This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Command Injection Defense Cheat Sheet"
(Adding Katy Antons work) |
(→Primary Defenses) |
||
| Line 35: | Line 35: | ||
If there are available libraries or APIs for the language you used, this is the preferred method. | If there are available libraries or APIs for the language you used, this is the preferred method. | ||
| − | === Defense option 2: Parametrization in conjunction with Input Validation === | + | === Defense option 2: Escape values added to OS commands specific to each OS === |
| + | |||
| + | <b>TODO</b> | ||
| + | |||
| + | === Defense option 3: Parametrization in conjunction with Input Validation === | ||
If it is considered unavoidable the call to a system command incorporated with user-supplied, the following two layers of defense should be used within software in order to prevent attacks | If it is considered unavoidable the call to a system command incorporated with user-supplied, the following two layers of defense should be used within software in order to prevent attacks | ||
| Line 47: | Line 51: | ||
^[a-z0-9]{3,10}$ | ^[a-z0-9]{3,10}$ | ||
</pre> | </pre> | ||
| + | |||
== Additional Defenses == | == Additional Defenses == | ||
Revision as of 18:16, 13 November 2017
|
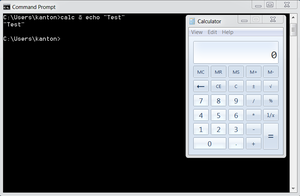
Last revision (08/09/16): 11/13/2017 IntroductionCommand injection (or OS Command Injection) is a type of injection where the software, that constructs a system command using externally influenced input, does not correctly neutralizes the input from special elements that can modify the initially intended command. For example, if the supplied value is: calc when typed in a Windows command prompt, the application “Calculator” is displayed. However, if the supplied value has been tempered with, and now it is: calc & echo “test” when execute, it changes the meaning of the initial intended value. Now, both the “Calculator” application and the value “test” are displayed. The problem is exacerbated if the compromised process does not follow the principle of least privilege principle and attacker-controlled commands end up running with special system privileges that increases the amount of damage.
Primary DefensesDefense Option 1: Avoid calling OS commands directlyThe primary defense is to avoid calling OS commands directly. Built-in library functions are a very good alternative to OS Commands, and they cannot be manipulated to perform tasks other than those it is intended to do. For example use “mkdir()” instead of system(“mkdir /dir_name”). If there are available libraries or APIs for the language you used, this is the preferred method. Defense option 2: Escape values added to OS commands specific to each OSTODO Defense option 3: Parametrization in conjunction with Input ValidationIf it is considered unavoidable the call to a system command incorporated with user-supplied, the following two layers of defense should be used within software in order to prevent attacks
^[a-z0-9]{3,10}$
Additional DefensesLeast privilegeOn top of primary defences, parameterizations and input validation, we also recommend adopting all of these additional defenses in order to provide defense in depth. These additional defenses are:
Code examplesC/C++Use function from exec() family ( execl(), execve(), etc., instead of system(). The exec family of functions does not use a full shell interpreter, so it is not vulnerable to command-injection attacks. JavaIn Java, use ProcessBuilder and the command must be separated from its arguments. Incorrect Usage
ProcessBuilder b = new ProcessBuilder("C:\DoStuff.exe -arg1 -arg2");
In this example, the command together with the arguments are passed as a one string, making easy to manipulate that expression and inject malicious strings. Correct Usage Here is an example that starts a process with a modified working directory. The command and each of the arguments are passed separately. This make it easy to validated each term and reduces the risk to insert malicious strings.
ProcessBuilder pb = new ProcessBuilder("TrustedCmd", "TrustedArg1", "TrustedArg2");
Map<String, String> env = pb.environment();
pb.directory(new File("TrustedDir"));
Process p = pb.start();
PHPIn PHP use escapeshellarg() or escapeshellcmd() rather than exec(), system(), passthru(). Related articlesDescription of Command Injection Vulnerability How to Avoid Vulnerabilities
How to Review Code
How to Test
External References Other Cheatsheets |