00 - 11h30 |
| − | | | + | | style="text-align: center;background: grey; color: white" colspan="3" | ''Morning Break'' |
|- | |- | ||
| − | | | + | | 11h30 - 12h15 |
| − | | | + | | [[#TALK_1130 | Niels Tanis]] |
| − | | [[Media: | + | | [[#TALK_1130 | When Serverless Met Security… Serverless Security & Functions-as-a-Service (FaaS)]] |
| + | | [[Media:OWASP BeNeLux 2018 Niels Tanis - When Serverless Met Security.pdf | Slides]] <br> | ||
| + | [https://youtu.be/wuvGmXN0n6Q Video] | ||
|- | |- | ||
| − | | | + | | 12h15 - 13h00 |
| − | + | | [[#TALK_1215 | David Scrobonia]] | |
| − | | [[Media:OWASP BeNeLux | + | | [[#TALK_1215 | OWASP Zap]] |
| + | | [[Media:OWASP BeNeLux 2018 David Scrobonia OWASP Zap.pdf | Slides]]<br> | ||
| + | [https://youtu.be/iaZaPuQ6ams Video] | ||
|- | |- | ||
| − | | | + | | 13h00 - 14h00 |
| − | | | + | | style="text-align: center;background: grey; color: white" colspan="3" | ''Lunch'' |
|- | |- | ||
| − | | | + | | 14h00 - 14h45 |
| − | + | | [[#TALK_1400 | Björn Kimminich]] | |
| − | | [[Media:OWASP BeNeLux- | + | | [[#TALK_1400 | Juice Shop: OWASP's most broken Flagship]] |
| + | | [[Media:OWASP BeNeLux 2018 Bjoern Kimminich - Juice Shop - OWASP's most broken Flagship.pdf | Slides]]<br> | ||
| + | [https://youtu.be/Lu0-kDdtVf4 Video] | ||
|- | |- | ||
| − | | | + | | 14h45 - 15h30 |
| − | + | | [[#TALK_1445 | Jo Van Bulck]] | |
| − | | | + | | [[#TALK_1445 | Leaky Processors: Stealing Your Secrets with Foreshadow]] |
| + | | [[Media:OWASP BeNeLux 2018 Jo Van Bulck - Leaky Processors - Stealing Your Secrets with Foreshadow.pdf | Slides]] <br> | ||
| + | [https://youtu.be/le60NzmxU6s Video] | ||
|- | |- | ||
| − | | | + | | 15h30 - 16h00 |
| − | | | + | | style="text-align: center;background: grey; color: white" colspan="3" | ''Afternoon Break'' |
|- | |- | ||
| − | | | + | | 16h00 - 16h45 |
| − | + | | [[#TALK_1600 | Jeroen Willemsen]] | |
| − | | [[Media:OWASP BeNeLux- | + | | [[#TALK_1600 | Fast forwarding Mobile Security with the MSTG]] |
| + | | [[Media:OWASP BeNeLux 2018 Jeroen Willemsen - Fast forwarding Mobile Security with the MSTG compressed.pdf | Slides ]]<br> | ||
| + | [https://youtu.be/WI2_cP48TnA Video] | ||
|- | |- | ||
| − | | | + | | 16h45 - 17h30 |
| − | + | | [[#TALK_1645 | Nick Drage]] | |
| − | | [[Media:OWASP BeNeLux- | + | | [[#TALK_1645 | Lessons from the legion (The OWASP BeNeLux Remix)]] |
| + | | [[Media:OWASP BeNeLux 2018 Nick Drage - Lessons from the Legion compressed.pdf | Slides]]<br> | ||
| + | [https://youtu.be/516Z420BgkE Video] | ||
|- | |- | ||
| − | | | + | | 17h30 - 17h45 |
| − | | | + | | style="text-align: center;background: grey; color: white" colspan="3" | ''Closing'' |
|} | |} | ||
| − | < | + | == Talks == |
| + | |||
| + | === <span id="TALK_0930">Fast, Furious and Insecure: Passive Keyless Entry and Start in Modern Supercars by Lennert Wouters</span> === | ||
| + | |||
| + | ==== Abstract ==== | ||
| − | + | The security of immobiliser and Remote Keyless Entry systems has been extensively studied over the past years. Passive Keyless Entry and Start systems, which are currently deployed in luxury vehicles, have not received as much attention. | |
| + | During this presentation we will share the techniques used in reverse engineering the Tesla Model S Passive Keyless Entry and Start system. We will discuss multiple security weaknesses in the system including the use of an inadequate proprietary cipher using 40-bit keys, the lack of mutual authentication in the challenge-response protocol, hardware configuration mistakes and the absence of security partitioning.<br> | ||
| + | We verified our findings by implementing a proof of concept attack allowing us to clone a Tesla Model S key fob in a matter of seconds with low cost commercial off the shelf equipment.<br> | ||
| + | Finally, we will share our experience with the responsible disclosure of these finding to Tesla Motors and other likely affected manufacturers such as McLaren, Karma Automotive and Triumph Motorcycles as they all use the same system developed by Pektron. | ||
| − | |||
| − | |||
| − | |||
====Bio==== | ====Bio==== | ||
| − | |||
| − | |||
| − | |||
| − | |||
| + | Lennert Wouters is a PhD researcher at the Computer Security and Industrial Cryptography (COSIC) research group at KU Leuven. His research interests involve hardware security of connected embedded devices and side channel attacks. | ||
| + | |||
| + | === <span id="TALK_1015">Weaknesses in our voice communications network: from Blue Boxing to VoLTE by Ralph Moonen</span> === | ||
| + | |||
| + | ==== Abstract ==== | ||
| + | |||
| + | Voice over 4G, or VoLTE, brings back the phreaking 80's. Once again, after 3 decades, the signaling path of telephony is accessible to end users. No more R1, R2, C4 or C5 however: we now have SIP. As it turns out, the implementations of SIP and VoLTE in various European providers' 4G infrastructures, open up a host of possibilities. During our research over the past few years we have identified vulnerabilities in implementations such as txt message spoofing, subscriber enumeration, location determination (leakage of cell-ID and LAC), IMEI leakage and a potential SIM-card sharing attack.<br> | ||
