This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Video Game Security Framework"
m |
(→Prevention) |
||
| Line 532: | Line 532: | ||
In the prevention phase begins the implementation of a security solution. | In the prevention phase begins the implementation of a security solution. | ||
This phase can have many sub tasks/levels depending on what you are implementing. | This phase can have many sub tasks/levels depending on what you are implementing. | ||
| − | |||
| − | |||
| − | |||
| + | <br /> | ||
| + | '''Prevention Process''' | ||
| + | <br /> | ||
| + | :1. Plan | ||
| + | |||
| + | :2. Analyze | ||
| + | |||
| + | :3. Design | ||
| + | |||
| + | :4. Build | ||
| + | |||
| + | :5. Deploy | ||
| + | <br /> | ||
| + | '''1. Plan''' | ||
| + | |||
| + | <br /> | ||
| + | Some of the planning work could have been done in the strategy phase. | ||
| + | |||
| + | <br /> | ||
| + | '''''Example Questions to ask:''''' | ||
What do we need a security solution for? | What do we need a security solution for? | ||
1. Application | 1. Application | ||
| Line 543: | Line 560: | ||
3. IT infrastructure | 3. IT infrastructure | ||
4. Identity & Access Management | 4. Identity & Access Management | ||
| + | <br /> | ||
| + | '''''What''''' do we need a security solution for? | ||
| + | <br /> | ||
| + | :1) Software Application | ||
| + | |||
| + | ::a) General Data Protection Regulation (GDPR) | ||
| + | ::b) Payment Card Industry Data Security Standard (PCI) | ||
| + | ::c) The National Institute for Standards and Technology (NIST) | ||
| + | |||
| + | :2) Data Protection | ||
| + | |||
| + | ::a) Open Web Application Security Project (OWASP) | ||
| + | ::b) Payment Card Industry Data Security Standard (PCI) | ||
| + | ::c) The National Institute for Standards and Technology (NIST) | ||
| + | |||
| + | :3) IT Infrastructure | ||
| + | |||
| + | ::a) Microsoft | ||
| + | ::b) Sony | ||
| + | |||
| + | |||
| + | |||
| + | :4) Identify & Access Management | ||
| + | <br /> | ||
| + | '''''Does''''' it align with our overall security & business strategy? | ||
| + | |||
| + | <br /> | ||
| + | '''''Does''''' it fit in our current architecture? | ||
| + | <br /> | ||
| + | '''''What''''' would the impact on this solution be? | ||
| + | <br /> | ||
| + | |||
| + | '''2. Analyze''' | ||
| + | <br /> | ||
| + | |||
| + | '''''What''''' capabilities do we need to assess? | ||
| + | :1) Application | ||
| + | :2) Architecture | ||
| + | :3) Processes & Flows | ||
| + | <br /> | ||
| + | |||
| + | '''''What''''' functions exist in the current security solutions vs future? | ||
| + | <br /> | ||
| + | |||
| + | '''3. Design''' | ||
| + | <br /> | ||
| + | '''''How''''' exactly do we want this solution to function? | ||
| + | :1) Configuration | ||
| + | |||
| + | '''4. Build''' | ||
| + | :1) Assigning work tasks and doing them | ||
| + | <br /> | ||
| + | |||
| + | |||
| + | '''5. Test''' | ||
| + | :1) What is our testing strategy? | ||
| + | |||
| + | :2) How do we shift when bugs are found? | ||
| + | |||
| + | <br /> | ||
| + | |||
| + | '''6. Deploy''' | ||
| + | :1) What is our "go-live" strategy for moving the solution from development to production? | ||
| + | |||
| + | <br /> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
{{Social Media Links}} | {{Social Media Links}} | ||
Revision as of 03:24, 2 May 2019
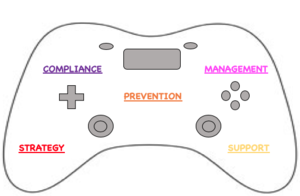
- About the Project
- Business Strategy & Risk
- Governance & Compliance
- Prevention
- Management
- Service Delivery/ Support
- Resources
- Trending
- Community
- Testing Tools
- Project About
OWASP Video Game Security Framework (VGSF)OWASP Video Game Security Framework (VGSF) defines an approach to discovering solutions for strategy, development, operations, and management surrounding security for video game industry business models
Most organizations that operate in the digital landscape approach security as a last afterthought when compared to the overall business strategy and operations. In the recent years it has become more apparent the consequences of such behavior with increasingly amounts of data breaches happening. The cost associated with an organization’s loss of intellectual property and other digital assets has reached the millions.
