This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Code Review and Static Analysis with tools
Chapter: OWASP NoVA >> Knowledge
Static Analysis Curriculum
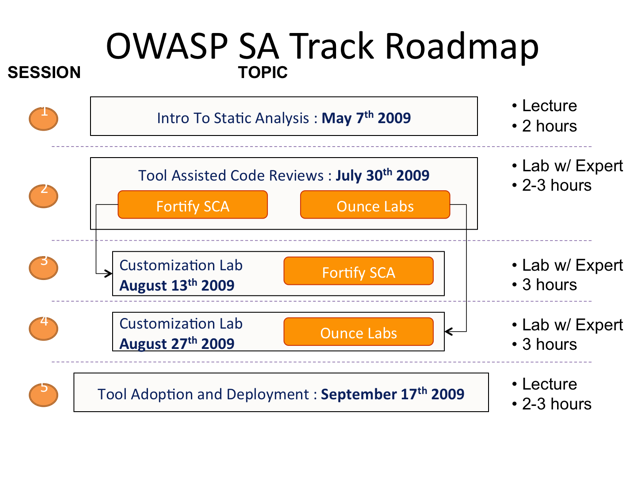
- For an introduction to the OWASP Static Analysis (SA) Track goals, objectives, and session roadmap, please see this presentation.
The following is the agenda of the OWASP Static Analysis track roadmap.
Code Review and Static Analysis with tools
- What: Secure Code Review
- Who: Performed by Security Analysts
- Where it fits: BSIMM Secure Code Review
- Cost: Scales with depth, threat facing application, and application size/complexity
This article will answer the following questions about secure code review and use of static analysis tools:
- What are static analysis tools and how do I use them?
- How do I select a static analysis tool?
- How do I customize a static analysis tool?
- How do I scale my assessment practices with secure code review?
Organizational
How do I scale my assessment practices with secure code review?
Implementing a static analysis tool goes a long way to providing a force multiplier for organizations. The following presentation discusses a comprehensive set of steps organizations can undertake to successfully adopt such tools. The presentation discusses who should adopt the tool, what steps they should take, who they should involve, and how long/much it will cost.
Implementing a Static Analysis Tool.ppt
For those with existing assessment practices involving secure code review (whether or not those practices leverage tools) the question often becomes, "I can review an application, but how do I scale the practice to my entire organization without astronomic cost?" The following presentation addresses this question:
Maturing Assessment Through Static Analysis
Customization
People who believe that the value of static analysis is predominantly within their core capabilities "out of the box" come up incredibly short. By customizing your chosen tool you can expect:
- Dramatically better accuracy (increased true positives, decreased false positives, and decreased false negatives)
- Automated scanning for corporate security standards
- Automated scanning for an organization's top problems
- Visibility into adherence to (or inclusion of) sanctioned toolkits
The following presentation was given at the NoVA chapter in '06 and discusses deployment and customization:
Warning: this presentation is old and gives examples using the now defunct "CodeAssure" from what was then SecureSoftware.