This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Jupiter"
From OWASP
Mattstanchek (talk | contribs) m (→High Level Design) (Tag: Visual edit) |
Mattstanchek (talk | contribs) (Added Roadmap and FAQ) |
||
| Line 68: | Line 68: | ||
= Roadmap = | = Roadmap = | ||
| − | + | ==Jupiter Application Inventory Management System Roadmap== | |
| + | # Collector Service | ||
| + | ## Authentication | ||
| + | ##* Utilize Auth Service for JWT validation | ||
| + | ## Authorization | ||
| + | ##* Based on JWT payload, enforce restrictions on CRUD operations | ||
| + | ## Database Connectivity | ||
| + | ##*Update Mongo connection code to update deprecated connection method | ||
| + | ##Input Validation | ||
| + | ##*Input length checks | ||
| + | ##*Input type checks | ||
| + | ##Data Fields | ||
| + | ##*Enable data fields beyond Common Name and Primary Owner | ||
| + | ##Containerization | ||
| + | ##*Prepare Dockerfile | ||
| + | ##*Build Docker container | ||
| + | ##*Deploy and test Docker container | ||
| + | #Curated Inventory Service | ||
| + | ##Authentication | ||
| + | ##*Utilize Auth Service for JWT validation | ||
| + | ##Authorization | ||
| + | ##*Based on JWT payload, enforce restrictions on CRUD operations | ||
| + | ##Input Validation | ||
| + | ##*Input length checks | ||
| + | ##*Input type checks | ||
| + | ##Data Fields | ||
| + | ##*Enable Application-specific data fields beyond Common Name and Primary Owner | ||
| + | ##*Enable capture of Collector Service instance ID | ||
| + | ##Data Integrity | ||
| + | ##*Restrict Common Name to unique values | ||
| + | ##Containerization | ||
| + | ##*Prepare Dockerfile | ||
| + | ##*Build Docker container | ||
| + | ##*Deploy and test Docker container | ||
| + | #Auth Service | ||
| + | ##Authentication | ||
| + | ###Enable LDAP authentication | ||
| + | ###*Build LDAP integration capabilities | ||
| + | ###*Based on successful username/password LDAP authentication, provide time-limited JSON Web Token for subsequent requests | ||
| + | ###*Enable facility to validate expiration of tokens and deny access to expired tokens | ||
| + | ##Authentication | ||
| + | ##*Define user roles (administrator, reader, creator/updater) | ||
| + | ##*Enable issuance of tokens that restrict access based on user role | ||
| + | #Management Console | ||
| + | ##Base Architecture | ||
| + | ###Add Local SQLite Database | ||
| + | ###*Enable saving of configuration and preferences | ||
| + | ##Authentication | ||
| + | ###Collector Services | ||
| + | ###*Build an interface to allow configuration of Collector Services | ||
| + | ###Curated Inventory Service | ||
| + | ###*Build an interface to allow configuration of Curated Inventory Service | ||
| + | ##Data Fields | ||
| + | ##*Enable Application-specific data fields beyond Common Name and Primary Owner | ||
| + | ##External Integrations | ||
| + | ##:Consistent naming across multiple external Application Security tools will allow for greater future automation and reporting as well as utilization. | ||
| + | ##*Enable set up of Application in Fortify Software Security Center | ||
| + | ##*Enable set up of Application in OWASP Dependency-Track | ||
| + | ##*Enable set up of Application in OWASP Defect Dojo | ||
| + | ##*Enable set up of Application in OWASP SecurityRAT | ||
| + | ##User Experience | ||
| + | ###Antecessors | ||
| + | ###*Aggregate all Collectors’ data in available Antecessors list when there is more than one Collector Service defined | ||
| + | #Jenkins Collector Plugin | ||
| + | ##Input Validation | ||
| + | ##*Input length checks | ||
| + | ##*Input type checks | ||
| + | ##Connectivity Validation | ||
| + | ##*Add a “Test Connection…” button to the Global config screen to test the Collector URL and token | ||
| + | ##Data Fields | ||
| + | ##*Enable Application-specific data fields beyond Common Name and Primary Owner under “Advanced” | ||
| + | |||
= About Jupiter = | = About Jupiter = | ||
| − | + | ==FAQ== | |
| + | Q: Why is this project named "Jupiter"? | ||
| + | |||
