This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP ZSC Tool Project"
(→Road Map and Getting Involved) |
Ali Razmjoo (talk | contribs) (Updating) |
||
| Line 7: | Line 7: | ||
| valign="top" style="border-right: 1px dotted gray;padding-right:25px;" | | | valign="top" style="border-right: 1px dotted gray;padding-right:25px;" | | ||
| − | + | ==OWASP ZSC Tool Project== | |
| − | + | ====What is OWASP ZSC ?==== | |
| − | |||
| − | |||
| − | + | '''OWASP ZSC''' is an open source software in python language which lets you generate customized shellcodes for listed operation systems. This software could be run on Linux under python 2.7.x. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
==Description== | ==Description== | ||
| − | + | ====Usage of shellcodes==== | |
| − | |||
| − | |||
| − | + | Shellcodesare small codes in assembly which could be use as the payload in software exploiting. Other usages are in malwares, bypassing antiviruses, obfuscated codes and etc. | |
| − | |||
| − | |||
| − | |||
| − | + | ====Why use OWASP ZSC ?==== | |
| − | |||
| − | + | According to other shellcode generators same as metasploit tools and etc, OWASP ZSC using new encodes and methods which antiviruses won't detect. | |
| + | OWASP ZSC encoderes are able to generate shellcodes with '''random encodes''' and that's lets you to get '''thousands new dynamic shellcodes''' with same job in just a second,that means you will not get a same code if you use random encodes with same commands, And that make OWASP ZSC one of the bests! otherwise it's gonna generate shellcodes for many operation systems in next versions. | ||
| − | + | ==Licensing== | |
| − | + | ====GNU GENERAL PUBLIC LICENSE , Version 3, 29 June 2007==== | |
| − | + | Copyright (C) 2007 Free Software Foundation, Inc. http://fsf.org/ Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed. [https://github.com/Ali-Razmjoo/ZCR-Shellcoder/blob/master/LICENSE.md Click to see the full licensing] | |
| − | |||
| − | |||
| − | |||
| − | |||
'''The OWASP Security Principles are free to use. In fact it is encouraged!!! | '''The OWASP Security Principles are free to use. In fact it is encouraged!!! | ||
| Line 54: | Line 38: | ||
== What is OWASP Security Principles Project? == | == What is OWASP Security Principles Project? == | ||
| − | + | With using '''OWASP ZSC''' you would be able to generate any customized '''Shellcode''' in your mind including encodes in some seconds. <span style="color:#ff0000">goals ...</span> | |
| − | |||
| − | <span style="color:#ff0000"> | ||
| − | |||
| − | </span> | ||
The end goal is to identify, cite, and document the fundamental principles of information security. Once this is well organised, I think it would be great to publish this through the [http://scriptogr.am/dennis-groves/post/owasp-press OWASP Press]. Of course, it will always remain freely available, and any money collected will go directly into the project to absorb costs with any remaining funds going to the OWASP Foundation. | The end goal is to identify, cite, and document the fundamental principles of information security. Once this is well organised, I think it would be great to publish this through the [http://scriptogr.am/dennis-groves/post/owasp-press OWASP Press]. Of course, it will always remain freely available, and any money collected will go directly into the project to absorb costs with any remaining funds going to the OWASP Foundation. | ||
| Line 76: | Line 56: | ||
== Project Leader == | == Project Leader == | ||
| − | + | * [https://www.owasp.org/index.php/User:Ali_Razmjoo Ali Razmjoo] | |
| − | |||
| − | |||
| − | |||
* [https://www.owasp.org/index.php/User:Dennis_Groves Dennis Groves] | * [https://www.owasp.org/index.php/User:Dennis_Groves Dennis Groves] | ||
| Line 85: | Line 62: | ||
== Related Projects == | == Related Projects == | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
* [[OWASP_CISO_Survey]] | * [[OWASP_CISO_Survey]] | ||
| Line 101: | Line 73: | ||
== Quick Download == | == Quick Download == | ||
| − | + | [https://github.com/Ali-Razmjoo/ZCR-Shellcoder/ Github Page.] | |
| − | + | [http://zsc.z3r0d4y.com/download/ Download Page.] | |
| − | |||
| − | |||
| − | |||
The home of the OWASP Security Principles is on [https://github.com/OWASP/Security-Principles GitHub.] You are encourged to fork, edit and push your changes back to the project through git or edit the project directly on github. | The home of the OWASP Security Principles is on [https://github.com/OWASP/Security-Principles GitHub.] You are encourged to fork, edit and push your changes back to the project through git or edit the project directly on github. | ||
However, if you like you may also download the master repository from the following links: | However, if you like you may also download the master repository from the following links: | ||
| − | * [https://github.com/ | + | * [https://github.com/Ali-Razmjoo/ZCR-Shellcoder/zipball/master .zip file.] |