| + | During this talk we will begin with a little historic stroll of phone phreaking through notable events and discoveries over the years. Bridging the narrative over the last few decades, new technologies such as VoIP, Volte, and VoWiFi are introduced, explaining the 4G and VoLTE infrastructure components and protocols. Next, on a rooted Android phone, we will show what control the user has over the VoLTE stack using some standard tools and the IPv6 stack. This includes hidden activities in Android and extraction of IPsec keys from the VoLTE stack. We will show that it is possible to import keys to Wireshark and monitor the IPv6 SIP traffic and components. Finally, examples of the vulnerabilities in implementations such as txt message spoofing, subscriber enumeration, location determination (leakage of cell-ID and LAC), IMEI leakage and a potential SIM-card sharing attack will be explained.<br> | ||
| + | Yes, a slightly technical nugget of knowledge, yet very accessible and a lot of fun!<br> | ||
| + | <br> | ||
| + | '''Importance of presentation for involved audience'''<br> | ||
| + | The phone systems of the world have always been of interest to everyone: from users who expect privacy, to intelligence agencies who want access. The privacy, integrity and confidentiality of voice communications over telecommunication networks is therefore of interest to anyone who uses mobile phones (i.e.: everyone). It is also typically a closed subject with very little research being done, relative to other security topics such as malware and application vulnerabilities. The combination of little research and high impact on everyone, makes that this topic deserves much more attention than it currently does. The VoLTE weaknesses we will describe are implementation dependent, and largely unpublished (i.e. new). | ||
| + | |||
| + | ==== Bio ==== | ||
| + | |||
| + | Ralph Moonen CISSP is Technical Director at Secura. Ralph is an old-school ethical hacker with 3 decades of experience as penetration tester, IT-auditor and security consultant. Now, as Technical Director, he is responsible for topics such as R&D and technical projects at Secura. | ||
| + | |||
| + | === <span id="TALK_1130">When Serverless Met Security… Serverless Security & Functions-as-a-Service (FaaS) by Niels Tanis</span> === | ||
| + | |||
| + | ==== Abstract ==== | ||
| + | |||
| + | Serverless is a design pattern for writing scalable applications in which Functions as a Service (FaaS) is one of the key building blocks. Every mayor Cloud Provider has got his own FaaS available. On Microsoft Azure there is Azure Functions, AWS has got Lambda and Cloud Functions can be used on the Google Cloud. All of these have a lot of similarities in the way they allow developers to create small event driven services. <br> | ||
| + | From security perspective there are a lot of benefits when moving to a serverless architecture. There is no need to manage any of the machines and the underlying infrastructure. Dealing with updates, patches and infrastructure is the responsibility of the platform provider. FaaS are short lived processes which will be instantiated and destroyed in a matter of milliseconds making it more resilient to denial-of-services (DoS) and also makes it harder to attack and compromise. <br> | ||
| + | But will all of this be sufficient to be ’secure’ or should we be worried about more? With serverless there is still a piece of software that will be developed, build, deployed and executed. It will also introduce a more complex architecture with corresponding attack surface which also makes it hard to monitor. What about the software supply chain and delivery pipeline? There still will be a need to patch your software for vulnerabilities in code and used 3rd party libraries. In this talk we will identify the security area’s we do need to focus on when developing serverless and define possible solutions for dealing with those problems. | ||
| + | |||
| + | ==== Bio ==== | ||
| + | |||
| + | Niels Tanis has got a background in .NET development, pentesting and security consultancy. He also holds the CSSLP certification and has been involved in breaking, defending and building secure applications. He joined Veracode in 2015 and right now he works as a security researcher on a variant of languages and technologies related to Veracode’s Binary Static Analysis service. He is married, father of 2 and lives in a small village just outside Amersfoort, The Netherlands. | ||
| + | |||
| + | |||
| + | === <span id="TALK_1215">OWASP Zap by David Scrobonia</span> === | ||
| + | |||
| + | ==== Abstract ==== | ||
| + | |||
| + | Intoducing security testing tools to a QA or developers workflow can be difficult when the tools aren't easy or intuitive to use. Even for security professionals, the friction of cumbersome security tooling can prevent them from getting the most from a tool or being effective with their time.<br> | ||
| + | The OWASP ZAP team is working to help enable developers, QA, and hackers alike with the ZAP Heads Up Display, a more user friendly way to engage with the security testing tool. The Heads Up Displays integrates ZAP directly in the browser providing all of the funcitonality of the tool via a heads up display. The goal is to make ZAP more accessible and enabling users, especially developers, to integrate security in their daily workflows.<br> | ||
