This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Atlanta Georgia"
(→September 2010 Meeting) |
|||
| Line 35: | Line 35: | ||
== '''Future Meetings''' == | == '''Future Meetings''' == | ||
| − | === | + | ===October 2010 Meeting=== |
'''WHAT::''' September Chapter Meeting | '''WHAT::''' September Chapter Meeting | ||
| − | '''WHEN::''' | + | '''WHEN::''' October 13th 2010 - 7-9PM |
| − | '''WHERE::''' | + | '''WHERE::''' Georgia Tech, Room TBD |
| − | |||
| − | |||
| − | |||
| − | '''WHO::''' ''' | + | '''WHO::''' '''Steve Millar, GTRI''' |
| − | |||
| − | '''ABSTRACT:: ''' | + | Steve Millar is a Senior Research Engineer with the Georgia Tech |
| + | Research Institute (GTRI). He is interested in all things .NET and all | ||
| + | things web so building web tools is a passion that he simply cannot ignore. | ||
| + | Steve is interested in building a high-performance framework for rapidly | ||
| + | constructing any kind of web tool that can be imagined by humans. He is | ||
| + | also keenly interested in building a thriving community around this code and | ||
| + | overall concept. In a former life Steve was the lead architect and SW | ||
| + | development manager for HP's WebInspect product line where he spent a lot of | ||
| + | time obsessing over how to automate web security tasks inside a large, | ||
| + | complex, multi-threaded application. Hopefully he learned enough to help | ||
| + | make this simpler for less obsessed people. Steve also thinks it is strange | ||
| + | to refer to himself in the third person. | ||
| + | |||
| + | |||
| + | |||
| + | '''ABSTRACT:: ''' | ||
| + | |||
| + | Web Security tools are everywhere and they come in multiple flavors from | ||
| + | freely downloadable binaries to open source libraries to commercial | ||
| + | application suites. Unfortunately, they never seem to do exactly what you | ||
| + | need and they are not always easy to extend or configure. Wouldn't it be | ||
| + | nice if the tools were interoperable, easy to construct (think Lego blocks) | ||
| + | and high-performance? Something more useful than just a few Python scripts | ||
| + | and a prayer. Georgia Tech's Cyber Technology and Information Security Lab | ||
| + | is on a mission to provide such a tool framework. | ||
| + | |||
| + | |||
| + | SpiderSense is a .NET code library and suite of tools that enables rapid | ||
| + | development of web security tools and data mining applications. The core | ||
| + | pillars of SpiderSense are a high performance web crawler, a modular and | ||
| + | extensible analysis engine and pluggable content parsers. These modules can | ||
| + | be combined quickly and flexibly to create data gathering and discovery | ||
| + | tools. SpiderSense also enables the crafting of non-standard HTTP payloads | ||
| + | that can be used in automated penetration testing and web-based | ||
| + | exploitation. The framework also uses a plug-in analysis model to allow | ||
| + | experimentation with a broad range of analysis algorithms. If you can do it | ||
| + | with HTTP then you can do it with SpiderSense. | ||
| + | |||
| + | |||
| + | We will show just a few slides just to outline the problem then quickly | ||
| + | dive into SpiderSense starting with demonstrations of a few tools and | ||
| + | finishing with a discussion of architecture, community and the development | ||
| + | roadmap. Hopefully we can get some good brain-storms to occur around the | ||
| + | topics of cool features and ways for the community to contribute. The | ||
| + | speaker also wants to walk away with some great ideas about possible | ||
| + | extensibility points from the audience. Bring your thinking cap and your | ||
| + | good ideas about web tools and we'll roll up our sleeves and talk code! | ||
| − | |||
'''RSVP::''' http://tr.im/owasp_meeting | '''RSVP::''' http://tr.im/owasp_meeting | ||
| − | + | '''''COST''''': Free to everyone | |
---- | ---- | ||
== Past Meetings == | == Past Meetings == | ||
| + | |||
| + | [[Atlanta Member Meeting 09.15.10 | Aug 2010 - Search Engine Hacking]] | ||
[[Atlanta Member Meeting 08.12.10 | Aug 2010 - OWASP Guided Tour & Using the O2 Platform]] | [[Atlanta Member Meeting 08.12.10 | Aug 2010 - OWASP Guided Tour & Using the O2 Platform]] | ||
Revision as of 17:36, 27 September 2010
OWASP Atlanta
Welcome to the Atlanta chapter homepage. Chapter Lead is Tony UV.
Participation
OWASP Foundation (Overview Slides) is a professional association of global members and is open to anyone interested in learning more about software security. Local chapters are run independently and guided by the Chapter_Leader_Handbook. As a 501(c)(3) non-profit professional association your support and sponsorship of any meeting venue and/or refreshments is tax-deductible. Financial contributions should only be made online using the authorized online chapter donation button. To be a SPEAKER at ANY OWASP Chapter in the world simply review the speaker agreement and then contact the local chapter leader with details of what OWASP PROJECT, independent research or related software security topic you would like to present on.
Sponsorship/Membership
![]() to this chapter or become a local chapter supporter.
Or consider the value of Individual, Corporate, or Academic Supporter membership. Ready to become a member?
to this chapter or become a local chapter supporter.
Or consider the value of Individual, Corporate, or Academic Supporter membership. Ready to become a member?
Local News
Our next meeting would be on 15th September where Rob Ragan will present search engine hacking techniques. For more information, click on the Chapter Meetings tab.
On behalf of the chapter, I would like to solicit your financial support of chapter via a tax deductible membership for a great non-profit organization which aims to elevate web application security. Please note that other chapters have the luxury to charge their members for attending some of their meetings. We hope that you find historical and future meetings to be of value and show support via a member based contribution. To contribute to OWASP-Atlanta, go here: <paypal>Atlanta Georgia</paypal>
Staying in Touch
New OWASP Atlanta Linkedin Group. For those addicted to LinkedIn, we have a group you can further feed your addiction. The OWASP Atlanta Chapter. http://www.linkedin.com/groups?home=&gid=1811960&trk=anet_ug_hm
Register for the OWASP Atlanta Mailing List by signing up here: http://lists.owasp.org/mailman/listinfo/owasp-atlanta
OWASP Atlanta Supporters
Thanks to the following list of official sponsors and supportive organizations for their financial contributions and resource support.
2009 OWASP Atlanta Member Survey
The Atlanta OWASP Member Survey has come and gone. Thanks to all those that responded. A subset of the results is shown below in the form of top ranking security topics that members wish to see in 2009. More detailed results will be provided and discussed briefly during our first meeting, April 2nd, 2009. 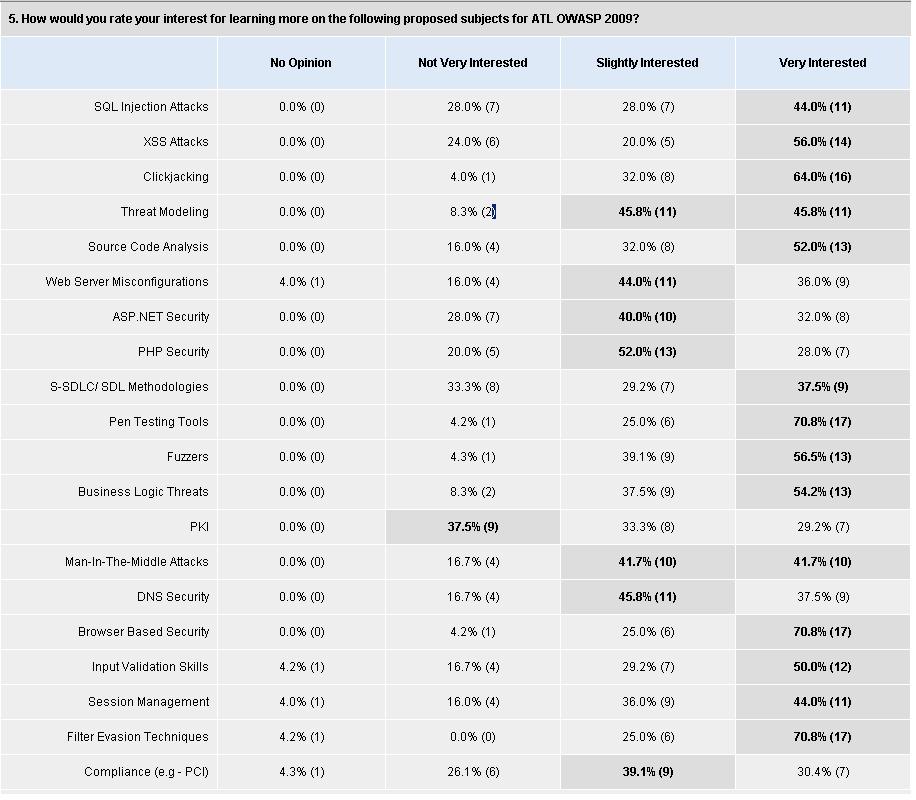
Chapter Meetings
Future Meetings
October 2010 Meeting
WHAT:: September Chapter Meeting
WHEN:: October 13th 2010 - 7-9PM
WHERE:: Georgia Tech, Room TBD
WHO:: Steve Millar, GTRI
