This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "File:Data flow1.jpg"
From OWASP
Davidlowry (talk | contribs) (Example data flow diagram for Application Threat Modeling in Code Review guide.) |
(uploaded a new version of "File:Data flow1.jpg": Typo: "Boundry" -> "Boundary") |
(No difference)
| |
Revision as of 15:28, 30 August 2010
Example data flow diagram for Application Threat Modeling in Code Review guide.
File history
Click on a date/time to view the file as it appeared at that time.
| Date/Time | Thumbnail | Dimensions | User | Comment | |
|---|---|---|---|---|---|
| current | 15:28, 30 August 2010 | 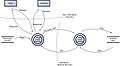 | 749 × 412 (39 KB) | Thomas Herlea (talk | contribs) | Typo: "Boundry" -> "Boundary" |
| 20:52, 10 August 2008 | 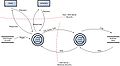 | 749 × 412 (27 KB) | Davidlowry (talk | contribs) | Example data flow diagram for Application Threat Modeling in Code Review guide. |
- You cannot overwrite this file.
File usage
The following page links to this file: