This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Dependency Track Project"
| Line 1: | Line 1: | ||
=Main= | =Main= | ||
| − | + | ||
| − | <div style="width:100%;height:160px;border:0,margin:0;overflow: hidden;">[[File: | + | <div style="width:100%;height:160px;border:0,margin:0;overflow: hidden;">[[File:OWASP_Project_Header.jpg|link=]]</div> |
| − | |||
{| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | {| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | ||
| Line 8: | Line 7: | ||
==OWASP Dependency-Track== | ==OWASP Dependency-Track== | ||
| + | |||
OWASP Dependency-Track is a Java web application that allows organizations to document the use of third-party components across multiple applications and versions. | OWASP Dependency-Track is a Java web application that allows organizations to document the use of third-party components across multiple applications and versions. | ||
==Introduction== | ==Introduction== | ||
| + | |||
Over the last several years, organizations have faced a growing trend on the number of vulnerabilities reported due to the use of vulnerable third-party components. The risk involved in using third-party components is described in a paper by Jeff Williams and Arshan Dabirsiaghi titled, "[https://www.aspectsecurity.com/uploads/downloads/2012/03/Aspect-Security-The-Unfortunate-Reality-of-Insecure-Libraries.pdf The Unfortunate Reality of Insecure Libraries]". This upward trend propelled the use of third-party components into a new category in the [https://www.owasp.org/index.php/Top_10_2013 OWASP Top Ten], specifically, [https://www.owasp.org/index.php/Top_10_2013-A9-Using_Components_with_Known_Vulnerabilities A9: Using Components with Known Vulnerabilities]. | Over the last several years, organizations have faced a growing trend on the number of vulnerabilities reported due to the use of vulnerable third-party components. The risk involved in using third-party components is described in a paper by Jeff Williams and Arshan Dabirsiaghi titled, "[https://www.aspectsecurity.com/uploads/downloads/2012/03/Aspect-Security-The-Unfortunate-Reality-of-Insecure-Libraries.pdf The Unfortunate Reality of Insecure Libraries]". This upward trend propelled the use of third-party components into a new category in the [https://www.owasp.org/index.php/Top_10_2013 OWASP Top Ten], specifically, [https://www.owasp.org/index.php/Top_10_2013-A9-Using_Components_with_Known_Vulnerabilities A9: Using Components with Known Vulnerabilities]. | ||
| − | == | + | ==Description== |
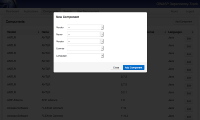
Dependency-Track's first goal is to document the use of third-party components across multiple applications and versions. Organizations can document the usage of components including vendors, libraries, versions and licenses. Many organizations have legal or new product introduction requirements that require software engineering teams to provide documentation on the use of third-party components. Dependency-Track aims to meet this requirement. | Dependency-Track's first goal is to document the use of third-party components across multiple applications and versions. Organizations can document the usage of components including vendors, libraries, versions and licenses. Many organizations have legal or new product introduction requirements that require software engineering teams to provide documentation on the use of third-party components. Dependency-Track aims to meet this requirement. | ||
| − | == | + | ==Licensing== |
| − | + | OWASP Dependency-Track is licensed under the [http://www.gnu.org/licenses/gpl-3.0.txt GPLv3]. | |
| + | |||
| − | | valign="top" style="padding-left:25px;width: | + | | valign="top" style="padding-left:25px;width:200px;border-right: 1px dotted gray;padding-right:25px;" | |
== Features == | == Features == | ||
| − | |||
| − | |||
* Hierarchical view of applications and associated versions | * Hierarchical view of applications and associated versions | ||
| Line 31: | Line 31: | ||
* Centralized distribution of Dependency-Check data | * Centralized distribution of Dependency-Check data | ||
* LDAP integration | * LDAP integration | ||
| − | |||
| + | == Presentation == | ||
| + | |||
| + | Coming soon | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | == Download == | + | == Project Leader == |
| + | |||
| + | Steve Springett | ||
| + | |||
| + | |||
| + | == Related Projects == | ||
| + | |||
| + | * [[OWASP_Dependency_Check]] | ||
| + | |||
| + | |||
| + | |||
| + | | valign="top" style="padding-left:25px;width:200px;" | | ||
| + | |||
| + | == Quick Download == | ||
| + | |||
Dependency-Track is packaged as a Java Web Application Archive (WAR). | Dependency-Track is packaged as a Java Web Application Archive (WAR). | ||
| + | Downloads will be available Q2 2014 | ||
| + | |||
| + | * [https://github.com/stevespringett/dependency-track Source Code] | ||
| − | |||
| − | |||
| + | == News and Events == | ||
| + | * [1 Feb 2014] Testing | ||
| + | |||
| + | ==Classifications== | ||
| + | |||
| + | {| width="200" cellpadding="2" | ||
| + | |- | ||
| + | | align="center" valign="top" width="50%" rowspan="2"| [[File:Owasp-incubator-trans-85.png|link=https://www.owasp.org/index.php/OWASP_Project_Stages#tab=Incubator_Projects]] | ||
| + | | align="center" valign="top" width="50%"| [[File:Owasp-builders-small.png|link=]] | ||