Steve Millar is a Senior Research Engineer with the Georgia Tech Research Institute (GTRI). He is interested in all things .NET and all things web so building web tools is a passion that he simply cannot ignore. Steve is interested in building a high-performance framework for rapidly constructing any kind of web tool that can be imagined by humans. He is also keenly interested in building a thriving community around this code and overall concept. In a former life Steve was the lead architect and SW development manager for HP's WebInspect product line where he spent a lot of time obsessing over how to automate web security tasks inside a large, complex, multi-threaded application. Hopefully he learned enough to help make this simpler for less obsessed people. Steve also thinks it is strange to refer to himself in the third person.
ABSTRACT::
Web Security tools are everywhere and they come in multiple flavors from freely downloadable binaries to open source libraries to commercial application suites. Unfortunately, they never seem to do exactly what you need and they are not always easy to extend or configure. Wouldn't it be nice if the tools were interoperable, easy to construct (think Lego blocks) and high-performance? Something more useful than just a few Python scripts and a prayer. Georgia Tech's Cyber Technology and Information Security Lab is on a mission to provide such a tool framework.
SpiderSense is a .NET code library and suite of tools that enables rapid
development of web security tools and data mining applications. The core
pillars of SpiderSense are a high performance web crawler, a modular and
extensible analysis engine and pluggable content parsers. These modules can
be combined quickly and flexibly to create data gathering and discovery
tools. SpiderSense also enables the crafting of non-standard HTTP payloads
that can be used in automated penetration testing and web-based
exploitation. The framework also uses a plug-in analysis model to allow
experimentation with a broad range of analysis algorithms. If you can do it
with HTTP then you can do it with SpiderSense.
We will show just a few slides just to outline the problem then quickly
dive into SpiderSense starting with demonstrations of a few tools and
finishing with a discussion of architecture, community and the development
roadmap. Hopefully we can get some good brain-storms to occur around the
topics of cool features and ways for the community to contribute. The
speaker also wants to walk away with some great ideas about possible
extensibility points from the audience. Bring your thinking cap and your
good ideas about web tools and we'll roll up our sleeves and talk code!
RSVP:: http://tr.im/owasp_meeting
COST: Free to everyone
Past Meetings
Aug 2010 - Search Engine Hacking
Aug 2010 - OWASP Guided Tour & Using the O2 Platform
Jun 2010 - Security Six Flags Outing
May 2010 - Clubbing WebApps with Botnets
Mar 2010 - Panel on Static & Dynamic Analysis for Web Apps
Feb 2010 - Embedded Malicious JavaScript
Oct 2009 - Security Religions & Risk Windows (Jeremiah Grossman)
Sept 2009 - Securing WebServices
June 2009 - OWASP LIVE CD Workshop
Apr 2009 - Filter Evasion Techniques (Workshop)
Apr 2009 - Chapter Rebirth meeting
Atlanta ISACA OWASP Meeting 03.27.09
Atlanta Leadership Meeting 03.05.09
Atlanta Leadership Meeting 02.26.09
Atlanta OWASP May 2007 Meeting
Atlanta OWASP December 06 Social
Chapter Meeting March 29th 2006
April 27th, Chapter meeting a SUCCESS!
Atlanta Georgia OWASP Chapter Leaders
- Tony UcedaVelez - Chapter Lead
- Charles Burke - Meeting Chairperson
- Shauvik Roy Choudhary - Marketing Chairperson


