This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Category:OWASP Application Security Verification Standard Project"
Deleted user (talk | contribs) |
|||
| Line 70: | Line 70: | ||
'''Web Application Standard''' | '''Web Application Standard''' | ||
| − | Download ASVS now, for free, [ | + | Download ASVS now, for free, [http://www.owasp.org/images/4/4e/OWASP_ASVS_2009_Web_App_Std_Release.pdf here]. |
'''Other Versions''' | '''Other Versions''' | ||
| − | * Web Application Verification Standard 2008 (Release Version) ([ | + | * Web Application Verification Standard 2008 (Release Version) ([http://www.owasp.org/images/3/35/OWASP_ASVS_2009_Web_App_Std_Release.doc Word]) |
'''Earlier Versions''' | '''Earlier Versions''' | ||
| − | * Web Application Verification Standard 2008 (Beta Version) ([ | + | * Web Application Verification Standard 2008 (Beta Version) ([http://www.owasp.org/images/b/b4/OWASP_ASVS_Web_Edition_2008_Beta.pdf PDF], [http://www.owasp.org/images/e/e6/OWASP_ASVS_Web_Edition_2008_Beta.doc Word]) |
| − | * Web Application Verification Standard 2008 (Alpha Version) ([ | + | * Web Application Verification Standard 2008 (Alpha Version) ([http://www.owasp.org/images/d/d1/OWASP_ASVS_Web_Edition_2008_Alpha.pdf PDF], [http://www.owasp.org/images/0/0b/OWASP_ASVS_Web_Edition_2008_Alpha.doc Word]) |
<br>{{OWASP Book|7295724}} | <br>{{OWASP Book|7295724}} | ||
Revision as of 13:25, 30 November 2009
About
|
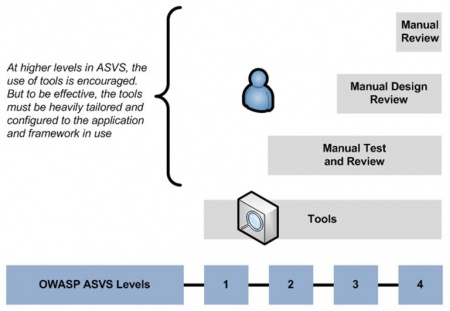
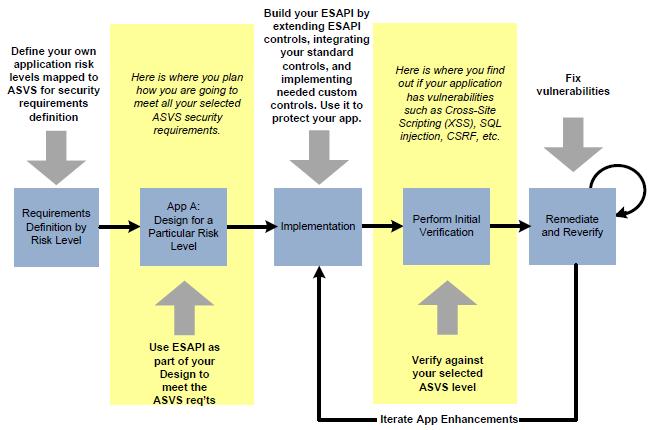
OWASP Documentation Project Application Security Verification Standards (ASVS) Application Security Verification Standards are specifications produced by OWASP in cooperation with secure applications developers and verifiers worldwide for the purpose of accelerating the deployment of secure Web applications. First published in 2008 as a result of an OWASP Summer of Code grant and meetings with a small group of early adopters, the ASVS documents have become widely referenced and implemented. Further development of ASVS occurs through mailing list discussions and occasional workshops, and suggestions for improvement are welcome. For more information, please contact us. You can download it here. Need help getting started? ASVS is brand new after all! Read this. Use this and this! Frequently asked questions can be found here. How ASVS Works ASVS defines four levels of Web application security verification. Each level includes a set of requirements for verifying the effectiveness of security controls that are being used. |
|
FAQ
|
More About OWASP ASVS
Related projects |
Did You Know...
|
Download
Web Application Standard
Download ASVS now, for free, here.
Other Versions
- Web Application Verification Standard 2008 (Release Version) (Word)
Earlier Versions
- Web Application Verification Standard 2008 (Beta Version) (PDF, Word)
- Web Application Verification Standard 2008 (Alpha Version) (PDF, Word)
| |
This project has produced a book that can be downloaded or purchased. Feel free to browse the full catalog of available OWASP books. |
Precedents/Interpretations
PI-0001: Are there levels between the levels?
- Issue: Are there levels between the levels for the cases where "The specification for an application may require OWASP ASVS Level N, but it could also include other additional detailed requirements such as from a higher ASVS level"?
- Resolution: No. Use of alternate level definitions or notations such as "ASVS Level 1B+" is discouraged.
