This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Testing for Web Application Fingerprint (OWASP-IG-004)"
(→Brief Summary) |
|||
| Line 3: | Line 3: | ||
== Brief Summary == | == Brief Summary == | ||
| − | Web server fingerprinting is a critical task for Penetration tester. | + | Web server fingerprinting is a critical task for the Penetration tester. Knowing the version and type of a running web server allows testers to determine known vulnerabilities and the appropriate exploits to use during testing. |
== Black Box testing and example == | == Black Box testing and example == | ||
Revision as of 17:30, 1 December 2006
[Up]
OWASP Testing Guide v2 Table of Contents
Brief Summary
Web server fingerprinting is a critical task for the Penetration tester. Knowing the version and type of a running web server allows testers to determine known vulnerabilities and the appropriate exploits to use during testing.
Black Box testing and example
The simplest and most basic form of identifying a Web server is to look at the Server field in the HTTP response header. For our experiments we use netcat. Consider the following HTTP Request-Response:
$ nc 202.41.76.251 80 HEAD / HTTP/1.0 HTTP/1.1 200 OK Date: Mon, 16 Jun 2003 02:53:29 GMT Server: Apache/1.3.3 (Unix) (Red Hat/Linux) Last-Modified: Wed, 07 Oct 1998 11:18:14 GMT ETag: "1813-49b-361b4df6" Accept-Ranges: bytes Content-Length: 1179 Connection: close Content-Type: text/html $
from the Server field we understand that the server is Apache, version 1.3.3, running on Linux operating system. Three examples of the HTTP response headers are shown below:
From an Apache 1.3.23 server:
HTTP/1.1 200 OK Date: Sun, 15 Jun 2003 17:10: 49 GMT Server: Apache/1.3.23 Last-Modified: Thu, 27 Feb 2003 03:48: 19 GMT ETag: 32417-c4-3e5d8a83 Accept-Ranges: bytes Content-Length: 196 Connection: close Content-Type: text/HTML
From a Microsoft IIS 5.0 server:
HTTP/1.1 200 OK Server: Microsoft-IIS/5.0 Expires: Yours, 17 Jun 2003 01:41: 33 GMT Date: Mon, 16 Jun 2003 01:41: 33 GMT Content-Type: text/HTML Accept-Ranges: bytes Last-Modified: Wed, 28 May 2003 15:32: 21 GMT ETag: b0aac0542e25c31: 89d Content-Length: 7369
From a Netscape Enterprise 4.1 server:
HTTP/1.1 200 OK Server: Netscape-Enterprise/4.1 Date: Mon, 16 Jun 2003 06:19: 04 GMT Content-type: text/HTML Last-modified: Wed, 31 Jul 2002 15:37: 56 GMT Content-length: 57 Accept-ranges: bytes Connection: close
This testing methodology however is not so good. There are several techniques that allow to obfuscate or to modify the server banner string. For example we could obtain the following answer:
403 HTTP/1.1 Forbidden Date: Mon, 16 Jun 2003 02:41: 27 GMT Server: Unknown-Webserver/1.0 Connection: close Content-Type: text/HTML; charset=iso-8859-1
In this case the server field of that response is obfuscated: we cannot know what type of web server is running.
Protocol behaviour
Refined techniques of testing take in consideration various characteristics of the several web servers available on the market. We will list some methodologies that allow us to deduce the type of web server in use.
HTTP header field ordering
The first method consists in observing the ordering of the several headers in the response. Every web server has just an inner ordering of the header. We consider the following answers as an example:
Response from Apache 1.3.23
$ nc apache.example.com 80 HEAD / HTTP/1.0 HTTP/1.1 200 OK Date: Sun, 15 Jun 2003 17:10: 49 GMT Server: Apache/1.3.23 Last-Modified: Thu, 27 Feb 2003 03:48: 19 GMT ETag: 32417-c4-3e5d8a83 Accept-Ranges: bytes Content-Length: 196 Connection: close Content-Type: text/HTML
Response from IIS 5.0
$ nc iis.example.com 80 HEAD / HTTP/1.0 HTTP/1.1 200 OK Server: Microsoft-IIS/5.0 Content-Location: http://iis.example.com/Default.htm Date: Fri, 01 Jan 1999 20:13: 52 GMT Content-Type: text/HTML Accept-Ranges: bytes Last-Modified: Fri, 01 Jan 1999 20:13: 52 GMT ETag: W/e0d362a4c335be1: ae1 Content-Length: 133
Response from Netscape Enterprise 4.1
$ nc netscape.example.com 80 HEAD / HTTP/1.0 HTTP/1.1 200 OK Server: Netscape-Enterprise/4.1 Date: Mon, 16 Jun 2003 06:01: 40 GMT Content-type: text/HTML Last-modified: Wed, 31 Jul 2002 15:37: 56 GMT Content-length: 57 Accept-ranges: bytes Connection: close
We can notice that the ordering of the Date field and the Server field differs between Apache, Netscape Enterprise and IIS.