| + | This talk will discuss the importance of usable tools, design tradeoffs made to improve usability, the various browser technologies powering the HUD, and how you can start hacking with a heads up display. | ||
| + | |||
| + | ==== Bio ==== | ||
| + | |||
| + | David Scrobonia is a part of the Security Engineering team at Segment working to secure modern web apps and AWS infrastructure. He contributes to open source in his spare time and is a core team member of the OWASP ZAP project. | ||
| + | |||
| + | |||
| + | === <span id="TALK_1400">Juice Shop: OWASP's most broken Flagship by Björn Kimminich</span> === | ||
| + | |||
| + | ==== Abstract ==== | ||
| + | |||
| + | OWASP Juice Shop is an intentionally insecure webapp for security trainings written entirely in Javascript which encompasses the entire OWASP Top Ten and many more severe security flaws. In this talk, you'll learn about this open-source project and its capabilities first-hand from its creator. Join a “happy shopper round trip,” enjoy a hacking demo of some of the built-in challenges, witness how to re-theme the Juice Shop into a security awareness booster for your own company, and learn how to set it up for a capture-the-flag (CTF) event in less than 5 minutes! | ||
| − | |||
| − | |||
| − | |||
====Bio==== | ====Bio==== | ||
| − | |||
| + | Björn Kimminich is responsible for global IT architecture and application security at Kuehne + Nagel. On the side, he gives IT security lectures at the non-profit private university Nordakademie. Björn also is the project leader of the OWASP Juice Shop and a board member for the German OWASP chapter. <br> | ||
| + | [[File:GitHub-Mark_no_background.png|25px|link=https://github.com/bkimminich|GitHub]] | ||
| + | [[File:TwitterLogo.png|25px|link=http://twitter.com/bkimminich|Twitter]] | ||
| + | [[File:LinkedinSquareLogo.png|25px|link=https://www.linkedin.com/in/bkimminich|LinkedIn]] | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | === <span id="TALK_1445">Leaky Processors: Stealing Your Secrets with Foreshadow by Jo Van Bulck</span> === | |
| − | + | ==== Abstract ==== | |
| − | + | For decades, memory isolation has been one of the key principles of | |
| − | + | secure system design. The recent wave of speculative execution attacks, | |
| + | including Meltdown, Spectre, and Foreshadow abruptly showed, however, | ||
| + | that performance optimizations in modern processors fundamentally | ||
| + | undermine application security.<br> | ||
| + | This talk will review how speculative execution attacks work. What makes | ||
| + | them dangerous, and why they require a paradigm shift in the way we | ||
| + | think about application security. The talk will have a special focus on | ||
| + | the recently disclosed Foreshadow CPU vulnerability, which led to a | ||
| + | complete collapse of state-of-the-art Intel SGX technology, and | ||
| + | necessitated hardware and software patches for all major operating | ||
| + | systems and virtual machine hypervisors. | ||
| − | + | ==== Bio ==== | |
| − | |||
| − | |||
| − | ====Bio==== | ||
| − | |||
| − | + | Jo Van Bulck is a PhD researcher at imec-DistriNet, KU Leuven, where he | |
| − | + | investigates hardware-level trusted computing from an integrated attack | |
| − | + | and defense perspective. His work resulted in a.o., the high-impact | |
| + | Foreshadow CPU vulnerability announced in August 2018, and several | ||
| + | open-source secure processor prototypes. | ||
| − | |||
| − | + | === <span id="TALK_1600">Fast forwarding Mobile Security with the MSTG by Jeroen Willemsen</span> === | |
| − | ==== | ||
| − | |||
| + | ==== Abstract ==== | ||
| − | + | After the startup of the mobile security project in 2010, the mobile security project and its testing guides have seen quiet some evolution. All of this changed quiet intensively when, in 2016, the Mobile Application Security Verification Standard (MASVS) and the Mobile Application Security Testing Guide (MSTG) were created. Now, two years fast forward: where are we now? How can you use it as a pentester or a developer? We will start with introducing the current state of the MSTG and its side-projects and then show various demos on iOS.<br> | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | ==== Bio ==== | ||
| − | + | Jeroen Willemsen is a Principal Security Architect at Xebia. With a love for mobile security, he recently became one of the projectleaders for the OMTG project (MASVS & MSTG). Jeroen is more or less a jack of all trades with interest in infrastructure security, risk management and application security. | |
| − | |||
| − | |||
| − | + | === <span id="TALK_1645">Lessons From The Legion (The OWASP BeNeLux Remix) by Nick Drage</span> === | |
| − | ==== | ||
| − | |||
| + | ==== Abstract ==== | ||
| − | + | Look at your job, your colleagues, your industry. Very smart people, working very hard... and yet it feels like we're losing.<br> | |
| − | + | <br> | |
| − | + | ''Why?''<br> | |
| + | <br> | ||
