This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "The General HTTP Authentication Framework"
(Create `General HTTP Authentication Framework` page) (Tag: Visual edit) |
m (include the page in `Web Application Authentication Schemes` category) |
||
| Line 38: | Line 38: | ||
[https://www.iana.org/assignments/http-authschemes/http-authschemes.xhtml IANA Authentication Scheme Registry] | [https://www.iana.org/assignments/http-authschemes/http-authschemes.xhtml IANA Authentication Scheme Registry] | ||
| + | |||
| + | [[Category:Web Application Authentication Schemes]] | ||
Latest revision as of 17:11, 5 June 2019
Introduction
HTTP provides a general framework for access control and authentication, through an extensible set of challenge-response authentication schemes, that can be used by a server to challenge a client request and by a client to provide information about the client.
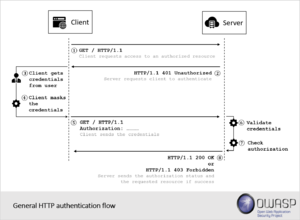
Authentication flow
1. A client requests the server to access an authorized resource.
- Client is anything that requests a resource. Example: Browser, web service
- Server is an application that serves the client's request.
- Resource can be any data/information. Example: HTML document, media files
2. The server requests the client to authenticate first.
- The server responds to the client with a 401 (Unauthorized) response status and provides information on how to authenticate with a WWW-Authenticate response header containing at least one challenge.
3. The client prepares for the authentication.
- The client checks the response status code and understands he needs to authenticate first.
- Usually, the client presents a password prompt to the user to get the credentials.
- Some modern applications hide/prevents the default password prompt using client-side JavaScript and show a login form to provide a rich user experience.
- The client masks/transforms the credentials based on the HTTP authentication scheme it chose/programmed to.
4. The client sends the (processed)credentials to the server.
- The client then issues the request to the server with an Authorization request-header field with the HTTP authentication scheme being used and the masked credentials.
5. The server validates the received credentials.
- The validation process/algorithm depends on the HTTP authentication scheme being used.
6. The server informs the client about the authorization status.
- If the validation succeeds then the server checks if the authenticated entity has the privilege to access the resource
Authentication schemes that are based on the general HTTP authentication framework
- Basic [RFC7617]
- Bearer[RFC6750]
- Digest[RFC7616]
- HOBA [RFC7486, Section 3]
- Mutual [RFC8120]
- Negotiate [RFC4559, Section 3]
- OAuth [RFC5849, Section 3.5.1]
- SCRAM-SHA-1 [RFC7804]
- SCRAM-SHA-256 [RFC7804]
- Vapid [RFC8292]