This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Projects/OWASP Mobile Security Project - Top Ten Mobile Risks
From OWASP
Revision as of 06:40, 30 January 2014 by Jason Haddix (talk | contribs)
About this list
In 2013 we polled the industry for new vulnerability statistics in the field of mobile applications. What you see here is a result of that data and a representation of the mobile application threat landscape.
Our road-map for 2014 includes:
- More updates to the wiki content; including cross-linking to testing guides, more visual exercises, etc.
- A PDF release.
This list is still a work in progress. We are small group doing this work and could use more help! If you are interested, please contact one of the project leads.
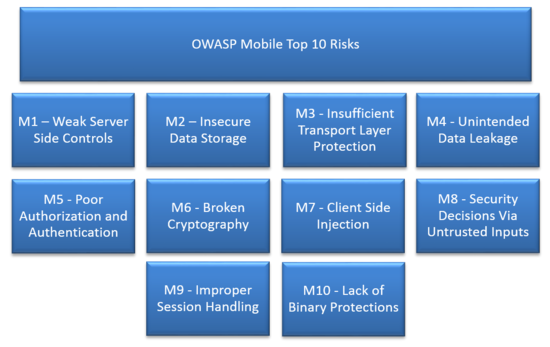
Top 10 Mobile Risks - Re-Release Candidate 2014 v1.0
- M1: Weak Server Side Controls
- M2: Insecure Data Storage
- M3: Insufficient Transport Layer Protection
- M4: Unintended Data Leakage
- M5: Poor Authorization and Authentication
- M6: Broken Cryptography
- M7: Client Side Injection
- M8: Security Decisions Via Untrusted Inputs
- M9: Improper Session Handling
- M10: Lack of Binary Protections
Additional Information
- We adhered loosely to the OWASP Web Top Ten Project methodology.
- The list below is the OLD release candidate v1.0 of the OWASP Top 10 Mobile Risks. This list was initially released on September 23, 2011 at Appsec USA.
- The original presentation can be found here: SLIDES
- The corresponding video can be found here: VIDEO
- 2011-12 Mobile Top Ten for archive purposes
- The original presentation can be found here: SLIDES