This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
OWASP Anti-Malware - Knowledge Base
Introduction
A Technical Knowledge Base for Banking Malware Threats
Protecting Banking Resources
Are your resources protected?
Enumerate the interesting targets
Define the path to the targets (Transition graphs)
Apply trust boundaries (security measures)
Define the weaknesses of the security measures adopted
Appendix A: Security Considerations about Authentication Solutions and Malware
Actually Banking Malware families can bypass the vast majority of the world most secure authentication. How? The answer is simple: by tailoring an appropriate attack on the specific authentication schema with a bit of social engineering. Malware Authors know that the weakest link most of the times is the user himself.
For more information:
- http://www.slideshare.net/marco_morana/owasp-app-seceu2011version1
- http://www.slideshare.net/guestb1956e/csi2008-gunter-ollmann-maninthebrowser-presentation
- https://www.owasp.org/images/e/e4/AppsecEU09_The_Bank_in_The_Browser_Presentation_v1.1.pdf
TextField Static Password
Risk Evaluation:
Vulnerable to vast majority of all Banking Malware families in their default configuration
Description
A password is a secret word or string of characters that is used for authentication, and is the world most used and simplest way of authenticating a user to a computer. “Static” means that Password does not change over time, unless manually updated. Textbox input field is the HTML element were password is inserted and this element is compatible with HID (Human Input Devices) such as hardware keyboards and Virtual Keyboards.
How gets defeated
Almost All banking malware can automatically log passwords using two components: Keylogging and Form Grabbing. A software Keylogger component can use a number of very different techniques, because operative systems offer many different ways to know which key is pressing a user. Even if this component seems very powerful, it has the disadvantage of not logging the Clipboard. Users may copy and paste passwords for simplicity or security reasons: many password wallets suggest to use this approach (e.g. KeePassX ). For this reason Banking Malware Authors prefer to log web based credentials using form grabbing components instead of keyloggers: from Wikipedia “this method intercepts the on submit API in browsers and collects web form data before it passes over the internet.”. Since FormGrabbing is actually used by any major Banking Malware Family (e.g. Zeus, Spyeye, IceIX etc.) “text field” static password does not represent a secure way of authentication. In addition Malware families can automatically log any password field without using any particular configuration.
External References:
Javascript Keyboard
Risk Evaluation:
Vulnerable to vast majority of all Banking Malware families with a minimal configuration of the malicious agent. This solution alone does not give a substantial improvement in terms of security comparing it to the Password TextBox input, however attacker takes more time in analyzing puzzled screen-shot passwords so it's a valid approach in terms of defense in depth.
Description
Javascript Keyboard was introduced more than a decade ago in response to Keylogging and Form Grabbing techniques used by Trojan Stealers. Javascript Keyboard works by creating a virtual keyboard on the screen with a dynamic layout; the random disposition of the keys represent a sort of "turing test" that could be understood by human users but not by malicious software agents.
How gets defeated
Back in year 2002, after a couple of years, Malware Authors realized that they could visually grab images of the clicked key pressed (click area grabbing) or to video record the sequence of key pressed. "Click Grabbing" feature was born and with a minimal configuration was possible to defeat javascript password in a standard and efficient way. This kind of attack simply stores the information remotely for a subsequent interpretation by a human attacker.
External References:
From Fortiguard (Zeus trojan defeats a Virtual Javascript Keypad)
Behavior Based Authentication
TAN (Gridcard, Scratch Card)
OTP (Time Based, Click Based)
CAP (Random Nonce, Challenge Response)
SMS Challenges
MSISDN (Caller-ID Authentication)
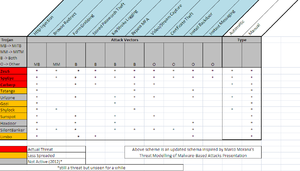
Appendix B: Banking Malware Families (Active in 2012)
Taken as inspiration from Marco Morana's Presentation and from other sources (e.g. slides 26-30 The Bank in the Browser Presentation - G. Fedon ), here is a quick summary of Banking Malware features updated as of 2012.
Schema summarizes every banking trojan by giving the following informations:
- Attack Capabilities
- Type
Attack Capabilites describes the features of the involved trojan, and immediately below the technique used to implement the given feature.