| + | |- | ||
| + | | align="center" valign="top" width="50%"| [[File:Owasp-defenders-small.png|link=]] | ||
| + | |- | ||
| + | | colspan="2" align="center" | [[File:Project_Type_Files_CODE.jpg|link=]] | ||
| + | |} | ||
|} | |} | ||
| + | |||
| + | =FAQs= | ||
| + | |||
| + | ; Q1 | ||
| + | : A1 | ||
| + | |||
| + | ; Q2 | ||
| + | : A2 | ||
| + | |||
=Screenshots= | =Screenshots= | ||
| Line 60: | Line 95: | ||
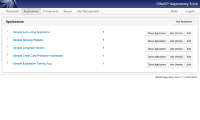
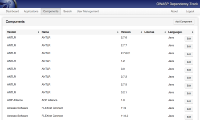
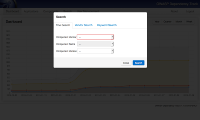
File:Dependency-Track-search-screenshot.png|Search for library usage across all applications | File:Dependency-Track-search-screenshot.png|Search for library usage across all applications | ||
</gallery> | </gallery> | ||
| + | |||
= Acknowledgements = | = Acknowledgements = | ||
| Line 79: | Line 115: | ||
You do not have to be a security expert in order to contribute. | You do not have to be a security expert in order to contribute. | ||
Some of the ways you can help: | Some of the ways you can help: | ||
| + | |||
==Localization== | ==Localization== | ||
Are you fluent in another language? Can you help translate Dependency-Track into that language? | Are you fluent in another language? Can you help translate Dependency-Track into that language? | ||
| + | |||
==Front-End Gurus== | ==Front-End Gurus== | ||
Want to provide design or an implementation for a way to visualize data? There's a lot of potential opportunities in this area. Let us know if you can help. | Want to provide design or an implementation for a way to visualize data? There's a lot of potential opportunities in this area. Let us know if you can help. | ||
| + | |||
==Feedback== | ==Feedback== | ||
Please use the [https://lists.owasp.org/mailman/listinfo/owasp_dependency_track_project Dependency-Track mailing list] for feedback: | Please use the [https://lists.owasp.org/mailman/listinfo/owasp_dependency_track_project Dependency-Track mailing list] for feedback: | ||
| Line 89: | Line 128: | ||
* What could be improved? | * What could be improved? | ||
| − | = About | + | |
| + | =Project About= | ||
{{:Projects/OWASP_Dependency_Track_Project | Project About}} | {{:Projects/OWASP_Dependency_Track_Project | Project About}} | ||
__NOTOC__ <headertabs /> | __NOTOC__ <headertabs /> | ||
| − | [[Category:OWASP Project]] [[Category:OWASP_Builders]] [[Category: | + | [[Category:OWASP Project]] [[Category:OWASP_Builders]] [[Category:OWASP_Defenders]] [[Category:OWASP_Document]] |
Revision as of 00:55, 1 February 2014
OWASP Dependency-TrackOWASP Dependency-Track is a Java web application that allows organizations to document the use of third-party components across multiple applications and versions. IntroductionOver the last several years, organizations have faced a growing trend on the number of vulnerabilities reported due to the use of vulnerable third-party components. The risk involved in using third-party components is described in a paper by Jeff Williams and Arshan Dabirsiaghi titled, "The Unfortunate Reality of Insecure Libraries". This upward trend propelled the use of third-party components into a new category in the OWASP Top Ten, specifically, A9: Using Components with Known Vulnerabilities. DescriptionDependency-Track's first goal is to document the use of third-party components across multiple applications and versions. Organizations can document the usage of components including vendors, libraries, versions and licenses. Many organizations have legal or new product introduction requirements that require software engineering teams to provide documentation on the use of third-party components. Dependency-Track aims to meet this requirement. LicensingOWASP Dependency-Track is licensed under the GPLv3.
|
Features
PresentationComing soon
Project LeaderSteve Springett
Related Projects
|
Quick DownloadDependency-Track is packaged as a Java Web Application Archive (WAR). Downloads will be available Q2 2014
News and Events
Classifications
| |||||
- Q1
- A1
- Q2
- A2
Sponsors
Development of OWASP Dependency-Track is sponsored by Axway.
As of October 2013, the priorities are:
- Further integrate Dependency-Check into Dependency-Track
- Create dashboard providing at-a-glace visibility into the use of vulnerable components
- Auto-populate Dependency-Track database with library identification from Dependency-Check
- Create scheduler to start Dependency-Check scans
- Update Dependency-Check to use Dependency-Track metadata as the sole source of evidence
- Add support for tracking end-of-life dates
- Translate into other languages
- Promote use of Dependency-Track
Involvement in the development and promotion of Dependency-Track is actively encouraged! You do not have to be a security expert in order to contribute. Some of the ways you can help:
Localization
Are you fluent in another language? Can you help translate Dependency-Track into that language?
Front-End Gurus
Want to provide design or an implementation for a way to visualize data? There's a lot of potential opportunities in this area. Let us know if you can help.
Feedback
Please use the Dependency-Track mailing list for feedback:
- What you like?
- What you don't like?
- What could be improved?
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||||||