- References: ASVS section "Application Security Verification Levels"
PI-0002: Is use of a master key simply another level of indirection?
- Issue: If a master key is stored as plaintext, isn't using a master key simply another level of indirection?
- Reolution: No. There is a strong rationale for having a "master key" stored in a secure location that is used to encrypt all other secrets. In many applications, there are lots of secrets stored in many different locations. This greatly increases the likelihood that one of them will be compromised. Having a single master key makes managing the protection considerably simpler and is not simply a level of indirection.
- References: ASVS verification requirement V2.14
News
Project News
- 07/06/2009 - OWASP ASVS users list updated to include Minded Security
- 07/02/2009 - OWASP ASVS and "Man vs. Code" ASVS article mentioned in Toorcamp 2009 presentation
- 07/01/2009 - OWASP ASVS users list updated to include CETEC/CTCSE - Divisão Processos de Segurança no Desenvolvimento SERPRO - Serviço Federal de Processamento de Dados / Sede - Brasília-DF (CETEC / CTCSE - Division of Security in Development Processes SERPRO - Federal Service of Data Processing / Headquarters - Brasília-DF)
- 06/22/2009 - OWASP ASVS rulesets are added to Casaba Security's security testing tool Watcher version 1.2.0. First tool vendor to do so!
- 06/09/2009 - OWASP ASVS users list updated to include CGI Federal
- 06/03/2009 - OWASP ASVS Release Version published! Mike Boberski, Jeff Williams, and Dave Wichers are the primary authors.
- 05/15/2009 - OWASP ASVS users list updated to include Denim Group
- 05/13/2009 - OWASP ASVS is presented by Dave Wichers at OWASP AppSec Europe 2009 - Poland.
- 05/04/2009 - OWASP ASVS users list updated to include Casaba Security
- 05/09/2009 - OWASP ASVS is discussed in the Department of Defense (DoD) Information Assurance Technology Analysis Center (IATAC) State-of-the-Art-Report (SOAR) on "Measuring Cyber Security and Information Assurance".
- 04/09/2009 - OWASP ASVS is the subject of an opinion piece by Mike Boberski in SC Magazine on the need for a web app standard
- 04/08/2009 - OWASP ASVS users list updated to include ps_testware.
- 04/06/2009 - OWASP ASVS users list updated to include Federal Deposit Insurance Corporation (FDIC).
- 03/13/2009 - OWASP ASVS is presented by Dave Wichers at OWASP Software Assurance Day DC 2009 in conjunction with the Software Assurance Forum sponsored by the US Department of Homeland Security, Department of Defense and National Institute of Standards and Technology.
- 02/25/2009 – OWASP ASVS proposed updates based on pilots being considered.
- 01/22/2009 - OWASP ASVS has been integrated into the OWASP Secure Software Contract Annex in the OWASP Legal Project.
- 01/08/2009 - OWASP ASVS is presented by Mike Boberski at the OWASP Washington VA Local Chapter meeting.
- 12/29/2008 - OWASP ASVS is the subject of an article by DarkReading.
- 12/08/2008 - OWASP ASVS Final assistance required! Please join the mailing list for more information and assignments.
- 12/05/2008 - OWASP ASVS exits the Summer of Code 2008! The Beta draft of the Web Application Edition is released! Mike Boberski, Jeff Williams, and Dave Wichers are the primary authors.
- 11/03/2008 - OWASP ASVS is presented by Jeff Williams at OWASP EU Summit 2008.
- 10/03/2008 - OWASP ASVS Alpha draft is released! Mike Boberski is the primary author.
- 04/16/2008 - OWASP ASVS Summer of Code 2008 proposal submitted by Mike Boberski wins!
Weekly Status
Users/Contributors
|
Project Leader Project Contributors |
Project Sponsorship |
Users A broad range of companies and agencies around the globe have added ASVS to their software assurance tool boxes, including:
Organizations listed above are not accredited by OWASP. Neither their products or services have been endorsed by OWASP. Use of ASVS may include for example providing verification services using the standard. Use of ASVS may also include for example performing internal evaluation of products with the OWASP ASVS in mind, and NOT making any claims of meeting any given level in the standard. Please let us know how your organization is using OWASP ASVS. Include your name, organization's name, and brief description of how you use the standard. The project lead can be reached here. |
This project licensed under the Creative Commons Attribution ShareAlike 3.0.
Articles Below - More About ASVS and Using It
Pages in category "OWASP Application Security Verification Standard Project"
The following 21 pages are in this category, out of 21 total.
H
- How to bootstrap the NIST risk management framework with verification activities
- How to bootstrap your SDLC with verification activities
- How to create verification project schedules
- How to perform a security architecture review at Level 1
- How to perform a security architecture review at Level 2
- How to specify verification requirements in contracts
- How to write verifier job requisitions