This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Static Code Analysis"
| Line 11: | Line 11: | ||
==Description== | ==Description== | ||
| − | Static Code Analysis is usually performed as part of a Code Review (also known as white-box testing) and is carried out at the Implementation phase of a Security Development Lifecycle (SDL). Static Code Analysis commonly refers to the running of Static Code Analysis tools that attempt to highlight possible vulnerabilities within 'static' (non-running) source code by using techniques such as | + | Static Code Analysis is usually performed as part of a Code Review (also known as white-box testing) and is carried out at the Implementation phase of a Security Development Lifecycle (SDL). Static Code Analysis commonly refers to the running of Static Code Analysis tools that attempt to highlight possible vulnerabilities within 'static' (non-running) source code by using techniques such as Taint Analysis and Data Flow Analysis. |
The UK Defense Standard 00-55 requires that Static Code Analysis be used on all 'safety related software in defense equipment'. [0] | The UK Defense Standard 00-55 requires that Static Code Analysis be used on all 'safety related software in defense equipment'. [0] | ||
| Line 17: | Line 17: | ||
==Techniques== | ==Techniques== | ||
There are various techniques to analyze static source code for potential vulnerabilities. | There are various techniques to analyze static source code for potential vulnerabilities. | ||
| − | |||
| − | |||
| − | |||
===Data Flow=== | ===Data Flow=== | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
TBD | TBD | ||
Revision as of 16:22, 5 January 2012
This article is a stub. You can help OWASP by expanding it or discussing it on its Talk page.
Every Control should follow this template.
This is a control. To view all control, please see the Control Category page.
Last revision (mm/dd/yy): 01/5/2012
Description
Static Code Analysis is usually performed as part of a Code Review (also known as white-box testing) and is carried out at the Implementation phase of a Security Development Lifecycle (SDL). Static Code Analysis commonly refers to the running of Static Code Analysis tools that attempt to highlight possible vulnerabilities within 'static' (non-running) source code by using techniques such as Taint Analysis and Data Flow Analysis.
The UK Defense Standard 00-55 requires that Static Code Analysis be used on all 'safety related software in defense equipment'. [0]
Techniques
There are various techniques to analyze static source code for potential vulnerabilities.
Data Flow
TBD
Taint Analysis
TBD
Limitations
TBD
False Positives
TBD
False Negatives
TBD
Examples
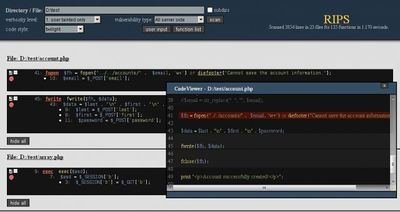
RIPS PHP Static Code Analysis Tool
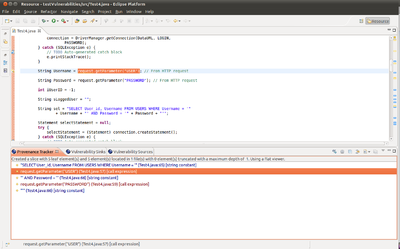
OWASP LAPSE+ Static Code Analysis Tool
Tools
Open Source/Free
- OWASP LAPSE (Java)
- PMD (Java)
- FlawFinder (C/C++)
- Microsoft FxCop (.NET)
- Splint (C)
- FindBugs (Java)
- RIPS (PHP)
- Agnitio (Objective-C, C#, Java & Android)
Commercial
References
[0] Ministry of Defence (MoD). (1997) SAFETY RELATED SOFTWARE IN DEFENSE EQUIPMENT [Online]. Available at: http://www.software-supportability.org/Docs/00-55_Part_2.pdf (Accessed: 5 January 2012).