This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
OWASP Zed Attack Proxy Project
| This project is part of the OWASP Builders community. Feel free to browse other projects within the Defenders, Builders, and Breakers communities. |
| This project is part of the OWASP Breakers community. Feel free to browse other projects within the Defenders, Builders, and Breakers communities. |
Main
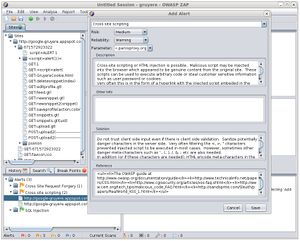
The Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications.
It is designed to be used by people with a wide range of security experience and as such is ideal for developers and functional testers who are new to penetration testing.
ZAP provides automated scanners as well as a set of tools that allow you to find security vulnerabilities manually.
The current version of ZAP is 1.3.0.
<paypal>Zed Attack Proxy</paypal>
Some of ZAP's features:
- Intercepting Proxy
- Automated scanner
- Passive scanner
- Brute Force scanner
- Spider
- Fuzzer
- Port scanner
- Dynamic SSL certificates
- API
- Beanshell integration
Some of ZAP's characteristics:
- Easy to install (just requires java 1.6)
- Ease of use a priority
- Comprehensive help pages
- Fully internationalized
- Under active development
- Open source
- Free (no paid for 'Pro' version)
- Cross platform
- Involvement actively encouraged
It supports the following languages:
- English
- Brazilian Portuguese
- Chinese
- French
- Danish
- German
- Greek
- Indonesian
- Japanese
- Polish
- Spanish
ZAP is a fork of the well regarded Paros Proxy.
Roadmap
Details of previous releases can be found here
Release 1.3.0
Version 1.3.0 has just been released, and adds the following main features:
- Fuzzing (using components from JBroFuzz)
- Dynamic SSL Certificates
- Daemon mode and API to allow other tools to interact with ZAP
- BeanShell integration
- Full internationalization
- Out of the box support for 10 languages
Future Releases
Future releases are likely to include:
- Further improvements to the passive and active automated scanners
- Further improvements the Spider
- Fuzzing analysis
- API extensions
Get Involved
Involvement in the development of ZAP is actively encouraged!
You do not have to be a security expert in order to contribute.
Some of the ways you can help:
Feature Requests
Please raise new feature requests as enhancement requests here: http://code.google.com/p/zaproxy/issues/list
If there are existing requests you are also interested in then please 'star' them - that way we can see which features people are most interested in and can prioritize them accordingly.
Feedback
Please use the zaproxy-develop Google Group for feadback:
- What do like?
- What dont you like?
- What features could be made easier to use?
- How could the help pages be improved?
Log issues
Have you had a problem using ZAP?
If so and its not already been logged then please report it
Localization
Are you fluent in another language? Can you help translate ZAP into that language?
If so then please get in touch.
Development
If you fancy having a go at adding functionality to ZAP then please get in touch via the zaproxy-develop Google Group.
Again, you do not have to be a security expect to contribute code - working on ZAP could be great way to learn more about web application security!
If you actively contribute to ZAP then you will be invited to join the project.
Project About
|
For more details about ZAP see the new ZAP website at zaproxy.org
|
Quick DownloadDonate to ZAPNews and EventsPlease see the News and Talks tabs Change LogCode RepoEmail ListQuestions? Please ask on the ZAP User Group Project LeaderProject Leader Co-Project Leaders Related ProjectsOpen Hub StatsClassifications
| ||||||||