This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Template:Application Security News"
From OWASP
| Line 1: | Line 1: | ||
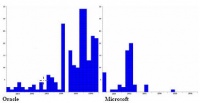
| − | ; '''Nov | + | ; [[Image:Database_security_comparison.jpg|right|200px]]'''Nov 28 - [http://www.databasesecurity.com/dbsec/comparison.pdf Litchfield slams Oracle lack of SDL]''' |
| − | : | + | : David Litchfield presents some very compelling evidence that Microsoft's SDL is paying off. A very interesting read. Not surprisingly, Microsoft is [http://blogs.msdn.com/michael_howard/archive/2006/11/22/microsoft-beats-oracle-in-security-showdown.aspx gloating] a little. |
| − | ; '''Nov | + | ; '''Nov 28 - [http://link Foreign software - threat or xenophobia?]''' |
| − | : " | + | : Ira Winkler - "If there is one line of code written overseas, that’s one line too many. Developing it in the U.S. is not perfect, but we are talking about an exponential increase in risk by moving it overseas." John Pescatore - the focus on offshore developers is "xenophobia" but said the software security concerns raised by the DOD should serve as a useful wake-up call for all organizations that buy software. |
| − | ; '''Nov | + | ; '''Nov 27 - [http://myappsecurity.blogspot.com/2006/11/comparison-between-appscan-vs.html Scanner smackdown results]''' |
| − | : " | + | : "Last month I got a chance to evaluate the two popular vulnerability assessment tools Webinspect and Appscan and I wanted to share my findings with others..." |
| − | ; '''Nov | + | ; '''Nov 27 [http://www.viruslist.com/en/analysis?pubid=204791907 Malware evolution - third wave coming?]''' |
| − | : | + | : "All the events of the third quarter of 2006 lead me to conclude that both the Internet and the field of information security are on the verge of something totally new. I would say that the second stage of both virus and antivirus evolution is now complete. The first stage was during the 1990s, which simple signature detection was enough to combat simple viruses. At this stage, malicious code was not highly technical and did not use complex infection methods." |
| − | ; '''Nov | + | ; '''Nov 26 - [http://www.esecurityplanet.com/print.php/3642321 The security snooze button]''' |
| − | : | + | : Great article by Ken van Wyk. He looks at the 41% increase in published software vulnerabilities and points out that there is not a corresponding 41% increase in the amount of software, a 41% more people looking for vulnerabilities, or more researchers looking. He concludes there's a significant shift in profit motive. Caveat browsor. |
; [[Application Security News|Older news...]] | ; [[Application Security News|Older news...]] | ||
Revision as of 16:21, 28 November 2006
- Nov 28 - Litchfield slams Oracle lack of SDL
- David Litchfield presents some very compelling evidence that Microsoft's SDL is paying off. A very interesting read. Not surprisingly, Microsoft is gloating a little.
- Nov 28 - Foreign software - threat or xenophobia?
- Ira Winkler - "If there is one line of code written overseas, that’s one line too many. Developing it in the U.S. is not perfect, but we are talking about an exponential increase in risk by moving it overseas." John Pescatore - the focus on offshore developers is "xenophobia" but said the software security concerns raised by the DOD should serve as a useful wake-up call for all organizations that buy software.
- Nov 27 - Scanner smackdown results
- "Last month I got a chance to evaluate the two popular vulnerability assessment tools Webinspect and Appscan and I wanted to share my findings with others..."
- Nov 27 Malware evolution - third wave coming?
- "All the events of the third quarter of 2006 lead me to conclude that both the Internet and the field of information security are on the verge of something totally new. I would say that the second stage of both virus and antivirus evolution is now complete. The first stage was during the 1990s, which simple signature detection was enough to combat simple viruses. At this stage, malicious code was not highly technical and did not use complex infection methods."
- Nov 26 - The security snooze button
- Great article by Ken van Wyk. He looks at the 41% increase in published software vulnerabilities and points out that there is not a corresponding 41% increase in the amount of software, a 41% more people looking for vulnerabilities, or more researchers looking. He concludes there's a significant shift in profit motive. Caveat browsor.