Malformed requests test
Another useful test to execute consists in sending malformed requests to the server, or requests of nonexistent pages. We consider the following HTTP response:
Response from Apache 1.3.23
$ nc apache.example.com 80 GET / HTTP/3.0 HTTP/1.1 400 Bad Request Date: Sun, 15 Jun 2003 17:12: 37 GMT Server: Apache/1.3.23 Connection: close Transfer: chunked Content-Type: text/HTML; charset=iso-8859-1
Response from IIS 5.0
$ nc iis.example.com 80 GET / HTTP/3.0 HTTP/1.1 200 OK Server: Microsoft-IIS/5.0 Content-Location: http://iis.example.com/Default.htm Date: Fri, 01 Jan 1999 20:14: 02 GMT Content-Type: text/HTML Accept-Ranges: bytes Last-Modified: Fri, 01 Jan 1999 20:14: 02 GMT ETag: W/e0d362a4c335be1: ae1 Content-Length: 133
Response from Netscape Enterprise 4.1
$ nc netscape.example.com 80 GET / HTTP/3.0 HTTP/1.1 505 HTTP Version Not Supported Server: Netscape-Enterprise/4.1 Date: Mon, 16 Jun 2003 06:04: 04 GMT Content-length: 140 Content-type: text/HTML Connection: close
We notice that every server answers in a different way. The answer differs also by the version of the server. An analogous issue comes if we create requests with a not existing protocol. Consider the following responses:
Response from Apache 1.3.23
$ nc apache.example.com 80 GET / JUNK/1.0 HTTP/1.1 200 OK Date: Sun, 15 Jun 2003 17:17: 47 GMT Server: Apache/1.3.23 Last-Modified: Thu, 27 Feb 2003 03:48: 19 GMT ETag: 32417-c4-3e5d8a83 Accept-Ranges: bytes Content-Length: 196 Connection: close Content-Type: text/HTML
Response from IIS 5.0
$ nc iis.example.com 80 GET / JUNK/1.0 HTTP/1.1 400 Bad Request Server: Microsoft-IIS/5.0 Date: Fri, 01 Jan 1999 20:14: 34 GMT Content-Type: text/HTML Content-Length: 87
Response from Netscape Enterprise 4.1
$ nc netscape.example.com 80 GET / JUNK/1.0 <HTML><HEAD><TITLE>Bad request</TITLE></HEAD> <BODY><H1>Bad request</H1> Your browser sent to query this server could not understand. </BODY></HTML>
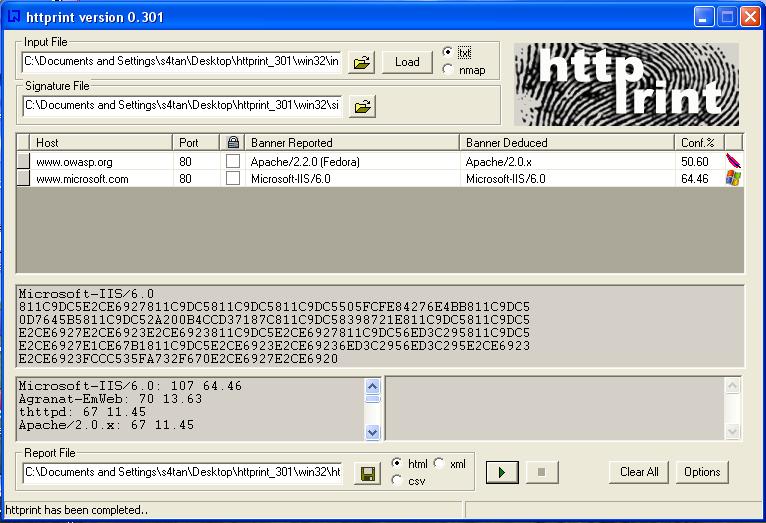
Automated Testing
The tests to carry out can be several. A tool that automates these tests is "httprint" that allows, through a signature dictionary, to recognize the type and the version of the web server in use.
An example of such tool is shown below:
References
Whitepapers
- Saumil Shah: "An Introduction to HTTP fingerprinting" - http://net-square.com/httprint/httprint_paper.html
Tools
- httprint - http://net-square.com/httprint/index.shtml
OWASP Testing Guide v2
Here is the OWASP Testing Guide v2 Table of Contents