This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Dependency Track Project"
(3.3.1 released) |
m (Jenkins plugin URL change) |
||
| Line 11: | Line 11: | ||
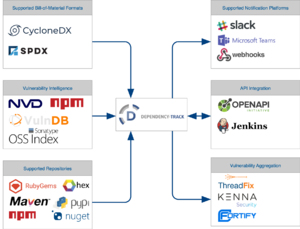
Dependency-Track is a Software Composition Analysis (SCA) platform that keeps track of all third-party components used in all the applications an organization creates or consumes. It integrates with multiple vulnerability databases including the [https://nvd.nist.gov/ National Vulnerability Database] (NVD), [https://www.npmjs.com/advisories NPM Public Advisories], [https://ossindex.sonatype.org/ Sonatype OSS Index], and [https://vulndb.cyberriskanalytics.com VulnDB] from [https://www.riskbasedsecurity.com Risk Based Security]. Dependency-Track monitors all applications in its portfolio in order to proactively identify vulnerabilities in components that are placing your applications at risk. Use of Dependency-Track can play a vital role in an overall [https://csrc.nist.gov/Projects/Supply-Chain-Risk-Management Cyber Supply Chain Risk Management] (C-SCRM) program by fulfilling many of the recommendations laid out by [https://www.safecode.org/wp-content/uploads/2017/05/SAFECode_TPC_Whitepaper.pdf SAFECode]. | Dependency-Track is a Software Composition Analysis (SCA) platform that keeps track of all third-party components used in all the applications an organization creates or consumes. It integrates with multiple vulnerability databases including the [https://nvd.nist.gov/ National Vulnerability Database] (NVD), [https://www.npmjs.com/advisories NPM Public Advisories], [https://ossindex.sonatype.org/ Sonatype OSS Index], and [https://vulndb.cyberriskanalytics.com VulnDB] from [https://www.riskbasedsecurity.com Risk Based Security]. Dependency-Track monitors all applications in its portfolio in order to proactively identify vulnerabilities in components that are placing your applications at risk. Use of Dependency-Track can play a vital role in an overall [https://csrc.nist.gov/Projects/Supply-Chain-Risk-Management Cyber Supply Chain Risk Management] (C-SCRM) program by fulfilling many of the recommendations laid out by [https://www.safecode.org/wp-content/uploads/2017/05/SAFECode_TPC_Whitepaper.pdf SAFECode]. | ||
| − | Dependency-Track is designed to be used in an automated DevOps environment where BoM (bill-of-material) formats are automatically ingested during CI/CD. Use of the [https:// | + | Dependency-Track is designed to be used in an automated DevOps environment where BoM (bill-of-material) formats are automatically ingested during CI/CD. Use of the [https://plugins.jenkins.io/dependency-track Dependency-Track Jenkins Plugin] is highly recommended for this purpose and is well suited for use in Jenkins Pipeline. In such an environment, Dependency-Track enables your DevOps teams to accelerate while still keeping tabs on component usage and any inherited risk. |
Dependency-Track can also be used to monitor vulnerabilities in COTS (commercial off-the-shelf) software. | Dependency-Track can also be used to monitor vulnerabilities in COTS (commercial off-the-shelf) software. | ||
Revision as of 15:03, 16 November 2018
OWASP Dependency-TrackModern applications leverage the availability of existing components for use as building blocks in application development. By using existing components, organizations can dramatically decrease time-to-market. Reusing existing components however, comes at a cost. Organizations that build on top of existing components assume risk for software they did not create. Vulnerabilities in third-party components are inherited by all applications that use those components. The OWASP Top Ten (2013 and 2017) both recognize the risk of using components with known vulnerabilities. Dependency-Track is a Software Composition Analysis (SCA) platform that keeps track of all third-party components used in all the applications an organization creates or consumes. It integrates with multiple vulnerability databases including the National Vulnerability Database (NVD), NPM Public Advisories, Sonatype OSS Index, and VulnDB from Risk Based Security. Dependency-Track monitors all applications in its portfolio in order to proactively identify vulnerabilities in components that are placing your applications at risk. Use of Dependency-Track can play a vital role in an overall Cyber Supply Chain Risk Management (C-SCRM) program by fulfilling many of the recommendations laid out by SAFECode. Dependency-Track is designed to be used in an automated DevOps environment where BoM (bill-of-material) formats are automatically ingested during CI/CD. Use of the Dependency-Track Jenkins Plugin is highly recommended for this purpose and is well suited for use in Jenkins Pipeline. In such an environment, Dependency-Track enables your DevOps teams to accelerate while still keeping tabs on component usage and any inherited risk. Dependency-Track can also be used to monitor vulnerabilities in COTS (commercial off-the-shelf) software. Features
DistributionsDependency-Track supports the following three deployment options:
LicensingOWASP Dependency-Track is licensed under the Apache 2.0 license. |
Quick DownloadReady-to-deploy distributions are available from the Dependency-Track website News and Events
MediaOWASP Dependency-Track Channel (YouTube) DocumentationDependency-Track Documentation Project LeaderRelated ProjectsClassifications
| ||||
This project would not be possible without the existence of the OWASP_Dependency_Check project. Special thanks to Jeremy Long and the Dependency-Check core team for their hard work.
Dependency-Track Core Team
Sponsors
Dependency-Track is created by a worldwide group of volunteers who have dedicated their time, talent, or provided financial support to the project.
The project would like to acknowledge and thank the following organizations that have helped move this project forward
OWASP Dependency-Track is an open source project, created by people who believe that the knowledge of using vulnerable components should be accessible to anyone with a desire to know. By supporting this project, you'll allow the team to outsource testing, infrastructure, further research and development efforts, and engage in outreach to various communities that would benefit from this technology.
Dependency-Track uses GitHub milestones to track roadmaps and future releases.
Feedback from the community is always encouraged. Tell us what you like, what needs to be improved, and what features would be beneficial to your organization.
Three ways to get involved:
- GitHub Issues - Collaborate on open issues
- Gitter - Chatroom built around GitHub
- Slack - The Dependency-Track Slack channel
Pull requests are highly encouraged. No contribution is too small. Do you know how to create test cases? Help us out. Want to write (or correct) some docs? Yes please... All contributions are appreciated.
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||||||