This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Category:Interceptor Project"
(→Future Development) |
|||
| Line 56: | Line 56: | ||
== News == | == News == | ||
| − | |||
| − | |||
== Project Contributors == | == Project Contributors == | ||
| − | |||
Revision as of 00:24, 22 November 2006
Overview
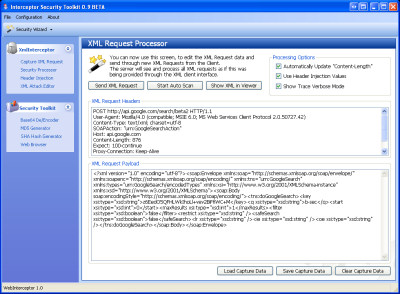
Welcome to the OWASP Interceptor Project for XML Processing. The Interceptor tool is designed to easily assist security testers in performing attacks against XML Web Services and AJAX interfaces. The utility allows testers to capture a sample XML request and then replay/fuzz requests against the Web Service.
A tester can also preload an automated attack database for each request into the tool, and Interceptor will fuzz and replay each attack against the service and provide results.
The Welcome Screen (And Interface) of the Interceptor Project.
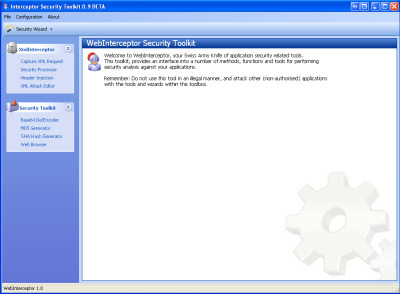
Goals
The Goal of this project was to develop a simple, quick and easy to use tool that could capture and save XML requests and then allow testers to easily replay the request with fuzzed data. Thus allowing the quick testing of the XML Web Service interfaces without the need to use TCP request processors or additional proxies to manipulate and replay handcrafted attack data.
Download
Interceptor 0.9 BETA is currently available for download from OWASP Interceptor 0.9 BETA
Interceptor ZIP includes all the binaries and associated Libraries to run on Windows. The utiltity requires the system to have an installed version of the Microsoft .NET Framework 2.0 installed.
Features
Web Interceptor Functionality (Release 0.9 BETA)
· Capture XML Traffic (via PROXY Configuration)
· Capture XML Traffic (Interception) – In ALPHA Code in release.
· Save, Edit and Replay XML Requests to Web Services
· Configure HTTP Headers (Injection & Manipulation)
· Replay Attacks for Captured XML Data
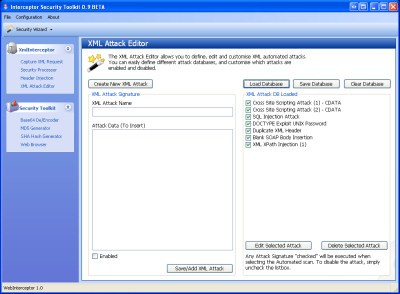
· Create customized XML Attack Signatures and automate XML replay attacks
· BASE 64 Encoding/Decoding
· SHA Hash Generator
· MD5 Hash Generator
· Many more features to come…
Future Development
Currently Interceptor only works in an "Proxy" mode, thus requiring any capture to be configured to proxy through the internal service. This is currently being upgraded so that the tool will sniff the ethernet interfaces and capture XML requests without the need for configuring a proxy connection.
Currently only a few sample XML style attacks exist in the pre-configured database, however we would like to make this attack database (for specific XML attacks) much larger and then make it available on this web site to download.
Other updates and changes to the code will be produced over time. If anyone wants to work on the development please contact the project team.
News
Project Contributors
This category currently contains no pages or media.