This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Fiddler Addons for Security Testing Project"
ChrisWeber (talk | contribs) |
ChrisWeber (talk | contribs) |
||
| Line 6: | Line 6: | ||
* [http://www.fiddler2.com Fiddler] is an HTTP debugging proxy with support (and scripting support) for traffic interception, traffic modification, replay, comparison, data parsing, offline usage, NTLM/basic/digest auth, and much more | * [http://www.fiddler2.com Fiddler] is an HTTP debugging proxy with support (and scripting support) for traffic interception, traffic modification, replay, comparison, data parsing, offline usage, NTLM/basic/digest auth, and much more | ||
| + | == Fiddler HTTP Proxy == | ||
The [http://www.fiddler2.com Fiddler] HTTP debugging proxy has a long history with a wide user base and was chosen as the platform for building security testing tools found on this page. By leveraging [http://www.fiddler2.com Fiddler] we can focus our efforts on the security testing logic and let the proxy do its job. | The [http://www.fiddler2.com Fiddler] HTTP debugging proxy has a long history with a wide user base and was chosen as the platform for building security testing tools found on this page. By leveraging [http://www.fiddler2.com Fiddler] we can focus our efforts on the security testing logic and let the proxy do its job. | ||
| + | |||
| + | == Watcher == | ||
| + | Ever find yourself looking for that showstopper exploit in a Web-app, and forgetting to check out all the low-hanging fruit? That's intitially why we created Watcher. For one thing, we don't want to manually inspect a Web-app for many of these issues (cookie settings, SSL configuration, information leaks, etc), but we still want to find and fix them. Watcher provides this level of security analysis, plus provides hot-spot detection to help pen-testers focus in on the spots that will lead to that showstopper exploit. | ||
| + | |||
| + | [http://websecuritytool.codeplex.com/wikipage?title=Checks Descriptions of the security checks] | ||
| + | |||
| + | [http://websecuritytool.codeplex.com/documentation?referringTitle=Home Detailed Documentation] | ||
| + | |||
| + | [http://websecuritytool.codeplex.com/releases/view/22212 Download link] | ||
| + | |||
| + | The security field today has several good choices for HTTP proxies which assist auditors and pen-testers. We chose to implement this as a plugin for Fiddler which already provides the proxy framework for HTTP debugging. Some reasons to use Watcher include: | ||
| + | |||
| + | *'''Safe for the Cloud and hosting environments''' | ||
| + | Being passive gives Watcher several advantages - when applications live in the Cloud there's often a risk that running security testing could damage the shared infrastructure. However, using a passive tool like Watcher ensures that there's no chance of damaging Cloud-like infrastructure. | ||
| + | *'''Safe for production environments''' | ||
| + | Watcher does not attack web-applications with loads of intrusive requests, it doesn't modify inputs to your application. Unlike crawlers and web-application scanners, Watcher does not generate dangerous traffic. It quietly analyzes normal user-interaction and makes educated reports on the security of an application. | ||
| + | *'''Low overhead, no training''' | ||
| + | If you’re building web-applications you already have a development and test staff. Fiddler has been valuable to dev and test for years as a general-purpose HTTP debugging proxy. Watcher fits seamlessly into the picture, providing valuable security insight with no special training requirements, dedicated machines, or other resources. | ||
| + | |||
| + | === Watcher screenshots === | ||
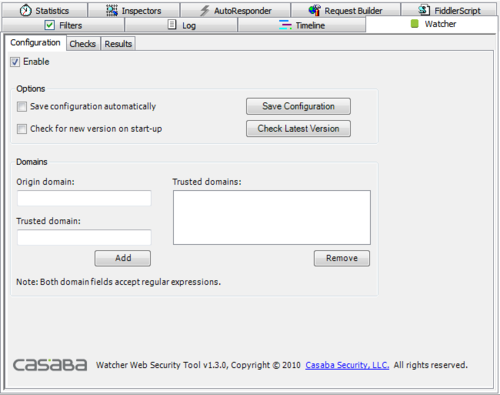
| + | The main configuration screen for Watcher makes it as simple as clicking the 'enable' button. Once you do that, all HTTP traffic starts getting observed and analyzed for security issues. You can also narrow Watcher's scope by specifying an ***origin*** domain that will be the focus of analysis, all others being ignored. Custom Watcher configurations can also be saved so you don't need to re-enter the same information each time you launch the tool. | ||
| + | |||
| + | [[Image:watcher-config.png|500px]] | ||
| + | |||
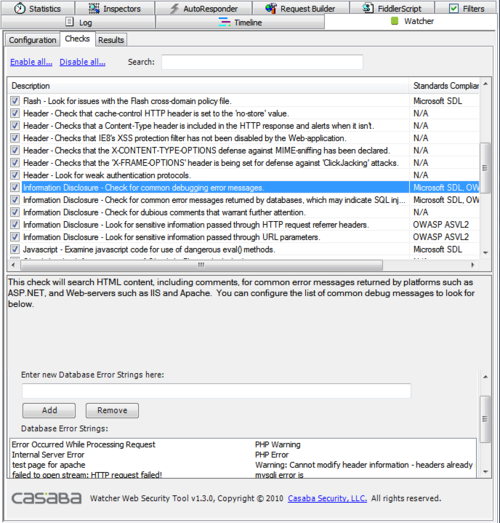
| + | To get more granular, the checks configuration screen allows you enable and disable individual checks. Some checks even come with their own configurations such as noise reduction or string analysis. | ||
