This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Code Pulse Project"
| Line 33: | Line 33: | ||
== News and Events == | == News and Events == | ||
| + | * <span style="background: #66CCFF; font-size:85%;padding:2px;">26 Feb 2015</span> [https://github.com/secdec/codepulse/releases/tag/v1.1.2 Version 1.1.2 is out!] | ||
* <span style="background: #66CCFF; font-size:85%;padding:2px;">28 May 2014</span> [https://github.com/secdec/codepulse/releases/tag/v1.1.1 Version 1.1 is out!] | * <span style="background: #66CCFF; font-size:85%;padding:2px;">28 May 2014</span> [https://github.com/secdec/codepulse/releases/tag/v1.1.1 Version 1.1 is out!] | ||
* <span style="background: #66CCFF; font-size:85%;padding:2px;">14 May 2014</span> [https://github.com/secdec/codepulse/releases/tag/v1.0.1 Version 1.0.1 is out!] | * <span style="background: #66CCFF; font-size:85%;padding:2px;">14 May 2014</span> [https://github.com/secdec/codepulse/releases/tag/v1.0.1 Version 1.0.1 is out!] | ||
| − | |||
== Contact Us == | == Contact Us == | ||
Revision as of 03:42, 27 February 2015
About Code PulseThe OWASP Code Pulse Project is a tool that provides insight into the real-time code coverage of black box testing activities. It is a cross-platform desktop application that runs on most major platforms.
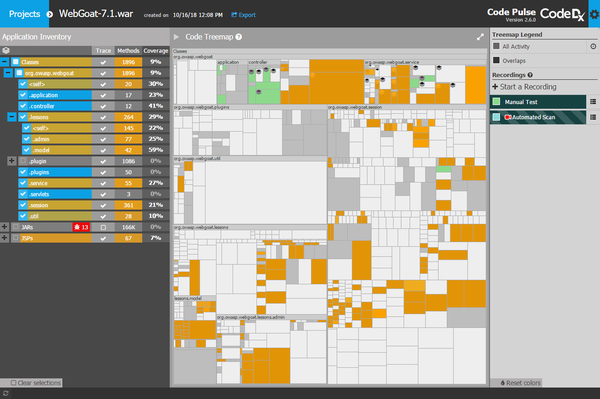
How it worksCode Pulse does its magic by monitoring the runtime of the target application using an agent-based approach that sits deep in the stack of the virtual machine executing the application’s binaries. Due to the intimate nature of our tracing approach we currently support Java Virtual Machines, but we do have plans to add support for .NET applications. Although Code Pulse will likely also work for desktop applications, our current focus is in providing the best experience for web application testing. Why Code Pulse?Whereas in the past it’s been very difficult to understand which parts of an application a DAST or manual penetration test covered, Code Pulse automatically detects the coverage information while the tests are being conducted and will even make it possible to understand the overlaps and boundaries of the different tools’ coverage. Code Pulse presents the coverage information in a visual form to make it easy to understand at-a-glance which parts of an application have been covered, and how much. The real-time coverage feedback makes it easy to adjust testing activity based on the observed coverage. In addition for testing activities relying on multiple techniques (a variety of dynamic analysis tools for instance) it’s fairly easy to split up the recorded activity to understand which code was covered by each tool independently or alternatively to view where the coverage overlaps between multiple tools. LicensingOWASP Code Pulse project is free to use. It is licensed under the Apache 2.0 License. |
Quick LinksNews and Events
Contact UsRelated ProjectsClassifications
| |||||||
The initial version of Code Pulse, version 1.0, was released in early May 2014. Since then we've pushed out version 1.1 to tweak address a number of usability issues and integrate with OWASP Dependency Check.
Long-term there are a number of things on our roadmap that we’d like to add to Code Pulse. The following is a partial list of features we’d like to add to Code Pulse as we continue development on it: - .NET support - Performance improvements - Block level coverage instead of the current method level support - Reporting - Trace playback to see the sequence of the coverage as opposed to just seeing the end state - ZAP integration
Involvement in the development and promotion of Code Pulse is actively encouraged! You do not have to be a security expert in order to contribute.
Some of the ways you can help:
- Code contributions
- Testing
- Wiki documentation
- Spreading the word about the project!
Visit the Code Pulse GitHub project page to see the source.
Code Pulse is maintained and developed by Secure Decisions.
Code Pulse is based on research sponsored by the Department of Homeland Security (DHS) Science and Technology Directorate, Cyber Security Division (DHS S&T/CSD), BAA via contract number FA8750-12-C-0219. The views and conclusions contained herein are those of the authors and should not be interpreted as necessarily representing the official policies or endorsements, either expressed or implied, of Department of Homeland Security or the U.S. Government.