This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
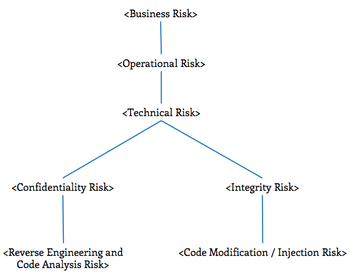
Technical Risks of Reverse Engineering and Unauthorized Code Modification
Introduction
With the recent move towards mobile applications, an adversary can now see, touch, and directly modify a lot of the application’s presentation and business layer code within the mobile computing environment. This capability allows the adversary to realize the same traditional business threats as before (with web applications) but in genuinely new and unconventional ways.
Attackers now leverage reverse-engineering and tampering attack techniques to realize the following pervasive threats on the mobile platform:
- Spoofing: interception of other users’ authentication credentials and using said credentials to conduct transactions on the victim’s behalf;
- Code modification: changing critical business logic, control flow, and program operations; disable or circumvent security controls to bypass authentication, encryption, license management / checking, digital rights management or root / jailbreak detection;
- Information Disclosure: lifting or intercepting digital keys, certificates, credentials, metadata, proprietary algorithms, other application internal logic; and
- Elevation of Privilege: Propagating unauthorized distribution of code; insertion of malware or exploits in the application and repackaging.
These unique threats are sponsoring evolution from web application security techniques to new mobile application security approaches.
Traditional secure coding techniques that were relevant to preventing attacks through web application security controls are completely irrelevant to preventing reverse-engineering and tampering attacks. Even if an organization produces ‘perfect’ code that employs secure coding techniques at all times, the organization cannot apply these same techniques to prevent an adver¬¬sary from applying reverse engineering techniques on an application that physically resides within the adversary’s phone. The compiled mobile application code, no matter how unreadable to human eyes, is reversible and modifiable by an adversary using many easily accessible reverse engineering tools.
The primary focus of this note is to address native or hybrid mobile applications and client-side binary-level attacks (i.e., adversary has the mobile application binary that she seeks to compromise). The rest of this document describes technical and business risks that may result from reverse engineering or integrity violation of applications.
Relevant Risks
|