| + | |||
| + | [[Image:watcher-checks.png|500px]] | ||
| + | |||
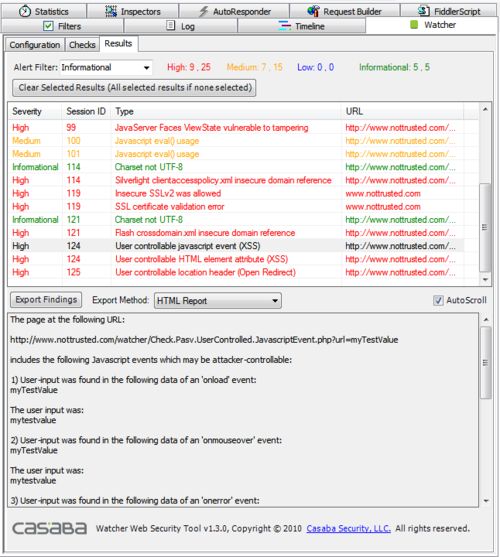
| + | The most interesting screen will probably be the results screen, where each finding is displayed. From here you can remove findings, filter by severity, and export to XML, HTML, or TFS. | ||
| + | |||
| + | [[Image:WatcherResults.png|500px]] | ||
| + | |||
| + | |||
==== FAST - Project About ==== | ==== FAST - Project About ==== | ||
Revision as of 23:52, 6 December 2010
Main
Welcome to the OWASP page presenting Fiddler addons for security testing. This is home of the Watcher and x5s security testing tools built as extensions for the Fiddler HTTP proxy. A quick overview:
- Watcher is a passive vulnerability scanner for Web applications
- x5s is an active cross-site scripting testing tool for Web applications
- Fiddler is an HTTP debugging proxy with support (and scripting support) for traffic interception, traffic modification, replay, comparison, data parsing, offline usage, NTLM/basic/digest auth, and much more
Fiddler HTTP Proxy
The Fiddler HTTP debugging proxy has a long history with a wide user base and was chosen as the platform for building security testing tools found on this page. By leveraging Fiddler we can focus our efforts on the security testing logic and let the proxy do its job.
Watcher
Ever find yourself looking for that showstopper exploit in a Web-app, and forgetting to check out all the low-hanging fruit? That's intitially why we created Watcher. For one thing, we don't want to manually inspect a Web-app for many of these issues (cookie settings, SSL configuration, information leaks, etc), but we still want to find and fix them. Watcher provides this level of security analysis, plus provides hot-spot detection to help pen-testers focus in on the spots that will lead to that showstopper exploit.
Descriptions of the security checks
The security field today has several good choices for HTTP proxies which assist auditors and pen-testers. We chose to implement this as a plugin for Fiddler which already provides the proxy framework for HTTP debugging. Some reasons to use Watcher include:
- Safe for the Cloud and hosting environments
Being passive gives Watcher several advantages - when applications live in the Cloud there's often a risk that running security testing could damage the shared infrastructure. However, using a passive tool like Watcher ensures that there's no chance of damaging Cloud-like infrastructure.
- Safe for production environments
Watcher does not attack web-applications with loads of intrusive requests, it doesn't modify inputs to your application. Unlike crawlers and web-application scanners, Watcher does not generate dangerous traffic. It quietly analyzes normal user-interaction and makes educated reports on the security of an application.
- Low overhead, no training
If you’re building web-applications you already have a development and test staff. Fiddler has been valuable to dev and test for years as a general-purpose HTTP debugging proxy. Watcher fits seamlessly into the picture, providing valuable security insight with no special training requirements, dedicated machines, or other resources.
Watcher screenshots
The main configuration screen for Watcher makes it as simple as clicking the 'enable' button. Once you do that, all HTTP traffic starts getting observed and analyzed for security issues. You can also narrow Watcher's scope by specifying an ***origin*** domain that will be the focus of analysis, all others being ignored. Custom Watcher configurations can also be saved so you don't need to re-enter the same information each time you launch the tool.
To get more granular, the checks configuration screen allows you enable and disable individual checks. Some checks even come with their own configurations such as noise reduction or string analysis.
The most interesting screen will probably be the results screen, where each finding is displayed. From here you can remove findings, filter by severity, and export to XML, HTML, or TFS.
FAST - Project About
- The OWASP Fiddler Addons for Security Testing Project (aka OWASP FAST) is the umbrella for two complementary projects:
- Watcher Project - a passive vulnerability scanner,
- X5s Project - an active XSS testing and input/output encoding detection.
Watcher - Project About
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||||||||||||
X5s - Project About
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||||||||||||