This will be one of the largest sections as it is comprised of many different aspects of overall cyber security
LicensingThe OWASP Video Game Security Framework is free to use. It is licensed under the http://creativecommons.org/licenses/by-sa/3.0/ Creative Commons Attribution-ShareAlike 3.0 license], so you can copy, distribute and transmit the work, and you can adapt it, and use it commercially, but all provided that you attribute the work and if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one.
|
What is the OWASP Video Game Security Framework?The goal of the OWASP Video Game Security Framework is to provide an adaptable blueprint to guide the development and deployment of cyber resiliency within a video game enterprise operation. The target audience for the project includes:
Project Leaders
Contributors
Related Projects |
CollaborationJoin the discord channel: [1] Quick DownloadCOMING SOON News and Events
Classifications
| |||||||
Business Strategy & Risk
|
What is the Business Strategy & Risk Section?This section provides an overview of the various places an attacker can target to harm a given game infrastructure. Sub-project Leader
Related Projects
CollaborationJoin the discord channel: [2] Quick Download
News and Events
|
Governance & ComplianceThe purpose of the Governance & Compliance phase in the framework is to layout a guiding path to establishing and maintaining a G&C operating model. With the current trends in gaming raising the risk to the public's privacy, having a proper G&C model will keep the business continuity high therefore lowering the risks related to non-compliance.
2. Audit
Auditing involves performing routine internal checks to ensure policies are being followed by all.
**Its important to be able to perform an audit on call for unpredictable external shifts in compliance requirements
**Overall if anything goes wrong, will you be able to pinpoint where non-compliance is. How do we want to view information on what is being monitored?
|
What is the Governance & Compliance (G&C) Section?This section provides an overview of the various places an attacker can target to harm a given game infrastructure. Sub-project Leader
Related Projects
CollaborationResources
News and Events
|
PreventionIn the prevention phase begins the implementation of a security solution. This phase can have many sub tasks/levels depending on what you are implementing.
2. Analyze
What capabilities do we need to assess?
What functions exist in the current security solutions vs future?
3. Design
4. Build
6. Deploy
|
The Exploits ProjectThe Exploits provides information on what types of tools and techniques an attacker might use to accomplish his/her goal. Sub-project Leader
Related Projects
CollaborationResourcesNews and Events
|
ManagementThis list refers to what a given attacker might be trying to accomplish within the game by performing a given attack. This could relate very closely (or not) with the technical impact or business impact cause by the behavior.
|
What is the Attacker Goals ProjectThe Attacker Goals Project provides information on what types of outcomes attackers might try to achieve within or outside of the game they're attacking. Sub-project Leader
Related ProjectsCollaborationResourcesNews and Events
|
Service Delivery/ SupportThe following is a list of possible negative outcomes that can occur as the result of someone successfully attacking a given game.
|
What is the Negative Outcomes Project?The Negative Outcomes Project provides information on what types of situations could manifest within the game if bugs or exploits are not successfully addressed. Project Leader
Related ProjectsCollaborationResourcesNews and Events
|
ResourcesThis page will list additional resources related to game security that may provide more detailed context.
|
What is the Game Security Vulnerabilities Project?The Security Vulnerabilities Project provides information on what types of vulnerabilities exist within games, and which attack surfaces they fall under. Project Leaders
Related ProjectsCollaborationJoin the discord channel: [3]
ResourcesNews and Events
|
Video Game Trends
This section is dedicated to trends in gaming and how it can evaluated from a security perspective
| ID | Vulnerabilty Name | Description | Surface Area | Goal | Techical Impact | Business Impact | Defense | Ref | Game | Genre |
|---|---|---|---|---|---|---|---|---|---|---|
| V1 | Local Resource Modification, Client-side Logic Flaw | In 2015 The Division experienced an exploit that allowed an attacker to switch weapons rapidly, applying weapon buffs in a stacking manner, with no cap. | Game Client | Unfair Player Advantage | Player Anger | Players leave, Lost Revenue | Cryptographic Integrity Checks on Game Client | http://www.gamesradar.com/theres-a-division-damage-stacking-glitch-if-youve-got-fast-fingers/ | 3PS/1PS/MMO | |
| VN1 | "The attacker attacked and edited the LOCAL GAME CLIENT (Attack Surface), which had a LACK OF CLIENT INTEGRITY CONTROLS (Vulnerability), which allowed her to ARTIFICIALLY INCREASE HER ABILITIES (Attacker Goal), ultimately leading to an UNHAPPY PLAYER BASE (Negative Outcome) and DECLINING GAME REVENUE (Negative Outcome) due to cheating, which could have been prevented by CRYPTOGRAPHIC INTEGRITY CHECKS ON GAME CLIENT”
| |||||||||
Working Data Collection Spreadsheet:
https://docs.google.com/spreadsheets/d/1Og08wyHsqtODBDkU_M2zHAvdxc63GSu-OmT8NjCc9Ak/edit#gid=0
The VGSF team has open opportunities for individuals to collaborate and contribute to the project.
- Improving the framework schema, e.g., vulns, attack surfaces, technical impacts, business impacts, defenses, etc.
- Adding content to any of the various sections
- Input from avid gamers on how useful this is to them
- Input from app security experts
- Input from security types working at gaming companies
- Input from game company business types
If you have interest in helping, reach out to us and we'll make you a contributor.
Commonly Used Game Hacking Tools
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||