| + | Cyber security has always been a technology driven, engineer led industry - self-taught practitioners have chosen tactics and point solutions based on what fits in with their preferred ways of working and studying. We need better strategies to make use of those tactics. We can learn those strategies from other contexts and conflicts to improve our own methods and practices.<br> | ||
| + | <br> | ||
| + | ''Would you like to start winning?'' | ||
====Bio==== | ====Bio==== | ||
| − | |||
| + | Nick is the Director of Path Dependence Limited, and has over two decades of experience in the cyber security field… previously he was "SecOps” before the term was invented, as well as having been a SysAdmin, PCI QSA, pre-sales analyst, CHECK Team Leader, and various other less well defined roles. Nick is currently a Cyber Security Consultant and Penetration Tester, with occasional forays into being a Wargame Umpire, Adversarial Analyst, or Professional Wildcard. | ||
| + | |||
| + | === <span id="CyberWayFinder">Women in cybersecurity (CyberWayFinder)</span> === | ||
| + | OWASP BeNeLux and CyberWayFinder would like to invite you to a '''breakfast with other women in cybersecurity'''.<br> | ||
| + | Since women make up 7% of the cybersecurity work force, they are a rare breed, and don't often meet each other. That is why "women in cybersecurity breakfasts" are popping up in conferences around the world. | ||
| + | A small gathering with the women who will be present at our OWASP conference in the morning provides an excellent network opportunity to meet one another. We'll make sure you don't start out the day on an empty stomach, and provide you with some contacts, without missing out on the rest of the conference.<br> | ||
| + | join us as of 08h30 at Lamot conference center, and also hear about the CyberWayFinder training program which is being created to help women transition their career into cybersecurity.<br> | ||
<!-- Sixth tab --> | <!-- Sixth tab --> | ||
| − | = Social Event ( | + | = Social Event = |
| + | |||
| + | '''The Social Event is on Thursday, November 29th''' | ||
| + | |||
| + | The social event will be a unique opportunity to meet some of the trainers and speakers, as well the organisers or even peers.<br><br> | ||
| + | |||
| + | The social event will take place in restaurant [http://www.puro-mechelen.be/english Puro Mechelen], a couple of minutes from the conference center, on Thursday 29/11 at 19h00.<br><br> | ||
| + | There is a fixed group menu (meat or fish) for '''59€/person''', drinks included.<br><br> | ||
| + | Link to the [https://static1.squarespace.com/static/53bedc63e4b051fad94ee1f7/t/59b7d81ea803bbc8f65d85ee/1505220639318/Puro-groepsmenu.pdf Menus] (page 1), and the [https://static1.squarespace.com/static/53bedc63e4b051fad94ee1f7/t/54b57100e4b0ab0673e80e8d/1421177088856/drankenformules.doc.pdf drinks]. | ||
| + | <br> | ||
| − | + | '''Any participant pays individually. <br>Reservation via the form you'll receive after conference registration is mandatory.'''<br> | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | ''' | ||
| − | |||
| − | + | <!-- | |
| − | + | Address: TBD | |
| + | Menu:TBD | ||
| + | --> | ||
<!-- Seventh tab --> | <!-- Seventh tab --> | ||
| − | |||
= Sponsor = | = Sponsor = | ||
| − | + | ''' Become a sponsor of OWASP BeNeLux! ''' | |
There are 3 combined sponsorship packages (Gold, Silver or Bronze) that cover the BeNeLux chapter meetings 2019 and the BeNeLux OWASP Days 2018. | There are 3 combined sponsorship packages (Gold, Silver or Bronze) that cover the BeNeLux chapter meetings 2019 and the BeNeLux OWASP Days 2018. | ||
| − | Download our sponsor brochure | + | Download our [https://www.owasp.org/images/8/8e/OWASP_BeNeLux_2018_Sponsorship_Form_v20181004.pdf sponsor brochure] and contact [mailto:[email protected] us] for questions or sponsorship confirmation! |
Your sponsorship will be invested directly in the chapter meetings, supporting speaker and catering expenses. | Your sponsorship will be invested directly in the chapter meetings, supporting speaker and catering expenses. | ||
| Line 365: | Line 507: | ||
<!-- Don't remove these two lines! -->__NOTOC__ | <!-- Don't remove these two lines! -->__NOTOC__ | ||
<headertabs></headertabs> | <headertabs></headertabs> | ||
| − | |||
| − | |||
=== Made possible by our {{#switchtablink:Sponsor|Sponsors}}=== | === Made possible by our {{#switchtablink:Sponsor|Sponsors}}=== | ||
| − | |||
| + | ==== Gold ==== | ||
| − | + | [[File:DavinsiLabs.png|250px|link=https://www.davinsilabs.com]] | |
| + | [[File:Vest.jpg|250px|link=http://www.vest.nl]] | ||
| − | + | ==== Silver ==== | |
| + | [[File:LogoIngenicoGroup.png|250px|link=https://ingenico.be]] | ||
| + | [[File:LogoToreon.jpg|250px|link=https://www.toreon.com]] | ||
| + | [[File:LogoSynopsys.png|250px|link=https://www.synopsys.com]] | ||
| + | [[File:Nviso_logo_RGB_baseline_200px.png|250px|link=http://www.nviso.be]] | ||
| − | |||
| − | + | ==== Bronze ==== | |
| + | [[File:Logo_Informatiebeveiliging-200.png|250px|link=https://informatiebeveiliging.nl/]] | ||
[[Category:OWASP_AppSec_Conference]] | [[Category:OWASP_AppSec_Conference]] | ||
[[Category:OWASP_BeNeLux_Archives]] | [[Category:OWASP_BeNeLux_Archives]] | ||
Latest revision as of 13:42, 31 October 2019

Thanks to all speakers and trainers, sponsors and volunteers who could make this 2018 edition a success.
