This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Top 10 2013-Risk"
From OWASP
| Line 5: | Line 5: | ||
|prev=RN | |prev=RN | ||
}} | }} | ||
| + | |||
| + | [[File:Top_10_2013-appsec-risks.png|750px|center]] | ||
{{Top_10_2010:SubsectionAdvancedTemplate|type={{Top_10_2010:StyleTemplate}}|number=whole|width=100%|year=2013}} | {{Top_10_2010:SubsectionAdvancedTemplate|type={{Top_10_2010:StyleTemplate}}|number=whole|width=100%|year=2013}} | ||
| − | What Are Application Security Risks | + | What Are Application Security Risks |
</td></tr></table> | </td></tr></table> | ||
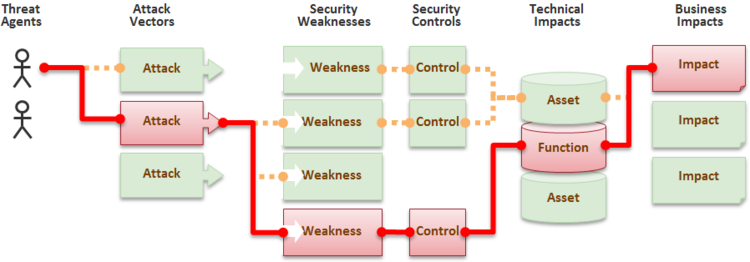
Attackers can potentially use many different paths through your application to do harm to your business or organization. Each of these paths represents a risk that may, or may not, be serious enough to warrant attention. | Attackers can potentially use many different paths through your application to do harm to your business or organization. Each of these paths represents a risk that may, or may not, be serious enough to warrant attention. | ||
Revision as of 17:33, 21 February 2013
NOTE: THIS IS NOT THE LATEST VERSION. Please visit the OWASP Top 10 project page to find the latest edition.
| [[Top 10 {{{year}}}-RN|← RN]] | [[Top_10_{{{year}}}-Top 10|{{{year}}} Top 10 List]] |
[[Top 10 {{{year}}}-T10|T10 →]] |
|
{{{title}}}
What Are Application Security Risks |
Attackers can potentially use many different paths through your application to do harm to your business or organization. Each of these paths represents a risk that may, or may not, be serious enough to warrant attention.
</td></tr></table>
| [[Top 10 {{{year}}}-RN|← RN]] | [[Top_10_{{{year}}}-Top 10|{{{year}}} Top 10 List]] |
[[Top 10 {{{year}}}-T10|T10 →]] |