| − | * [https://github.com/ | + | * [https://github.com/Ali-Razmjoo/ZCR-Shellcoder/tarball/master .tgz file.] |
== News and Events == | == News and Events == | ||
| − | + | * [28 July 2015] [http://zsc.z3r0d4y.com/ OWASP ZSC Version 1.0.5.1 Released!] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== In Print == | == In Print == | ||
| Line 155: | Line 118: | ||
=FAQs= | =FAQs= | ||
| − | < | + | To see full guides please visit our [http://zsc.z3r0d4y.com/wiki wiki page]. |
| − | + | ||
| − | + | ====Help Menu==== | |
| − | </ | + | <pre><nowiki> |
| + | Switches: | ||
| + | -h, --h, -help, --help => to see this help guide | ||
| + | -os => choose your os to create shellcode | ||
| + | -oslist => list os for switch -os | ||
| + | -o => output filename | ||
| + | -job => what shellcode gonna do for you ? | ||
| + | -joblist => list of -job switch | ||
| + | -encode => generate shellcode with encode | ||
| + | -types => types of encode for -encode switch | ||
| + | -wizard => wizard mod | ||
| + | |||
| + | -update => check for update | ||
| + | -about => about software and developers.</nowiki></pre> | ||
| + | |||
=Requirement / Installation= | =Requirement / Installation= | ||
| − | |||
| − | |||
'''Installation''' | '''Installation''' | ||
| + | Go to download page, and download last version in github. Extract and run installer.py, then you are able to run software with OWASP ZSC command or you can directly execute zsc.py without installing it.or you can follow these commands to install the last version: | ||
| + | |||
| + | <pre><nowiki>wget https://github.com/Ali-Razmjoo/ZCR-Shellcoder/archive/master.zip -O zcr-shellcoder.zip && unzip zcr-shellcoder.zip && | ||
| + | rm -rf zcr-shellcoder.zip && mv ZCR-Shellcoder-master ZCR-Shellcoder && cd ZCR-Shellcoder && python installer.py</nowiki></pre> | ||
| + | |||
| + | |||
| + | http://zsc.z3r0d4y.com/images/Snapshot_2015-07-27_114843.png | ||
| + | |||
| + | |||
| + | '''Note''': Software could be '''uninstall''' with executing '''uninstaller.py''' | ||
| + | |||
| + | '''Note''': Software installation directory is "'''/usr/share/zcr-shellcoder'''" | ||
| − | |||
| − | |||
==How can I participate in your project?== | ==How can I participate in your project?== | ||
| − | + | ===Be an OWASP ZSC developer=== | |
| − | + | To join us for developing ZCR Shellcoder, you may need to know Assembly, Shellcoding, Python. Then check up this [http://zsc.z3r0d4y.com/table.html Table] and build a shellcode generator with python which we didn’t made it yet, then send it to us and after checking and testing your code, You will became an OWASP ZSC developer and your code will add to software in next versions. | |
| − | + | ||
| + | Also please visit [http://zsc.z3r0d4y.com/developers/ Developer Pages.] | ||
| + | |||
| + | http://zsc.z3r0d4y.com/images/Snapshot_2015-07-27_135930.png | ||
= Acknowledgements = | = Acknowledgements = | ||
==Contributors== | ==Contributors== | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
The OWASP Security Principles project is developed by a worldwide team of volunteers. A live update of project [https://github.com/OWASP/Security-Principles/graphs/contributors contributors is found here]. | The OWASP Security Principles project is developed by a worldwide team of volunteers. A live update of project [https://github.com/OWASP/Security-Principles/graphs/contributors contributors is found here]. | ||
| Line 194: | Line 175: | ||
* [https://github.com/sublimino Andrew Martin] | * [https://github.com/sublimino Andrew Martin] | ||
* [https://github.com/Lambdanaut Josh Thomas] | * [https://github.com/Lambdanaut Josh Thomas] | ||
| − | * | + | * [https://www.owasp.org/index.php/User:Ali_Razmjoo Ali Razmjoo] |
= Road Map and Getting Involved = | = Road Map and Getting Involved = | ||
As I said before, I started project some month ago without OWASP Brand, and More project details is available on website : http://zsc.z3r0d4y.com/ | As I said before, I started project some month ago without OWASP Brand, and More project details is available on website : http://zsc.z3r0d4y.com/ | ||
| − | What is ZSC ? | + | What is OWASP ZSC ? |
ZeroDay Cyber Research Shellcoder [Generator] is an open source software in python language which lets you generate customized shellcodes for listed operation systems. This software can be run on Linux under python 2.7.x. | ZeroDay Cyber Research Shellcoder [Generator] is an open source software in python language which lets you generate customized shellcodes for listed operation systems. This software can be run on Linux under python 2.7.x. | ||
| Line 205: | Line 186: | ||
Shellcodesare small codes in assembly which could be use as the payload in software exploiting. Other usages are in malwares, bypassing antiviruses, obfuscated codes and etc. | Shellcodesare small codes in assembly which could be use as the payload in software exploiting. Other usages are in malwares, bypassing antiviruses, obfuscated codes and etc. | ||
