This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "AppSensor ResponseActions"
(→Overview) |
(→Detailed Listing) |
||
| Line 17: | Line 17: | ||
=Detailed Listing= | =Detailed Listing= | ||
| + | |||
| + | Classifications are: | ||
| + | |||
| + | * Purposes: Logging, Notifying, Disrupting and Blocking | ||
| + | * Target: One, Some or All users | ||
| + | * Response duration: Instantaneous (e.g. just for the request), Period (e.g. time period or session duration), Permanent | ||
==Silent== | ==Silent== | ||
Revision as of 18:04, 27 August 2010
About This Document
These response actions are part of the OWASP AppSensor project which advocates bringing intelligent intrusion detection inside the application. These responses can be used to counter a malicious user that has been detected probing for vulnerabilities or weaknesses within your application.
Overview
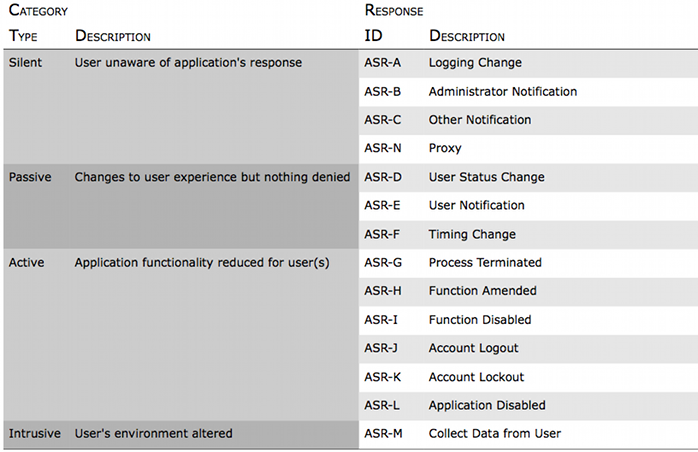
The following table lists possible AppSensor Responses (ASRs). The application response actions are categorized here by:
- Silent: User(s) unaware of any application change
- Passive: Process altered, but user(s) may still continue to process completion
- Active: Functionality reduced or disabled
This table, with examples and alternative classifications, is described in AppSensor - Response Actions (64 KB PDF).
Detailed Listing
Classifications are:
- Purposes: Logging, Notifying, Disrupting and Blocking
- Target: One, Some or All users
- Response duration: Instantaneous (e.g. just for the request), Period (e.g. time period or session duration), Permanent
Silent
ASR-A: Logging Change
| id |
ASR-A |
| title |
Logging Change |
| classifications |
Logging | One, some or all users | Instantaneous (request) or for a period |
| category |
Silent |
| description |
The granularity of logging is changed (typically more logging) |
| consideration | |
| examples |
Example 1: Capture sanitised request headers and response bodies Example 2: Full stack trace of error messages logged Example 3: Record DNS data on user's IP address Example 4: Security logging level changed to include 'informational' messages |
| code |
- |