- HTTP Injection
- Browse Redirect
- Form Grabbing
- Credential Theft
- Keystroke Logging
- Bypass MFA
- ScreenCapture / VideoCapture
- Certificate Theft
- Install Backdoor
- Instant Message
Type field describes what kind how the malware operates:
- Automatic
- Manual
Spyeye
SpyEye is considered the successor of ZeuS and globally considered as the most advanced Banking Malware kit actually used.
This kit was conceived as botnet easy to manage via a web based control panel.
SpyEye relies upon MiTB ( Man in The Browser ) attacks to accomplish its task, it provides a custom Encrypted Configuration File where there are:
- Plugins
- Web Injection Code
- Collectors List- where stolen data is sent
SpyEye is capable of HTML code injection in the following browsers:
- FireFox
- Internet Explorer
- Chrome
- Opera
List of commonly used Plugins:
- ccgrabber - used to collect Credit Card numbers by analyzing POST requests.
- ffcertgrabber - used to steal Firefox stored Certificates.
- ftpbc - used to reverse ftp connections to the bot.
- socks5 - allows reverse connections via a proxy server.
- billinghammer - charges Credit Cards by using stolen card data.
- ddos - plugin used to ddos a specified target.
- bugreport - send crash reports to the bot master.
- SpySpread - capability to spread via USB, IM Messages
- rdp - Remote Desktop capability
SpyEye kit, actually reached version 1.3.48
In the second half of 2011 appeared a mobile edition of SpyEye, called SpitMo specifically designed to steal mTAN (mobile TAN) authentication systems. SpitMo
Recently (Jenuary 2012) appeared a SpyEye Campaign able to Hide its Fraud Footprint also called Post-Transaction Attack
Resources:
- A Guide to SpyEye C&C Messages
- New SpyEye Gains Zeus Features – A Detailed Analysis of SpyEye Trojan v1.3
- DDOS plugin for SpyEye
- SpyEye steals your data. Even in a limited account
- The SpyEye Interface, Part 1: CN 1
- The SpyEye Interface Part 2: SYN 1
- SpyEye 1.3.4.x Comes with Noteworthy Modifications (Part 1)
- SpyEye 1.3.4.x Comes with Noteworthy Modifications (Part 2)
Tracking SpyEye:
Zeus
ZeuS is a Banking Trojan identified for the first time in 2007, designed as HTTP Based Botnet specifically crafted to steal Online Banking Credentials.
Despite the fact that ZeuS Kit is no longer developed, infection statistics that can be checked here ZeuS Statistics clearly demonstrates that this Trojan has a remarkable diffusion.
The ZeuS Kit functionality is based on MiTB attacks, an encrypted configuration file contains URL Triggers and HTML Code to be Injected.
In the past year appeared also a ZeuS for mobile called ZitMo, developed to bypass mTAN authentication system, more information can be reached here:
- The ZitMo Trojan Bypasses Online Banking Security
- Zitmo Trojan for Android defeats two-factor authentication
2011 was also the year of ZeuS Source Code leak, this essentially lead to a number of new ZeuS Variants, here the most significant:
- ICE IX
- ZeuS P2P Edition
The most interesting variant is the P2P one, where ZeuS gained P2P Botnet and DGA (Domain Generation Algorithm) capabilities, that make ZeuS able to interact with other victims (nodes) and get Updated Binaries and Configurations.
ZeuS P2P References:
- ZeuS Gets More Sophisticated Using P2P Techniques
- ZeuS – P2P+DGA variant – mapping out and understanding the threat
Other References:
- ZeuS Tracker
- Ice IX – Or Just ZeuS?
- JaZeus: when Zeus meets Java
- Zeus Malware Analysis by SophosLabs
- ZeuS Banking Trojan Report
- Abstract Memory Analysis: Zeus Encryption Keys
Tracking ZeuS:
Carberp
After ZeuS and SpyEye the third advanced Malware Banking Trojan is Carberp, that during its evolution reached a great level of complexity, by mixing good bypassing and stealth countermeasures with ability to steal via Browser Code Injection online Banking Credentials.