| + | A: In ''2001: A Space Odyssey'', the Discovery One embarked on a mission to investigate the signal sent from the monolith on the Moon to Jupiter. In ''2010: The Year We Make Contact'', the crews of the Discovery and Leonov witness countless monoliths emerge from Jupiter before it is converted into a star. Aside from the cool sci-fi reference, there is an analog to what this project is for -- to start with a small amount of information about software applications in an organization's portfolio and build upon that knowledge to find more. | ||
__NOTOC__ <headertabs></headertabs> | __NOTOC__ <headertabs></headertabs> | ||
Revision as of 22:58, 23 March 2019
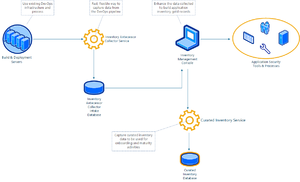
Jupiter Application Inventory Management System Roadmap
- Collector Service
- Authentication
- Utilize Auth Service for JWT validation
- Authorization
- Based on JWT payload, enforce restrictions on CRUD operations
- Database Connectivity
- Update Mongo connection code to update deprecated connection method
- Input Validation
- Input length checks
- Input type checks
- Data Fields
- Enable data fields beyond Common Name and Primary Owner
- Containerization
- Prepare Dockerfile
- Build Docker container
- Deploy and test Docker container
- Authentication
- Curated Inventory Service
- Authentication
- Utilize Auth Service for JWT validation
- Authorization
- Based on JWT payload, enforce restrictions on CRUD operations
- Input Validation
- Input length checks
- Input type checks
- Data Fields
- Enable Application-specific data fields beyond Common Name and Primary Owner
- Enable capture of Collector Service instance ID
- Data Integrity
- Restrict Common Name to unique values
- Containerization
- Prepare Dockerfile
- Build Docker container
- Deploy and test Docker container
- Authentication
- Auth Service
- Authentication
- Enable LDAP authentication
- Build LDAP integration capabilities
- Based on successful username/password LDAP authentication, provide time-limited JSON Web Token for subsequent requests
- Enable facility to validate expiration of tokens and deny access to expired tokens
- Enable LDAP authentication
- Authentication
- Define user roles (administrator, reader, creator/updater)
- Enable issuance of tokens that restrict access based on user role
- Authentication
- Management Console
- Base Architecture
- Add Local SQLite Database
- Enable saving of configuration and preferences
- Add Local SQLite Database
- Authentication
- Collector Services
- Build an interface to allow configuration of Collector Services
- Curated Inventory Service
- Build an interface to allow configuration of Curated Inventory Service
- Collector Services
- Data Fields
- Enable Application-specific data fields beyond Common Name and Primary Owner
- External Integrations
- Consistent naming across multiple external Application Security tools will allow for greater future automation and reporting as well as utilization.
- Enable set up of Application in Fortify Software Security Center
- Enable set up of Application in OWASP Dependency-Track
- Enable set up of Application in OWASP Defect Dojo
- Enable set up of Application in OWASP SecurityRAT
- User Experience
- Antecessors
- Aggregate all Collectors’ data in available Antecessors list when there is more than one Collector Service defined
- Antecessors
- Base Architecture
- Jenkins Collector Plugin
- Input Validation
- Input length checks
- Input type checks
- Connectivity Validation
- Add a “Test Connection…” button to the Global config screen to test the Collector URL and token
- Data Fields
- Enable Application-specific data fields beyond Common Name and Primary Owner under “Advanced”
- Input Validation
FAQ
Q: Why is this project named "Jupiter"?
A: In 2001: A Space Odyssey, the Discovery One embarked on a mission to investigate the signal sent from the monolith on the Moon to Jupiter. In 2010: The Year We Make Contact, the crews of the Discovery and Leonov witness countless monoliths emerge from Jupiter before it is converted into a star. Aside from the cool sci-fi reference, there is an analog to what this project is for -- to start with a small amount of information about software applications in an organization's portfolio and build upon that knowledge to find more.