| − | Why use ZSC ? | + | Why use OWASP ZSC ? |
| − | According to other shellcode generators same as metasploit tools and etc, ZSC using new encodes and methods which antiviruses won't detect. | + | According to other shellcode generators same as metasploit tools and etc, OWASP ZSC using new encodes and methods which antiviruses won't detect. |
| − | ZSC encoderes are able to generate shellcodes with random encodes and that's lets you to get thousands new dynamic shellcodes with same job in just a second,that means you will not get a same code if you use random encodes with same commands, And that make ZSC one of the bests! otherwise it's gonna generate shellcodes for many operation systems in next versions. | + | OWASP ZSC encoderes are able to generate shellcodes with random encodes and that's lets you to get thousands new dynamic shellcodes with same job in just a second,that means you will not get a same code if you use random encodes with same commands, And that make OWASP ZSC one of the bests! otherwise it's gonna generate shellcodes for many operation systems in next versions. |
Project features: http://zsc.z3r0d4y.com/table.html | Project features: http://zsc.z3r0d4y.com/table.html | ||
Revision as of 06:32, 5 August 2015
OWASP ZSC Tool ProjectWhat is OWASP ZSC ?OWASP ZSC is an open source software in python language which lets you generate customized shellcodes for listed operation systems. This software could be run on Linux under python 2.7.x. DescriptionUsage of shellcodesShellcodesare small codes in assembly which could be use as the payload in software exploiting. Other usages are in malwares, bypassing antiviruses, obfuscated codes and etc. Why use OWASP ZSC ?According to other shellcode generators same as metasploit tools and etc, OWASP ZSC using new encodes and methods which antiviruses won't detect. OWASP ZSC encoderes are able to generate shellcodes with random encodes and that's lets you to get thousands new dynamic shellcodes with same job in just a second,that means you will not get a same code if you use random encodes with same commands, And that make OWASP ZSC one of the bests! otherwise it's gonna generate shellcodes for many operation systems in next versions. LicensingGNU GENERAL PUBLIC LICENSE , Version 3, 29 June 2007Copyright (C) 2007 Free Software Foundation, Inc. http://fsf.org/ Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed. Click to see the full licensing
The OWASP Security Principles are licensed under the http://creativecommons.org/licenses/by-sa/3.0/ Creative Commons Attribution-ShareAlike 3.0 license], so you can copy, distribute and transmit the work, and you can adapt it, and use it commercially, but all provided that you attribute the work and if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one. |
What is OWASP Security Principles Project?With using OWASP ZSC you would be able to generate any customized Shellcode in your mind including encodes in some seconds. goals ... The end goal is to identify, cite, and document the fundamental principles of information security. Once this is well organised, I think it would be great to publish this through the OWASP Press. Of course, it will always remain freely available, and any money collected will go directly into the project to absorb costs with any remaining funds going to the OWASP Foundation. This document should serve as a guide to technical architects and designers outlining the fundamental principles of security. PresentationThis is where you can link to slide presentations related to your project.
Project Leader
Related ProjectsOpenhub |
Quick DownloadThe home of the OWASP Security Principles is on GitHub. You are encourged to fork, edit and push your changes back to the project through git or edit the project directly on github. However, if you like you may also download the master repository from the following links: News and Events
In PrintThis is where you place links to where your project product can be downloaded or purchased, in the case of a book. This project can be purchased as a print on demand book from Lulu.com ClassificationsHere is where you can let the community know what project stage your project is currently in, whether the project is a builder, breaker, or defender project, and what type of project you are running.
| |||||||
To see full guides please visit our wiki page.
Help Menu
Switches: -h, --h, -help, --help => to see this help guide -os => choose your os to create shellcode -oslist => list os for switch -os -o => output filename -job => what shellcode gonna do for you ? -joblist => list of -job switch -encode => generate shellcode with encode -types => types of encode for -encode switch -wizard => wizard mod -update => check for update -about => about software and developers.