Synthesis of Carberp Functionalities [1]:
- Ability to run as non-administrator
- Ability to infect Windows XP , Windows Vista and Windows 7
- Will not make any changes to the registry (only in memory modifications)
- Browser Hooking
- Stolen data is transmitted in real-time to C&C server
- Kill AntiVirus Software
- Screenshot Ability
- Form Grabber
- Backconnect
Carberp makes use of encrypted Configuration Files that contains plugins and web injection code
- miniav.psd - Kill Competitors Botnets (SpyEye. ZeuS)
- vnc.psd - Remote VNC Session Capability
- passw.psd - password grabber for FTP, VNC, E-Mail Clients, Stored Browser Passwords
References:
- www.malwareint.com/docs/inside-carberp-botnet-en.pdf
- Carberp + BlackHole growing fraud incidents
- Bootkit Evolution of Win32Carberp: going deeper
- Decrypting Carberp C&C communication
- Facebook New Trends in Carberp Activity
Tatanga
Tatanga appeared in the first half of 2011 as MiTB based trojan designed to steal Online Banking Credentials and spoof (Post Transaction Attack) the real balance of the victim.
Like previously seen trojans, also Tatanga makes use of Encrypted Configuration Files (3-DES) to store plugins and web injection code.
Additionally Tatanga is able to:
- Grab E-Mail addresses
- Remove Competitors Botnets
- File Infector to increase malware spread
- Kill Antivirus Software
References:
Urlzone
Urlzone is a Banking Trojan appeared in 2009, its main feature is the ability to hide the evidence of the fraud by changing on fly the balance showed to the Victim.
To accomplish money stealing Urlzone uses a classical MiTB Approach, it works on the following browsers
- FireFox
- Internet Explorer 6,7,8
- Opera
References:
- Finjan CyberIntel Report September 2009
- Banking Trojan steals money from under your nose
- The case of the fake money-mules: Inside the URLZone Trojan network
- RSA banking Trojan research underscores problem tracking cybercriminals
Gozi
Banking trojan Gozi appeared for the first time in 2007 and was characterized by a Low Detection Rate and ability to Steal from SSL Encrypted Sessions.
Features List:
- Steals SSL Data
- Steals Static Information from Banking Website
- Steals Dynamic Password Schemes like Two Factor Authentication and OTP
- KeyLogging Capabilities
- SSL Encrypted Communication with the C&C Server
- AntiVirus Bypassing Capabilities
SSL Stealing Technique is described here Gozi Trojan Steals SSL Encrypted Data for Fun and Profit
References:
Shylock
Shylock is a new Financial Malware, publicly reported for the first time on 7 September 2011. Main ability of this malware is to inject itself inside explorer's code. Also it incorporates watchdog that prevents removing and rootkit functionality to hide itself.
Features List:
- Gathering system information on compromised system and sends it to dropzone
- Downloading configuration that will be used from defined domain
- Injects malicious code into browser's code
- Hides using rootkit functionality
- Intercepts network traffic and attempts to add malicious code to network trafic
References:
Sunspot
Sunspot appeared for the first time in late 2011 as MiTB based trojan designed to steal Online Banking Credentials.
Features:
- Browser Code Injection
- KeyStroke Logger
- Screenshotting Capabilities
- Steals Sensitive Personal Information necessary to carry out User Impersonation Attacks
- Good AntiVirus Bypassing Capabilities
Sunspot works on 32bit and 64bit Systems from Windows XP to Windows 7.
References:
Oddjob
Oddjob Financial Trojan has been publicly reported for the first time 22 February 2011, the peculiar characteristic of Oddjob is the ability to keep open Victim's Session even after they Logout, this implies that Criminals will be able to steal money by Impersonating the Victim by tapping the Session ID.
Oddjob works by injecting malicious code into Internet Explorer and Firefox browsers, the code is contained in custom configuration files.
Will follow a quick summary of the Trojan Functionalities:
- Intercepts GET and POST requests
- HTML Code Injection via MiTB Approach
- Session Hijacking
Session hijacking is performed by changing Logout functionality via malicious html/js injected code, victim will inadvertently keep session open and fraudsters will commit the money transaction.
References:
Ramnit
Ramnit is a prolific malware that show a wide range of morphings during its arc of existence, between these variations there is also the Financial Stealing one.
Ramnit is essentially a Backdoor Trojan with the ability to perform also MiTB Attacks.
List of Features:
- MiTB Capabilities
- Backdoor Capabilities
- File Infector Office Files, Windows Executables
- SSL Secured C&C Communication
- AntiVirus bypassing Capabilities
- Cookie Grabber
References: