This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Security Integration System"
MB netblue4 (talk | contribs) (→Description) |
MB netblue4 (talk | contribs) (→Preparation phase) |
||
| Line 141: | Line 141: | ||
</div> | </div> | ||
<ul> | <ul> | ||
| + | <li>SCAT comes out the box with a standard OWASP secure code requirements map. This mapping need to be modified to the specific organisation requirements</li> | ||
| + | <br> | ||
<li><b>Information security and development team</b> use the <b>Internal mapping </b> screen to | <li><b>Information security and development team</b> use the <b>Internal mapping </b> screen to | ||
<ol> | <ol> | ||
| Line 154: | Line 156: | ||
</div> | </div> | ||
<ul> | <ul> | ||
| − | <li> | + | <li>To generate these requirements we perform a risk assessment on client application landscape and identifies</li> |
| − | <li> | + | <ol> |
| + | <li>Critical applications and functions</li> | ||
| + | <li>Risk associated with each critical application function</li> | ||
| + | <li>Architectural security requirements to secure each critical application functions</li> | ||
| + | <li>Client specific secure code blocks to implement security requirements</li> | ||
| + | <li>Secure test plans to verify risk has been mitigated</li> | ||
| + | </ol> | ||
| + | <br> | ||
<li><b>Tool administrators</b> use the <b>Internal mapping </b> screen to | <li><b>Tool administrators</b> use the <b>Internal mapping </b> screen to | ||
<ol> | <ol> | ||
Revision as of 12:13, 2 September 2019
Table of content
Description
Secure code assurance tool (SCAT) is used by inhouse and third party development teams to build, verify and assure secure software BuildVerifyAssure
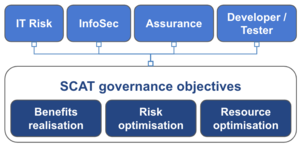
SCAT has the following governance objectives implemented by the following “first line of defense” functions Benefits realisation: Enabling development teams to deliver at speedRisk optimisation: Minimise the negative and maximise the positive consequencesResource optimisation: Predictable, repeatable and consistent level of security across all teams
I've detailed the other domains in an article that will be published in the Nov/Dec issue of the ISC2 magazine, I will add a link here after publication.
See how developers use SCATSee below how the Secure code assurance tool integrates security into software development phases
Preparation phaseWhen developing secure software we need to consider both standard secure code and client specific architectural requirements Standard secure code requirements
Client specific architectural requirements
How does the SCAT implement first line of defencePromoting compliance to security requirements
Minimising the impact of audit and assurance
Informing risk based decision making
Integrating security into the software development process
LicensingThis program is free software: you can redistribute it and/or modify it under the terms of the link GNU Affero General Public License 3.0 as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version. Project Resources[Installation Package] [Source Code] Project LeaderClassifications
| ||||||