Sad you missed the conference? No problem, just have a look at the video recordings!
Save the date
In 2019 we will skip one year (we organised Global AppSec Amsterdam), See you next year in the Netherlands: 26 and 27 November 2020
Confirmed Conference Speakers
- David Scrobonia
- Niels Tanis
- Jeroen Willemsen
- Björn Kimminich
- Ralph Moonen
- Jo Van Bulck
- Lennert Wouters
- Nick Drage
Confirmed Trainers
- Andrew Martin
- David Scrobonia
- Jeroen Beckers - Stephanie Vanroelen
OWASP BeNeLux conference is free, but registration is required!
The conference is closed.
To support the OWASP organisation, consider to become a member, it's only US$50! Check out the Membership page to find out more.
The OWASP BeNeLux Program Committee
- Sebastien Deleersnyder / Lieven Desmet / David Mathy / Thomas Herlea / Stella Dineva / Adolfo Solero / Bart De Win, OWASP Belgium
- Martin Knobloch / Joren Poll / Edwin Gozeling, OWASP Netherlands
- OWASP Luxembourg
Tweet!
Event tag is #owaspbnl18
Donate to OWASP BeNeLux
Registration is closed
To support the OWASP organisation, consider to become a member, it's only US$50! Check out the Membership page to find out more.
Address
Training venueNovotel Mechelen Centrum Van Beethovenstraat 1 2800 Mechelen Belgium |
Conference venueCongres- en Erfgoedcentrum Lamot Van Beethovenstraat 8-10 2800 Mechelen Belgium |
Parking:
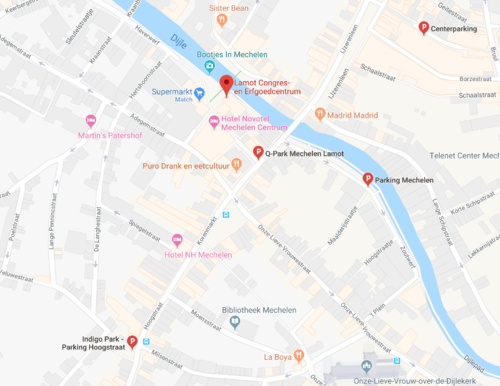
Find your parking on Google Maps
How to reach the venue?
Public transport
You can reach the Mechelen's train station from Antwerpen or Brussels. The Lamot conference center is 10 min away by bus (line 1).
Or you can choose to walk for 15 min (1.2 km).
By car
From Brussels:
Follow the E19 Brussels / Antwerpen and take the exit 10.
Follow the N1 until the R12 (take a left) and turn to the right at the "Brusselpoort" into the Hoogstraat to reach one of the parkings.
From Antwerpen:
Follow the E19 Brussels / Antwerpen and take the exit 9.
Follow the N16 until the R12 (take a right) and turn to the left at the "Brusselpoort" into the Hoogstraat to reach one of the parkings.
Hotels Nearby
Hotels around the Lamot conference center
Training Day is November 29th
Training Venue
The trainings will take place in the Novotel Mechelen Centrum hotel:
Van Beethovenstraat 1
2800 Mechelen
Google maps
Agenda
| Time | Description | Training 1 | Training 2 | Training 3 | |
|---|---|---|---|---|---|
| (Hof van Busleyden 1) | (Hof van Busleyden 2) | (Hof van Kamerijk) | |||
| 08h30 - 9h30 | Registration | ||||
| 09h30 - 11h00 | Training | Kubernetes security by Andrew Martin | OWASP Zap Training by David Scrobonia | Android security workshop by Jeroen Beckers & Stephanie Vanroelen | |
| 11h00 - 11h30 | Coffee Break | ||||
| 11h30 - 13h00 | Training | ||||
| 13h00 - 14h00 | Lunch | ||||
| 14h00 - 15h30 | Training | ||||
| 15h30 - 16h00 | Coffee Break | ||||
| 16h00 - 17h30 | Training | ||||
Choose the most appropriate training as they will be hosted at the same time.
Trainings
Training 1 - Kubernetes security by Andrew Martin
Abstract
Course Description
The course guides attendees through Linux container security in general, and progresses to advanced Kubernetes cluster security. It emphasises pragmatic threat modelling and risk assessment based on an understanding of the tools and primitives available, rather than dogmatic dos and don’ts.
Course Outline
- How to attack containerised workloads
- Enhanced container security
- How to attack Kubernetes
- Interactive production cluster hacking
- Hardening Kubernetes
- Locking down applications
- Security tooling and vendor landscape
Who Should Attend
This course is suitable for intermediate to advanced Kubernetes users who want to strengthen their security understanding. It is particularly beneficial for those operating Kubernetes in a high-compliance domain, or for established security professionals looking to update their skills for the cloud native world.
Participant requirements
Just a laptop with an SSH client please, ssh or PuTTY.
Bio
Andrew has a strong test-first engineering ethos gained architecting and deploying high-traffic web applications. Proficient in systems development, testing, and maintenance, he is comfortable profiling and securing every tier of a bare metal or cloud native application, and has battle-hardened experience delivering containerised solutions to enterprise clients. He is a co-founder at https://control-plane.io
Training 2 - OWASP Zap Training by David Scrobonia
Abstract
This hands on course will start with the basics of using ZAP attack proxy and finish with leveraging it's API to integrate ZAP within you CI/CD processes. Along the way we will be practicing techniques by attacking the OWASP JuiceShop, an intentionally vulnerable web application.
Audience
This couse is designed for both new and experienced users. No knowledge or experience with ZAP is required, but even those familiar with ZAP will learn something new.
Contents
- Basic Techniques & Manual Testing
- Advanced Techniques & Automated Testing
- Scripting with ZAP
- Using ZAP within your CI/CD Pipeline
Participant requirements
Please come prepared with the following tools installed:
If you have any trouble with the setup please feel free to reach out to davidscrobonia at gmail with questions.
Bio
David Scrobonia is a part of the Security Engineering team at Segment working to secure modern web apps and AWS infrastructure. He contributes to open source in his spare time and is a core team member of the OWASP ZAP project.
Training 3 - Android security workshop by Jeroen Beckers & Stephanie Vanroelen
Abstract
In this workshop, participants will come in contact with the basics of Android application security. Through hands-on exercises, Jeroen and Stephanie will show which mistakes can be made, both at the design and implementation level, that can compromise the security of both the application and the backend server. Although no real prior experience with Android is needed, some basic knowledge on programming is advised.
Participation requirements
- Basic linux / terminal knowledge
- Be able to understand the OWASP Top 10 (Not Mobile)
- Laptop with VirtualBox / VMWare (At least 8GB of RAM)
Bio
Jeroen Beckers is a security researcher at NVISO. He focusses mainly on
mobile applications for Android/iOS and sometimes even Windows Phone
(yes, some people actually use it!). Apart from breaking mobile
applications, he also gives security trainings and presentations at
conferences.
Stephanie Vanroelen is an IT security consultant currently focussing on Web and
Mobile Application Security. Her experiences in organizing IT Security
conferences such as BruCON and CyberSKool help her with project
management and communication skills. In her free time she pretends to be
Godzilla :).
Conference Day is November 30th
Agenda
| Time | Speaker | Topic | Media |
|---|---|---|---|
| 08h30 - 09h15 | Registration / Women in cybersecurity (CyberWayFinder) | ||
| 09h15 - 09h30 | Opening | ||
| 09h30 - 10h15 | Lennert Wouters | Fast, Furious and Insecure: Passive Keyless Entry and Start in Modern Supercars | |
| 10h15 - 11h00 | Ralph Moonen | Weaknesses in our voice communications network: from Blue Boxing to VoLTE | Slides |
| 11h00 - 11h30 | Morning Break | ||
| 11h30 - 12h15 | Niels Tanis | When Serverless Met Security… Serverless Security & Functions-as-a-Service (FaaS) | Slides |
| 12h15 - 13h00 | David Scrobonia | OWASP Zap | Slides |
| 13h00 - 14h00 | Lunch | ||
| 14h00 - 14h45 | Björn Kimminich | Juice Shop: OWASP's most broken Flagship | Slides |
| 14h45 - 15h30 | Jo Van Bulck | Leaky Processors: Stealing Your Secrets with Foreshadow | Slides |
| 15h30 - 16h00 | Afternoon Break | ||
| 16h00 - 16h45 | Jeroen Willemsen | Fast forwarding Mobile Security with the MSTG | Slides |
| 16h45 - 17h30 | Nick Drage | Lessons from the legion (The OWASP BeNeLux Remix) | Slides |
| 17h30 - 17h45 | Closing | ||
Talks
Fast, Furious and Insecure: Passive Keyless Entry and Start in Modern Supercars by Lennert Wouters
Abstract
The security of immobiliser and Remote Keyless Entry systems has been extensively studied over the past years. Passive Keyless Entry and Start systems, which are currently deployed in luxury vehicles, have not received as much attention.
During this presentation we will share the techniques used in reverse engineering the Tesla Model S Passive Keyless Entry and Start system. We will discuss multiple security weaknesses in the system including the use of an inadequate proprietary cipher using 40-bit keys, the lack of mutual authentication in the challenge-response protocol, hardware configuration mistakes and the absence of security partitioning.
We verified our findings by implementing a proof of concept attack allowing us to clone a Tesla Model S key fob in a matter of seconds with low cost commercial off the shelf equipment.
Finally, we will share our experience with the responsible disclosure of these finding to Tesla Motors and other likely affected manufacturers such as McLaren, Karma Automotive and Triumph Motorcycles as they all use the same system developed by Pektron.
