This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Section 2: WebGoat"
(→How it works) |
(→How it works) |
||
| Line 27: | Line 27: | ||
| − | Each WebGoat lesson is designated by the 'menu' parameter in the query string. In the | + | Each WebGoat lesson is designated by the 'menu' parameter in the query string. In the screen shot below, the 'screen' parameter will vary but the 'menu' paramater will always be 900 for this lesson. There is no similar way of easily identifying sublessons within a lesson or stages within a sublesson; ths sublesson 'Stored XSS Attacks' will also have 'menu' value of 900, and each of the stages in the 'LAB: Cross-Site Scripting' sublesson will also have 'menu' value of 900: |
[[Image:OWASP_ModSecurity_Securing_WebGoat_Section_2_SS4.jpg]] | [[Image:OWASP_ModSecurity_Securing_WebGoat_Section_2_SS4.jpg]] | ||
| + | |||
When a WebGoat lesson is completed successfully, there are 3 different areas that denote this: | When a WebGoat lesson is completed successfully, there are 3 different areas that denote this: | ||
| Line 36: | Line 37: | ||
[[Image:OWASP_ModSecurity_Securing_WebGoat_Section_2_SS5.jpg]] | [[Image:OWASP_ModSecurity_Securing_WebGoat_Section_2_SS5.jpg]] | ||
| + | |||
* A report card in Section 18 of WebGoat: | * A report card in Section 18 of WebGoat: | ||
Revision as of 05:06, 24 July 2008
Overview
From the WebGoat home page at OWASP: "WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat application. For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. The application is a realistic teaching environment, providing users with hints and code to further explain the lesson."
WebGoat can be downloaded from http://code.google.com/p/webgoat/downloads/list. It runs within Tomcat and can either be used stand-alone "out-of-the-box" with a version of Tomcat that is packaged with it, or a WebGoat.war file can be dropped onto an existing Tomcat installation.
Explaining WebGoat and the WebGoat lessons in detail is beyond the scope of this document. Each sublesson has a solution - available from the menu at the top of each lesson - that explains the purpose of the lesson. The motivation of the WebGoat solution (which is exploiting the vulnerability) is often accompanied by screenshots of WebGoat and WebScarab, the web proxy that is used in the solutions. If the reader does not wish to go through the WebGoat lessons themselves, the solutions are the "cheat sheets" for WebGoat, and because of that the solutions are provided in this project's documentation as is. If this is insufficient, installing and using WebGoat may be necessary to gain a complete understanding of the lessons.
How it works
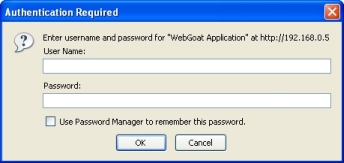
WebGoat users are configured in the tomcat-users.xml configuration file.
Here is the WebGoat login page, which uses Basic Authentication:
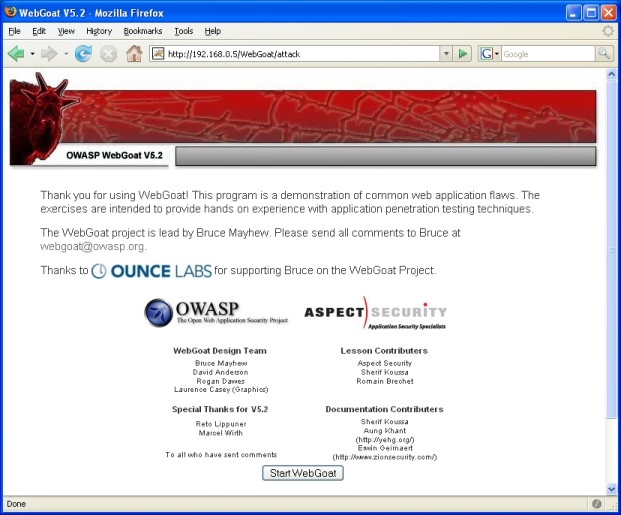
Next is the entrance/start page; a JSESSIONID cookie is set for the session variable:
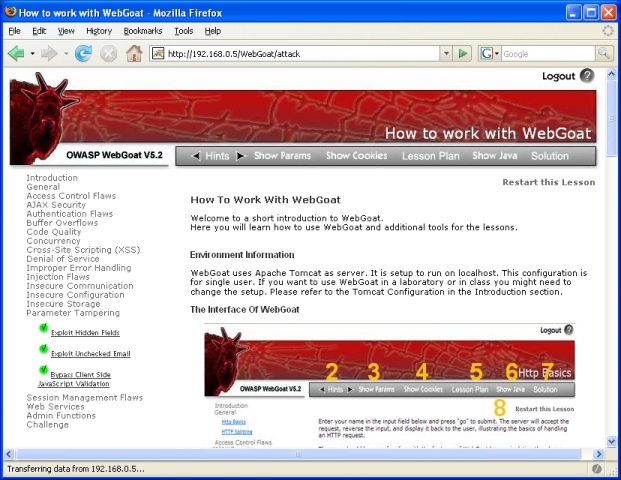
Here is an overview of the lesson menu on the left side of the page that is used for navigation:
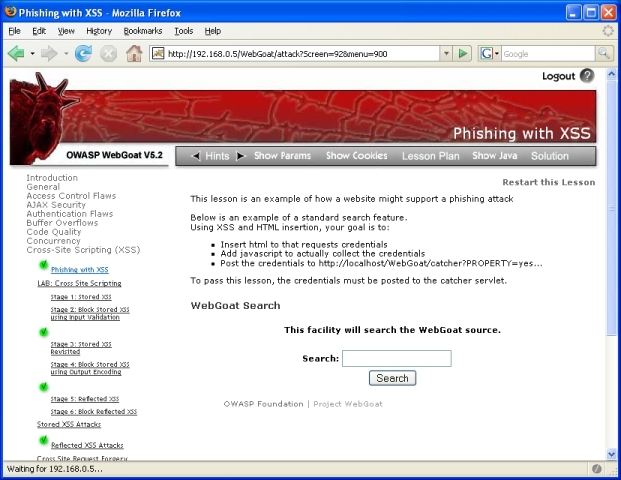
Each WebGoat lesson is designated by the 'menu' parameter in the query string. In the screen shot below, the 'screen' parameter will vary but the 'menu' paramater will always be 900 for this lesson. There is no similar way of easily identifying sublessons within a lesson or stages within a sublesson; ths sublesson 'Stored XSS Attacks' will also have 'menu' value of 900, and each of the stages in the 'LAB: Cross-Site Scripting' sublesson will also have 'menu' value of 900:
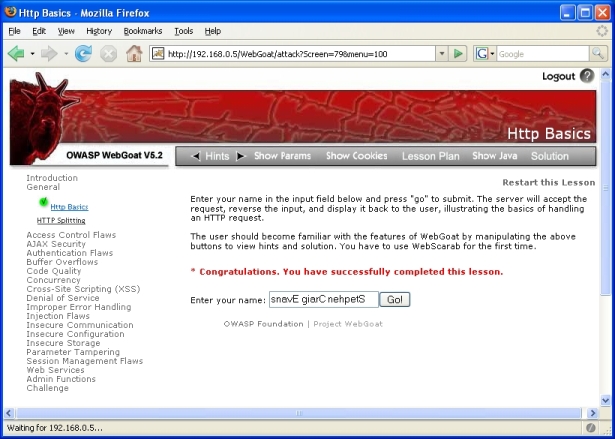
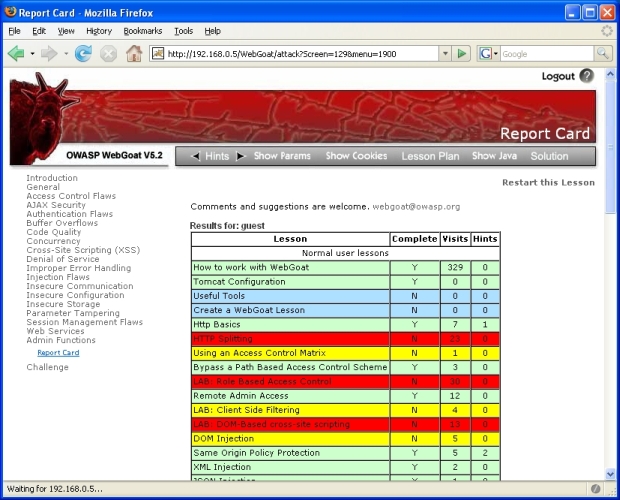
When a WebGoat lesson is completed successfully, there are 3 different areas that denote this:
- A message in red in the body of the HTML page and a green check mark beside the lesson in the menu on the left side:
- A report card in Section 18 of WebGoat: