This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Summit 2011 Working Sessions/Session073"
(me too) |
|||
| Line 17: | Line 17: | ||
| summit_session_attendee_notes,_reason_for_participating_and_issues_to_be discussed3= see items at [[Talk:Summit_2011_Working_Sessions/Session023#Emphasise_.22S.22_of_OWASP | Overhauling OWASP website]] session | | summit_session_attendee_notes,_reason_for_participating_and_issues_to_be discussed3= see items at [[Talk:Summit_2011_Working_Sessions/Session023#Emphasise_.22S.22_of_OWASP | Overhauling OWASP website]] session | ||
| − | | summit_session_attendee_name4 = | + | | summit_session_attendee_name4 = Elke Roth-Mandutz |
| − | | summit_session_attendee_email4 = | + | | summit_session_attendee_email4 = [email protected] |
| − | | summit_session_attendee_company4= | + | | summit_session_attendee_company4= GSO-University of Applied Sciences |
| − | | summit_session_attendee_notes,_reason_for_participating_and_issues_to_be discussed4= | + | | summit_session_attendee_notes,_reason_for_participating_and_issues_to_be discussed4= web privacy research project |
| summit_session_attendee_name5 = | | summit_session_attendee_name5 = | ||
Revision as of 18:10, 11 January 2011
Global Summit 2011 Home Page
Global Summit 2011 Tracks
| Please see/use the 'discussion' page for more details about this Working Session | ||||||
|---|---|---|---|---|---|---|
| Working Sessions Operational Rules - Please see here the general frame of rules. |
| WORKING SESSION IDENTIFICATION | ||||||
|---|---|---|---|---|---|---|
| Short Work Session Description | 
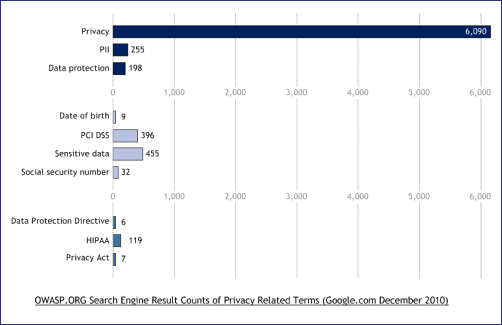
Privacy is a growing area of concern in the US, and might have greater awareness & understanding in the EU than security. Should OWASP say more about protecting personal data? Security is just one aspect of data protection, but many data breaches have been the result of application vulnerabilities. This session will be useful for project leaders, as well as anyone in sectors collecting, processing or storing personal data (e.g. of consumers, citizens and employees). | |||||
| Related Projects (if any) |
| |||||
| Email Contacts & Roles | Chair Colin Watson @ |
Operational Manager |
Mailing list {{{mailing_list}}} | |||
| WORKING SESSION SPECIFICS | ||||||
|---|---|---|---|---|---|---|
| Objectives |
| |||||
| Venue/Date&Time/Model | Venue/Room OWASP Global Summit Portugal 2011 |
Date & Time
|
Discussion Model participants and attendees | |||
| |
|---|
| WORKING SESSION OPERATIONAL RESOURCES | ||||||
|---|---|---|---|---|---|---|
| Projector, whiteboards, markers, Internet connectivity, power | ||||||
| |
|---|
| WORKING SESSION ADDITIONAL DETAILS | ||||||
|---|---|---|---|---|---|---|
The protection of personal data has been an important concern of organisations, especuially in Europe where European legislation has driven continent-wide adoption. In North America, the US HIPAA and Canadian Privacy Act have driven privacy initiatives. With the adoption of principles and processes such as "privacy by design", "privacy impact assessments" and "building privacy in", backed with strong regulation, organizations are having to make privacy a central part of their business practices. Growing public concern about use of their personal data, mis-use by organizations and personal data breaches are leading to increased, rather than decreased government intervention in this area. Privacy issues are nothing new, but some more recent examples are:
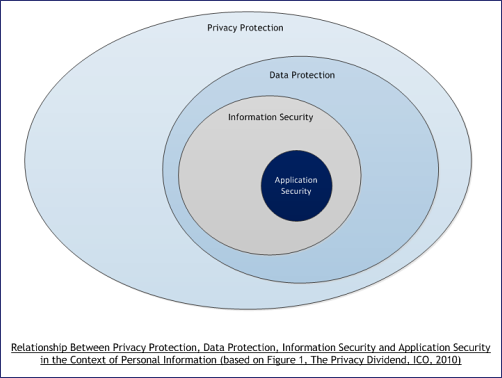
Can we map projects (tools and sections in resources) to business drivers such as "privacy"? Privacy aspects are referred to through the wiki (including projects): But there is not any central guide, and perhaps what there is, does not have enough depth. ASVS includes a whole verification topic about data protection and the ASDR has a page on privacy as a "vulnerability". The OWASP Top ten 2010 mentions personal data in the context of insecure cryptographic storage, but privacy protection is of course much wider than encrypting data. It is of course much wider than application security: But is OWASP offering the correct guidance in this area? Should OWASP be doing more? | ||||||
| WORKING SESSION OUTCOMES / DELIVERABLES | ||
|---|---|---|
| Proposed by Working Group | Approved by OWASP Board | |
| After the Board Meeting - fill in here. | ||
| After the Board Meeting - fill in here. | ||
| After the Board Meeting - fill in here. | ||
| After the Board Meeting - fill in here. | ||
| After the Board Meeting - fill in here. | ||
| After the Board Meeting - fill in here. | ||
| After the Board Meeting - fill in here. | ||
| After the Board Meeting - fill in here. | ||
Working Session Participants
(Add you name by clicking "edit" on the tab on the upper left side of this page)
| WORKING SESSION PARTICIPANTS | ||||||
|---|---|---|---|---|---|---|
| Name | Company | Notes & reason for participating, issues to be discussed/addressed | ||||
| Colin Watson |
Watson Hall |
| ||||
| Lorna Alamri @ |
| |||||
| Achim Hoffmann @ |
sic[!]sec |
see items at Overhauling OWASP website session | ||||
| Elke Roth-Mandutz @ |
GSO-University of Applied Sciences |
web privacy research project | ||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||
| |
| |||||