Bio
Lennert Wouters is a PhD researcher at the Computer Security and Industrial Cryptography (COSIC) research group at KU Leuven. His research interests involve hardware security of connected embedded devices and side channel attacks.
Weaknesses in our voice communications network: from Blue Boxing to VoLTE by Ralph Moonen
Abstract
Voice over 4G, or VoLTE, brings back the phreaking 80's. Once again, after 3 decades, the signaling path of telephony is accessible to end users. No more R1, R2, C4 or C5 however: we now have SIP. As it turns out, the implementations of SIP and VoLTE in various European providers' 4G infrastructures, open up a host of possibilities. During our research over the past few years we have identified vulnerabilities in implementations such as txt message spoofing, subscriber enumeration, location determination (leakage of cell-ID and LAC), IMEI leakage and a potential SIM-card sharing attack.
During this talk we will begin with a little historic stroll of phone phreaking through notable events and discoveries over the years. Bridging the narrative over the last few decades, new technologies such as VoIP, Volte, and VoWiFi are introduced, explaining the 4G and VoLTE infrastructure components and protocols. Next, on a rooted Android phone, we will show what control the user has over the VoLTE stack using some standard tools and the IPv6 stack. This includes hidden activities in Android and extraction of IPsec keys from the VoLTE stack. We will show that it is possible to import keys to Wireshark and monitor the IPv6 SIP traffic and components. Finally, examples of the vulnerabilities in implementations such as txt message spoofing, subscriber enumeration, location determination (leakage of cell-ID and LAC), IMEI leakage and a potential SIM-card sharing attack will be explained.
Yes, a slightly technical nugget of knowledge, yet very accessible and a lot of fun!
Importance of presentation for involved audience
The phone systems of the world have always been of interest to everyone: from users who expect privacy, to intelligence agencies who want access. The privacy, integrity and confidentiality of voice communications over telecommunication networks is therefore of interest to anyone who uses mobile phones (i.e.: everyone). It is also typically a closed subject with very little research being done, relative to other security topics such as malware and application vulnerabilities. The combination of little research and high impact on everyone, makes that this topic deserves much more attention than it currently does. The VoLTE weaknesses we will describe are implementation dependent, and largely unpublished (i.e. new).
Bio
Ralph Moonen CISSP is Technical Director at Secura. Ralph is an old-school ethical hacker with 3 decades of experience as penetration tester, IT-auditor and security consultant. Now, as Technical Director, he is responsible for topics such as R&D and technical projects at Secura.
When Serverless Met Security… Serverless Security & Functions-as-a-Service (FaaS) by Niels Tanis
Abstract
Serverless is a design pattern for writing scalable applications in which Functions as a Service (FaaS) is one of the key building blocks. Every mayor Cloud Provider has got his own FaaS available. On Microsoft Azure there is Azure Functions, AWS has got Lambda and Cloud Functions can be used on the Google Cloud. All of these have a lot of similarities in the way they allow developers to create small event driven services.
From security perspective there are a lot of benefits when moving to a serverless architecture. There is no need to manage any of the machines and the underlying infrastructure. Dealing with updates, patches and infrastructure is the responsibility of the platform provider. FaaS are short lived processes which will be instantiated and destroyed in a matter of milliseconds making it more resilient to denial-of-services (DoS) and also makes it harder to attack and compromise.
But will all of this be sufficient to be ’secure’ or should we be worried about more? With serverless there is still a piece of software that will be developed, build, deployed and executed. It will also introduce a more complex architecture with corresponding attack surface which also makes it hard to monitor. What about the software supply chain and delivery pipeline? There still will be a need to patch your software for vulnerabilities in code and used 3rd party libraries. In this talk we will identify the security area’s we do need to focus on when developing serverless and define possible solutions for dealing with those problems.
Bio
Niels Tanis has got a background in .NET development, pentesting and security consultancy. He also holds the CSSLP certification and has been involved in breaking, defending and building secure applications. He joined Veracode in 2015 and right now he works as a security researcher on a variant of languages and technologies related to Veracode’s Binary Static Analysis service. He is married, father of 2 and lives in a small village just outside Amersfoort, The Netherlands.
OWASP Zap by David Scrobonia
Abstract
Intoducing security testing tools to a QA or developers workflow can be difficult when the tools aren't easy or intuitive to use. Even for security professionals, the friction of cumbersome security tooling can prevent them from getting the most from a tool or being effective with their time.
The OWASP ZAP team is working to help enable developers, QA, and hackers alike with the ZAP Heads Up Display, a more user friendly way to engage with the security testing tool. The Heads Up Displays integrates ZAP directly in the browser providing all of the funcitonality of the tool via a heads up display. The goal is to make ZAP more accessible and enabling users, especially developers, to integrate security in their daily workflows.
This talk will discuss the importance of usable tools, design tradeoffs made to improve usability, the various browser technologies powering the HUD, and how you can start hacking with a heads up display.
Bio
David Scrobonia is a part of the Security Engineering team at Segment working to secure modern web apps and AWS infrastructure. He contributes to open source in his spare time and is a core team member of the OWASP ZAP project.