Installation Go to download page, and download last version in github. Extract and run installer.py, then you are able to run software with OWASP ZSC command or you can directly execute zsc.py without installing it.or you can follow these commands to install the last version:
wget https://github.com/Ali-Razmjoo/ZCR-Shellcoder/archive/master.zip -O zcr-shellcoder.zip && unzip zcr-shellcoder.zip && rm -rf zcr-shellcoder.zip && mv ZCR-Shellcoder-master ZCR-Shellcoder && cd ZCR-Shellcoder && python installer.py
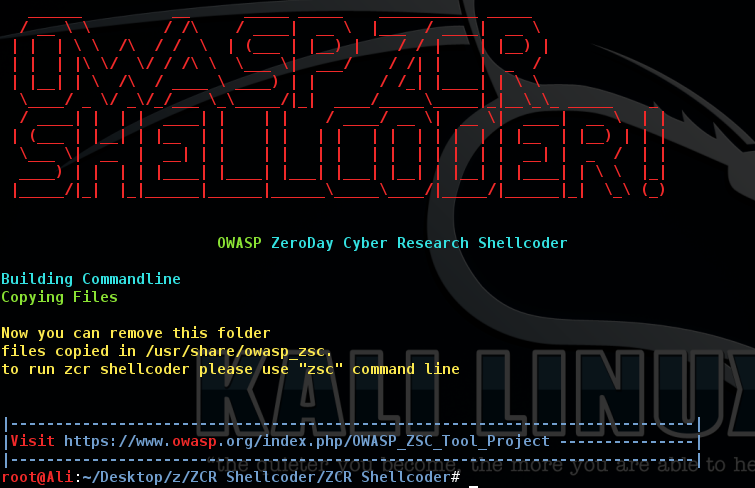
Note: Software could be uninstall with executing uninstaller.py
Note: Software installation directory is "/usr/share/zcr-shellcoder"
How can I participate in your project?
Be an OWASP ZSC developer
To join us for developing ZCR Shellcoder, you may need to know Assembly, Shellcoding, Python. Then check up this Table and build a shellcode generator with python which we didn’t made it yet, then send it to us and after checking and testing your code, You will became an OWASP ZSC developer and your code will add to software in next versions.
Also please visit Developer Pages.
Contributors
The OWASP Security Principles project is developed by a worldwide team of volunteers. A live update of project contributors is found here.
The first contributors to the project were:
As I said before, I started project some month ago without OWASP Brand, and More project details is available on website : http://zsc.z3r0d4y.com/
What is OWASP ZSC ? ZeroDay Cyber Research Shellcoder [Generator] is an open source software in python language which lets you generate customized shellcodes for listed operation systems. This software can be run on Linux under python 2.7.x.
Usage of shellcodes Shellcodesare small codes in assembly which could be use as the payload in software exploiting. Other usages are in malwares, bypassing antiviruses, obfuscated codes and etc.
Why use OWASP ZSC ? According to other shellcode generators same as metasploit tools and etc, OWASP ZSC using new encodes and methods which antiviruses won't detect. OWASP ZSC encoderes are able to generate shellcodes with random encodes and that's lets you to get thousands new dynamic shellcodes with same job in just a second,that means you will not get a same code if you use random encodes with same commands, And that make OWASP ZSC one of the bests! otherwise it's gonna generate shellcodes for many operation systems in next versions.
Project features: http://zsc.z3r0d4y.com/table.html
A project roadmap is the envisioned plan for the project. The purpose of the roadmap is to help others understand where the project is going. It gives the community a chance to understand the context and the vision for the goal of the project. Additionally, if a project becomes inactive, or if the project is abandoned, a roadmap can help ensure a project can be adopted and continued under new leadership.
Roadmaps vary in detail from a broad outline to a fully detailed project charter. Generally speaking, projects with detailed roadmaps have tended to develop into successful projects. Some details that leaders may consider placing in the roadmap include: envisioned milestones, planned feature enhancements, essential conditions, project assumptions, development timelines, etc. You are required to have at least 4 milestones for every year the project is active.
As of October 2013, the priorities are:
- Finish the referencing for each principle.
- Update the Project Template.
- Use the OWASP Press to develop a book.
- Finish and publish the book on Lulu.
Involvement in the development and promotion of the OWASP Security Principles Project is actively encouraged! You do not have to be a security expert in order to contribute. Some of the ways you can help:
- Helping find references to some of the principles.
- Project administration support.
- Wiki editing support.
- Writing support for the book.



