This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Jupiter"
From OWASP
Mattstanchek (talk | contribs) (Initial update) (Tag: Visual edit) |
Mattstanchek (talk | contribs) m |
||
| Line 3: | Line 3: | ||
{| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | {| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | ||
| style="border-right: 1px dotted gray;padding-right:25px;" valign="top" | | | style="border-right: 1px dotted gray;padding-right:25px;" valign="top" | | ||
| − | = Introduction = | + | == Introduction == |
An Application Security program is more successful when coverage of its processes and tooling can be proven. Unfortunately, software inventory lists consist of some custom-written applications for an organization but also include systems and software that aren't in scope for a traditional AppSec program (Active Directory or Adobe Reader, for instance). | An Application Security program is more successful when coverage of its processes and tooling can be proven. Unfortunately, software inventory lists consist of some custom-written applications for an organization but also include systems and software that aren't in scope for a traditional AppSec program (Active Directory or Adobe Reader, for instance). | ||
| Line 17: | Line 17: | ||
If "who owns this?" or "did you know this was in production?" sounds familiar, you're not alone. | If "who owns this?" or "did you know this was in production?" sounds familiar, you're not alone. | ||
| − | = OWASP Jupiter - Application Inventory Management System = | + | == OWASP Jupiter - Application Inventory Management System == |
Existing DevOps processes already know what software is being built and when it is being deployed. | Existing DevOps processes already know what software is being built and when it is being deployed. | ||
| Line 27: | Line 27: | ||
* Enhanced metrics capabilities to determine tool and process coverage as well as the organization’s Application Security maturity level | * Enhanced metrics capabilities to determine tool and process coverage as well as the organization’s Application Security maturity level | ||
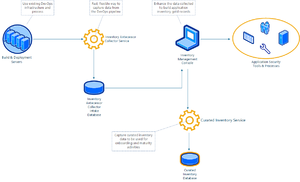
| − | = High Level Design = | + | == High Level Design == |
[[File:Jupiter HLD.png|alt=Jupiter High Level Design|thumb|Jupiter High Level Design]]Jupiter is a microservice-based solution that consists of several components. | [[File:Jupiter HLD.png|alt=Jupiter High Level Design|thumb|Jupiter High Level Design]]Jupiter is a microservice-based solution that consists of several components. | ||