Juice Shop: OWASP's most broken Flagship by Björn Kimminich
Abstract
OWASP Juice Shop is an intentionally insecure webapp for security trainings written entirely in Javascript which encompasses the entire OWASP Top Ten and many more severe security flaws. In this talk, you'll learn about this open-source project and its capabilities first-hand from its creator. Join a “happy shopper round trip,” enjoy a hacking demo of some of the built-in challenges, witness how to re-theme the Juice Shop into a security awareness booster for your own company, and learn how to set it up for a capture-the-flag (CTF) event in less than 5 minutes!
Bio
Björn Kimminich is responsible for global IT architecture and application security at Kuehne + Nagel. On the side, he gives IT security lectures at the non-profit private university Nordakademie. Björn also is the project leader of the OWASP Juice Shop and a board member for the German OWASP chapter.
![]()
![]()
![]()
Leaky Processors: Stealing Your Secrets with Foreshadow by Jo Van Bulck
Abstract
For decades, memory isolation has been one of the key principles of
secure system design. The recent wave of speculative execution attacks,
including Meltdown, Spectre, and Foreshadow abruptly showed, however,
that performance optimizations in modern processors fundamentally
undermine application security.
This talk will review how speculative execution attacks work. What makes
them dangerous, and why they require a paradigm shift in the way we
think about application security. The talk will have a special focus on
the recently disclosed Foreshadow CPU vulnerability, which led to a
complete collapse of state-of-the-art Intel SGX technology, and
necessitated hardware and software patches for all major operating
systems and virtual machine hypervisors.
Bio
Jo Van Bulck is a PhD researcher at imec-DistriNet, KU Leuven, where he investigates hardware-level trusted computing from an integrated attack and defense perspective. His work resulted in a.o., the high-impact Foreshadow CPU vulnerability announced in August 2018, and several open-source secure processor prototypes.
Fast forwarding Mobile Security with the MSTG by Jeroen Willemsen
Abstract
After the startup of the mobile security project in 2010, the mobile security project and its testing guides have seen quiet some evolution. All of this changed quiet intensively when, in 2016, the Mobile Application Security Verification Standard (MASVS) and the Mobile Application Security Testing Guide (MSTG) were created. Now, two years fast forward: where are we now? How can you use it as a pentester or a developer? We will start with introducing the current state of the MSTG and its side-projects and then show various demos on iOS.
Bio
Jeroen Willemsen is a Principal Security Architect at Xebia. With a love for mobile security, he recently became one of the projectleaders for the OMTG project (MASVS & MSTG). Jeroen is more or less a jack of all trades with interest in infrastructure security, risk management and application security.
Lessons From The Legion (The OWASP BeNeLux Remix) by Nick Drage
Abstract
Look at your job, your colleagues, your industry. Very smart people, working very hard... and yet it feels like we're losing.
Why?
Cyber security has always been a technology driven, engineer led industry - self-taught practitioners have chosen tactics and point solutions based on what fits in with their preferred ways of working and studying. We need better strategies to make use of those tactics. We can learn those strategies from other contexts and conflicts to improve our own methods and practices.
Would you like to start winning?
Bio
Nick is the Director of Path Dependence Limited, and has over two decades of experience in the cyber security field… previously he was "SecOps” before the term was invented, as well as having been a SysAdmin, PCI QSA, pre-sales analyst, CHECK Team Leader, and various other less well defined roles. Nick is currently a Cyber Security Consultant and Penetration Tester, with occasional forays into being a Wargame Umpire, Adversarial Analyst, or Professional Wildcard.
Women in cybersecurity (CyberWayFinder)
OWASP BeNeLux and CyberWayFinder would like to invite you to a breakfast with other women in cybersecurity.
Since women make up 7% of the cybersecurity work force, they are a rare breed, and don't often meet each other. That is why "women in cybersecurity breakfasts" are popping up in conferences around the world.
A small gathering with the women who will be present at our OWASP conference in the morning provides an excellent network opportunity to meet one another. We'll make sure you don't start out the day on an empty stomach, and provide you with some contacts, without missing out on the rest of the conference.
join us as of 08h30 at Lamot conference center, and also hear about the CyberWayFinder training program which is being created to help women transition their career into cybersecurity.
The Social Event is on Thursday, November 29th
The social event will be a unique opportunity to meet some of the trainers and speakers, as well the organisers or even peers.
The social event will take place in restaurant Puro Mechelen, a couple of minutes from the conference center, on Thursday 29/11 at 19h00.
There is a fixed group menu (meat or fish) for 59€/person, drinks included.
Link to the Menus (page 1), and the drinks.
Any participant pays individually.
Reservation via the form you'll receive after conference registration is mandatory.
Become a sponsor of OWASP BeNeLux!
There are 3 combined sponsorship packages (Gold, Silver or Bronze) that cover the BeNeLux chapter meetings 2019 and the BeNeLux OWASP Days 2018.
Download our sponsor brochure and contact us for questions or sponsorship confirmation!
Your sponsorship will be invested directly in the chapter meetings, supporting speaker and catering expenses.
The sponsorship will also be dedicated to cover the costs of the OWASP 2018 BeNeLux event.
Made possible by our Sponsors
Gold
Silver







