This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
The Owasp Orizon Framework
Introduction
A lot of open source projects exist in the wild performing static code review analysis. This is good, it means that source code testing for security issues is becoming a constraint.
Such tools bring a lot of valuable points:
- community support
- source code freely available to anyone
- costs
On the other side, these tools don't share the most valuable point among them: the security knowledge. All these tools have their own security library with a lot of checks contained into without sharing such knowledge.
In 2006 Owasp Orizon project is born to provide a common underlying layer to all opensource projects concern static analysis.
Orizon project includes:
- a set of APIs that developers can use to build their own security tool performing static analysis
- a security library with checks to apply to source code
- a tool, Milk, able to static analyze a source code using Orizon Framework.
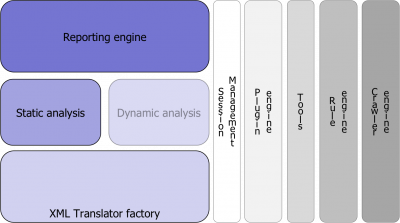
The Owasp Orizon Architecture
In the following picture, the Owasp Orizon version 1.0 architecture is shown. As you may see, the framework is organized in engines that perform tasks over the source code and a block of tools that are deployed out of the box in order to use the APIs in a real world static analysis.
With all such elements, a developer can be scared to use the framework, that's why a special entity called SkyLine was created. Before going further into SkyLine analysis, it's very important to understand all the elements Orizon is made of.
The first
foo